Phase retrieval algorithm for optical information security
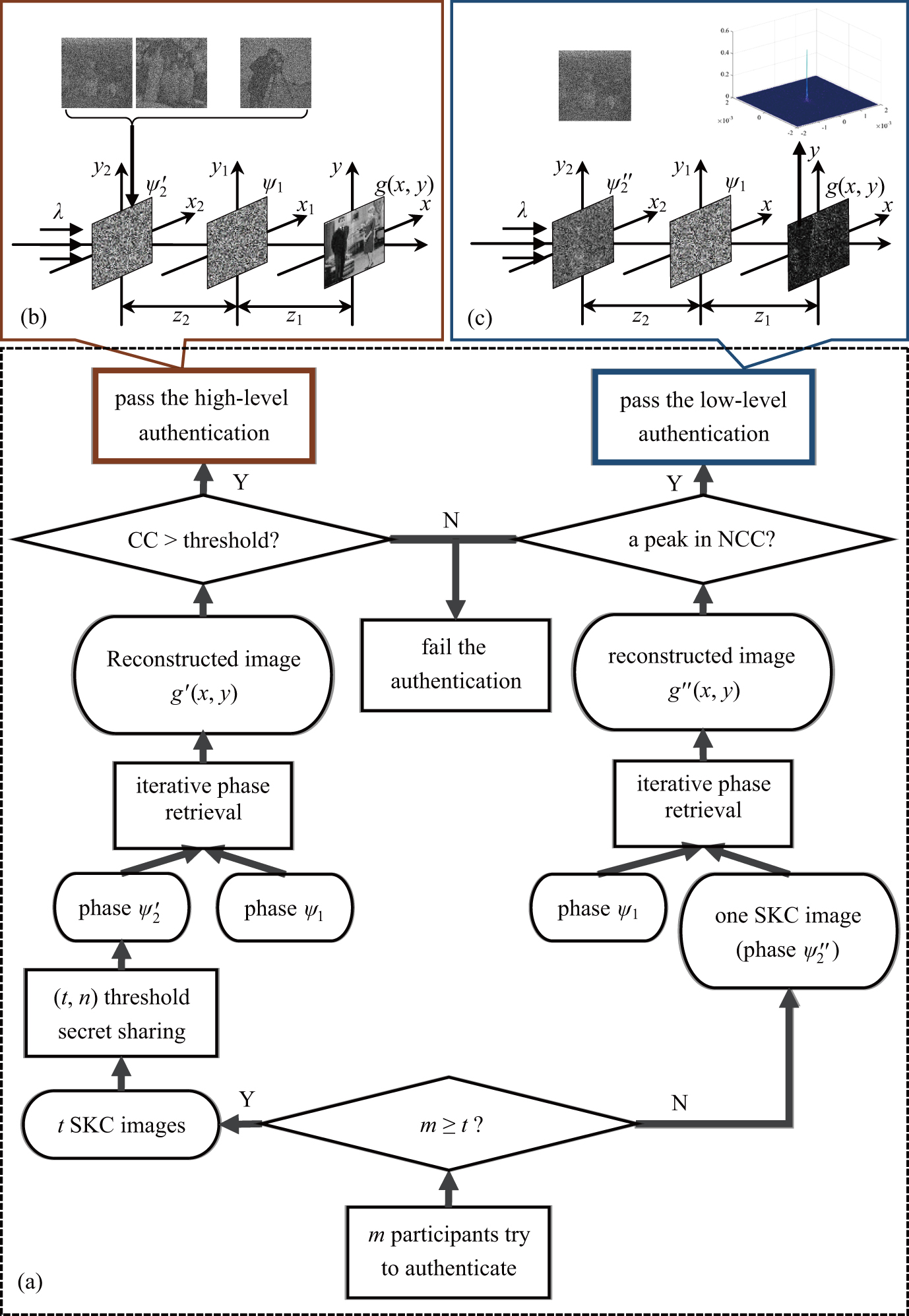
Flow chart of (a) authentication process, (b) high-level authentication process, and (c) low-level authentication process.
Phase retrieval algorithm for optical information security |
|
Flow chart of (a) authentication process, (b) high-level authentication process, and (c) low-level authentication process. |
 |