† Corresponding author. E-mail:
Project supported by the National Natural Science Foundation of China (Grant Nos. 61775121, 61307003, 61405122, and 11574311), Key R&D Program of Shandong Province, China (Grant No. 2018GGX101002), the Natural Science Foundation of Shandong Province, China (Grant No. R2016FM03), and the Fundamental Research Funds of Shandong University, China (Grant No. 2015GN031).
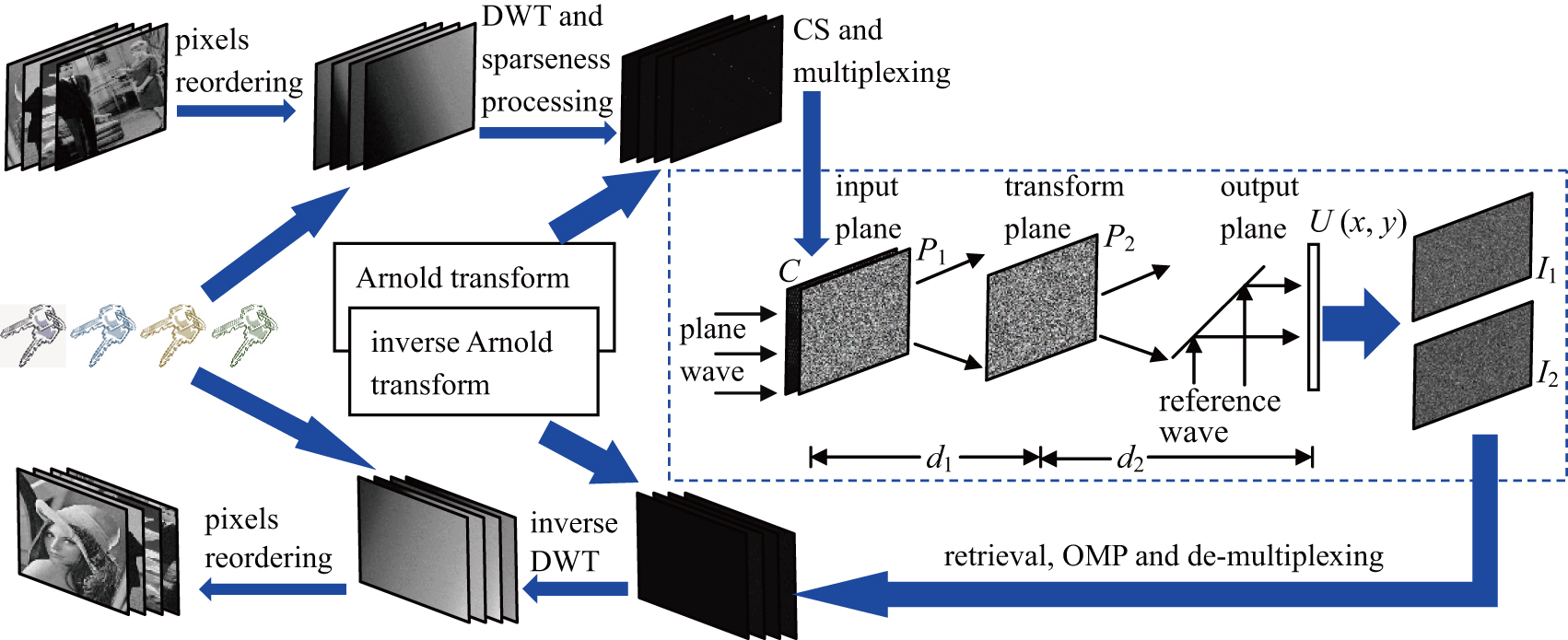
A multiple-image encryption method based on two-step phase-shifting interferometry (PSI) and spatial multiplexing of a smooth compressed signal is proposed. In the encoding and encryption process, with the help of four index matrices to store original pixel positions, all the pixels of four secret images are firstly reordered in an ascending order; then, the four reordered images are transformed by five-order Haar wavelet transform and performed sparseness operation. After Arnold transform and pixels sampling operation, one combined image can be grouped with the aid of compressive sensing (CS) and spatial multiplexing techniques. Finally, putting the combined image at the input plane of the PSI encryption scheme, only two interferograms ciphertexts can be obtained. During the decoding and decryption, utilizing all the secret key groups and index matrices keys, all the original secret images can be successfully decrypted by a wave-front retrieval algorithm of two-step PSI, spatial de-multiplexing, inverse Arnold transform, inverse discrete wavelet transform, and pixels reordering operation.
Information transmission and storage, especially in the age of the internet, is an inevitable part of people’s lives. Meanwhile, an information security technique has emerged to prevent the unauthorized information usurpation. Since Réfrégier and Javidi proposed the double random phase encoding (DRPE) technique in 1995,[1] optical information security techniques have attracted an increasing number of researchers, because of their advantages such as high processing speed, high degree of parallelism, high encryption dimension, fast convolution, correlation operation, etc. Subsequently, some typical optical information processing techniques or transforms,[2] such as fractional Fourier transform,[3,4] digital holography,[5–7] phase retrieval,[8–10] two-beam interference,[11] fractional Mellin transform,[12] gyrator transform,[13] joint transform correlator,[14] jigsaw transform,[15] aperture movement,[16,17] and ghost imaging,[18–22] have been combined with DRPE to build more versatile security cryptosystems.
In 2000, Tajahuerce et al. proposed an optical encryption method of 3D information by DRPE and four-step phase-shifting interferometry (PSI),[23] in which the 3D object information was encrypted with the Fresnel diffraction pattern generated by DRPE, and then electronically recorded by four-step phase-shifting interferometry. Subsequently, three-step PSI was applied to a digital image encryption and watermarking method,[24] in which the secret image encoded by DRPE and Fresnel diffraction can be recorded into three interferograms. To raise the efficiency of encrypted information transmission, we proposed a two-step phase-shifting algorithm in 2006 and then applied it to image encryption,[25] by which an original object complex field can be recorded and reconstructed with only two interferograms.
Compressive sensing (CS) is a newly developed sampling-reconstruction technique that can complete the sampling and compressing simultaneously. This method can reduce the sampling rate, but at the expense of a complex reconstruction on the recipient.[26–30] Because of this unique advantage, CS has been successfully applied to optical information security fields. In 2014, Zhou et al. proposed an image compression-encryption hybrid algorithm with high security based on a key-controlled measurement matrix in CS,[31] in which the circulant matrix was utilized to construct the measurement matrix in CS and control the original row vector of the circulant matrix with a chaos system. Recently, CS has been introduced into the image encryption methods based on DRPE and PSI by Li et al.[32,33]
Besides the optical image encryption methods mentioned above, some pioneers have proposed multiple-image encryption methods based on wavelength multiplexing,[34] position multiplexing,[35] phase-only mask (POM) multiplexing,[36,37] lateral shifting,[38] etc. In 2014, Deepan et al. proposed a multiple-image encryption scheme by spatial multiplexing based on CS and the DRPE,[39] in which a space multiplexing concept was used to exploit the redundant space available due to the compressive sensing process. In 2016, Sui et al. proposed a multiple-image encryption method based on the chaotic structured phase masks under the illumination of a vortex beam in the gyrator domain,[40] in which two structured phase masks were utilized to reconstruct the phase keys by nonlinear iterative phase retrieval algorithm. Based on the modified logistic map algorithm,[41,42] compressive ghost imaging and CS, we recently proposed a multiple-image encryption method,[43] in which after a random phase-only-mask generation[44] by the modified logistic map algorithms, the ciphertext can be acquired by discrete cosine transformation, random sampling and scrambling, the combined image generation, and compressive ghost imaging. At this time, we propose a multiple-image encryption method based on two-step phase-shifting interferometry and spatial multiplexing of smooth compressed signal, aiming to reduce the phase-shifting steps and the data volume of the secret images for n images encryption program, and further enhance the data usage efficiency of interferograms derived from two-step phase-shifting interferometry. The principle and procedure will be described firstly, and then a set of simulations will be given to verify the feasibility and robustness of the scheme, finally a conclusion will be drawn.
In a conventional sampling process, a massive amount of data collected can only be largely discarded at the compression stage to facilitate storage and transmission. This process of massive data acquisition followed by compression is extremely wasteful.[27] The compressive sensing (CS) theory, which combines sampling and compression into a single non-adaptive linear measurement process, can recover certain signals and images from far fewer samples than the Shannon–Nyquist sampling theorem requires, and CS consists of three steps: sparse representation, random projection, and reconstruction.[26–28]
In signal compression theory, any signal that is sparse or sparsifiable can be compressed through a measurement matrix. Taking an N × N real value matrix
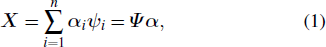 |
Besides the random measurement matrix
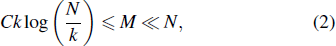 |
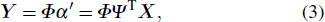 |
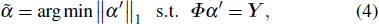 |
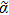
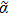
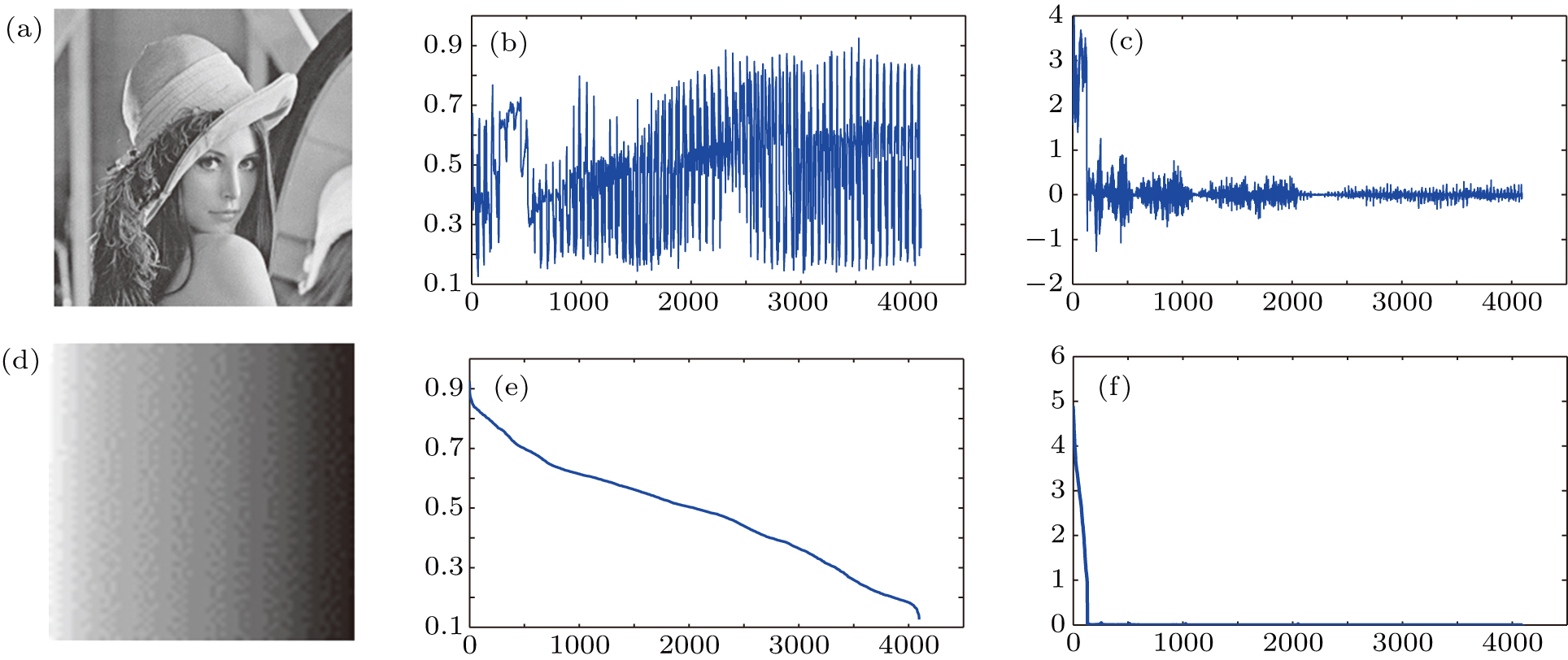
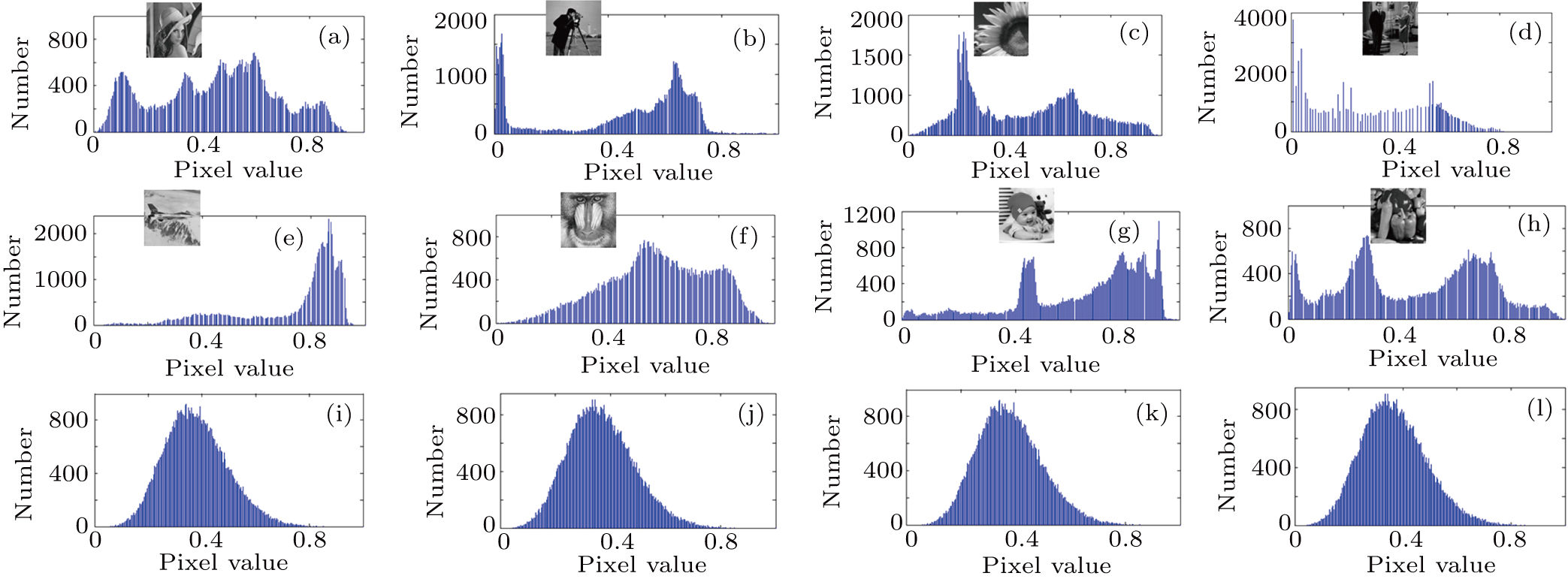
The decay of Fourier or wavelet coefficients of smooth signals exhibits a power law, which means that for the same image, the reordered smooth image performs with a stronger sparse property than the original image in the Fourier or wavelet domain.[50] Inspired by this thought, prior to compression, we reorder the pixels in ascending/descending order to lower the inherent frequency of the original image. For a further step, the simulated results are also presented and listed in Fig.
For simplicity, as depicted in the encryption part shown in Fig.
In the two-step PSI encryption system shown in Fig.
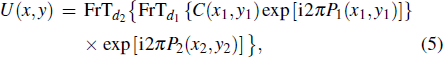 |
On the reference wave arm, the phase
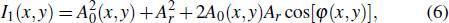 |
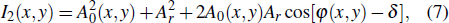 |
The decryption process will occur when the Useri enters the cryptosystem with his/her secret key group SGi. As the decryption part illustrates in Fig.
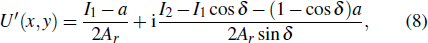 |
 |
 |
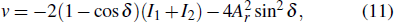 |
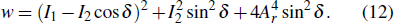 |
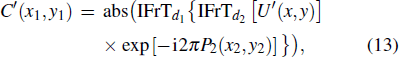 |
It is not until the authorized Useri is able to get the exclusive module Yi (i = 1, 2, 3, 4) consisting in C′ from top to bottom that he/she can obtain correct decrypted images through the next decryption work. After the OMP reconstruction algorithm and inverse Arnold transform, four K-sparse images are recovered; then taking the inverse DWT operator followed by reordering in the index matrix ( SK1, SK2, SK3, and SK4) order, all the original secret images can be decrypted.
Correlation coefficient (CC),[51,52] normalized cross correlation (NCC),[53] structural similarity index metric (SSIM), and mean square error (MSE) are adopted as objective criterions to evaluate the image quality between the recovered and the original secret image.
A series of simulations have been carried out using MATLAB R2014a to verify the feasibility and validity of the proposed method. All resolutions of the digital images are 15 μm, the parameters: λ = 532 nm, d1 = d2 = 0.01 m, and δ = π/2. The sizes of the measurement key and the sampled results are 64 × 256, and the sizes of other images are 256 × 256.
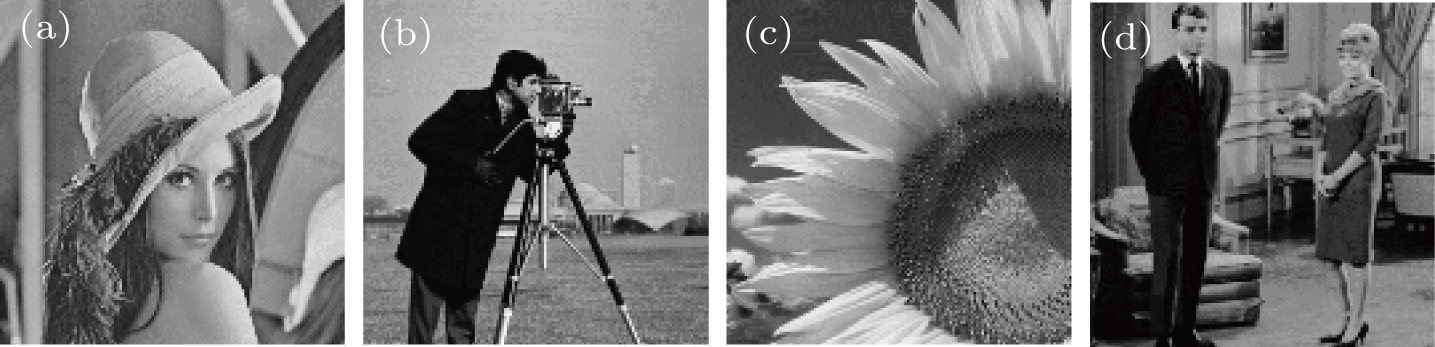
Four plaintext images with 256 × 256 pixels to be encrypted are shown in Figs.
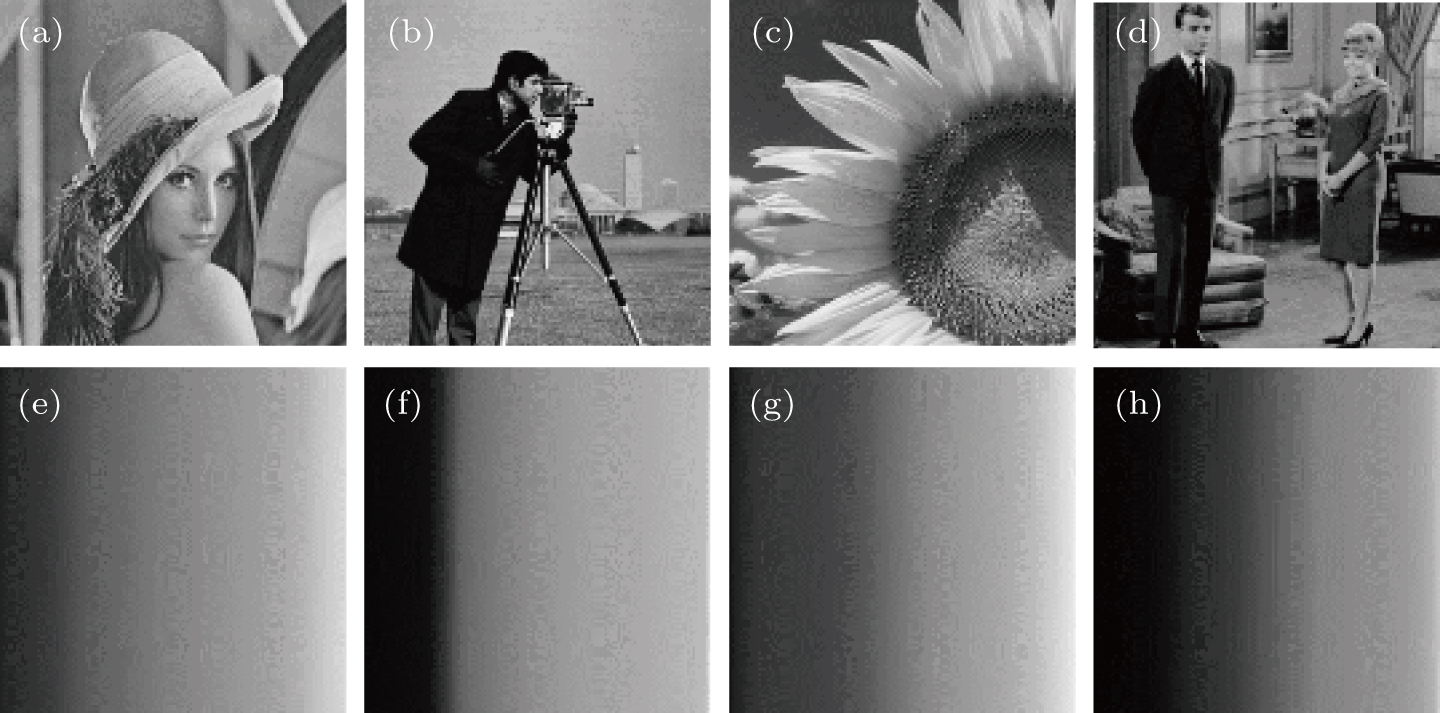 | Fig. 3. (a)–(d) Four secret images to be encrypted; (e)-(h) the corresponding reordered images after pixels ascending order for (a)–(d). |
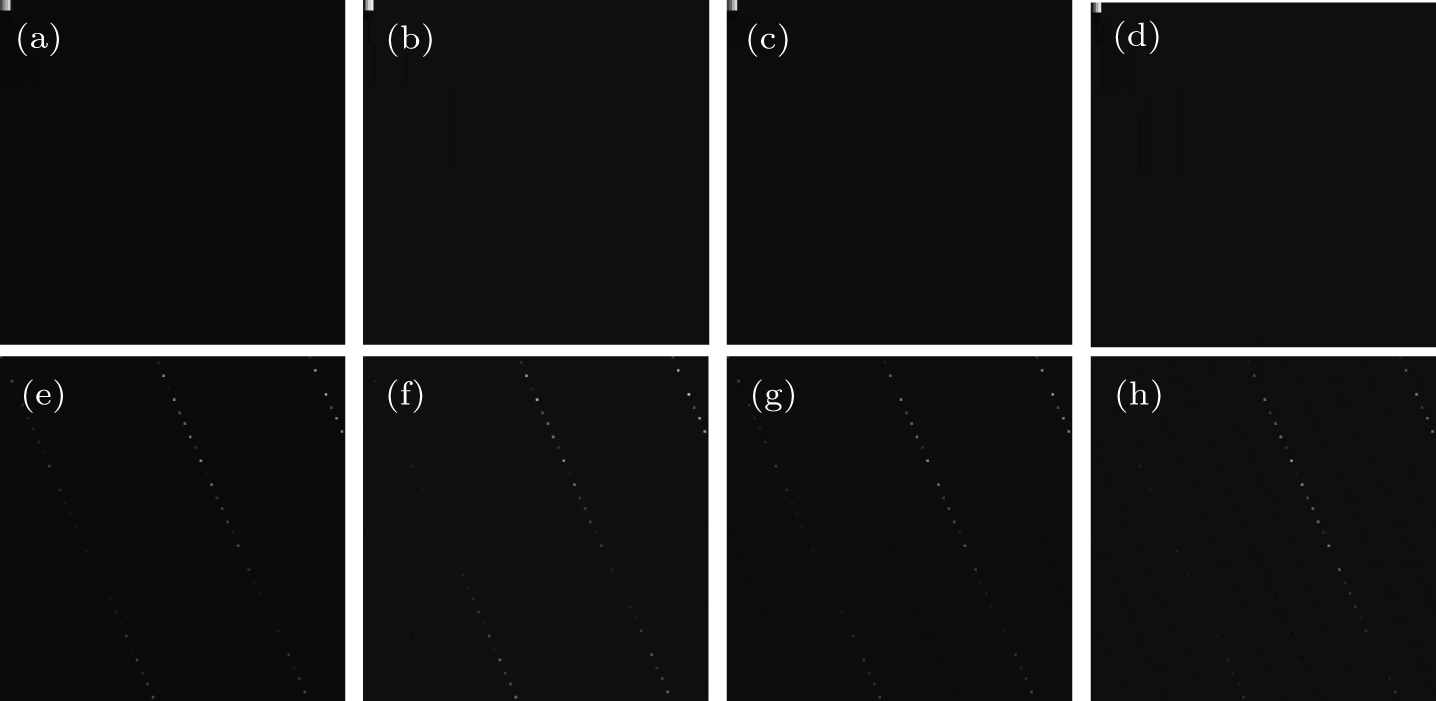 | Fig. 4. (a)–(d) Four sparse images after 5-order Haar DWT; (e)–(h) the corresponding images after Arnold transform for (a)–(d). |
A preselected Gaussian random matrix, acting as a measurement matrix, is shown in Fig.
During decryption, figures
| Table 1.
Four quality evaluation metrics for the decrypted images. . |
Next, as shown in Fig.
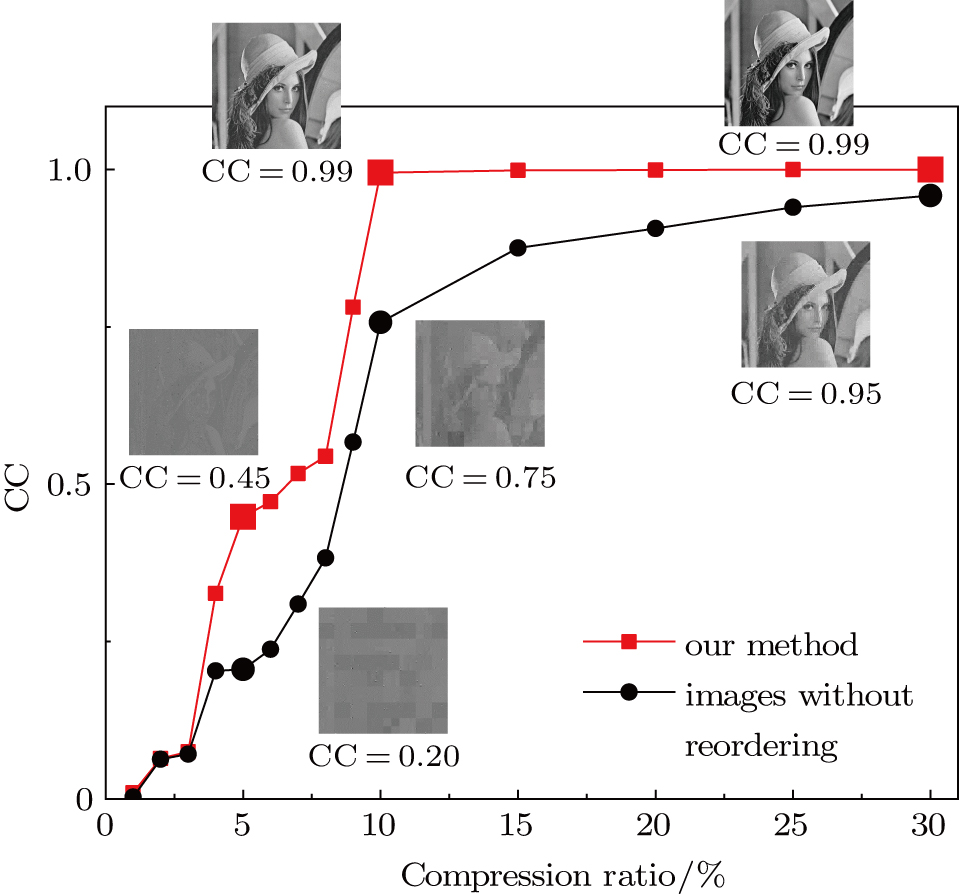 | Fig. 11. (color online) The variation curve between the CCs of the decrypted image and compression ratio. |
Taking ‘Lena’ as an example, the time complexity of the proposed encryption method is plotted in Fig.
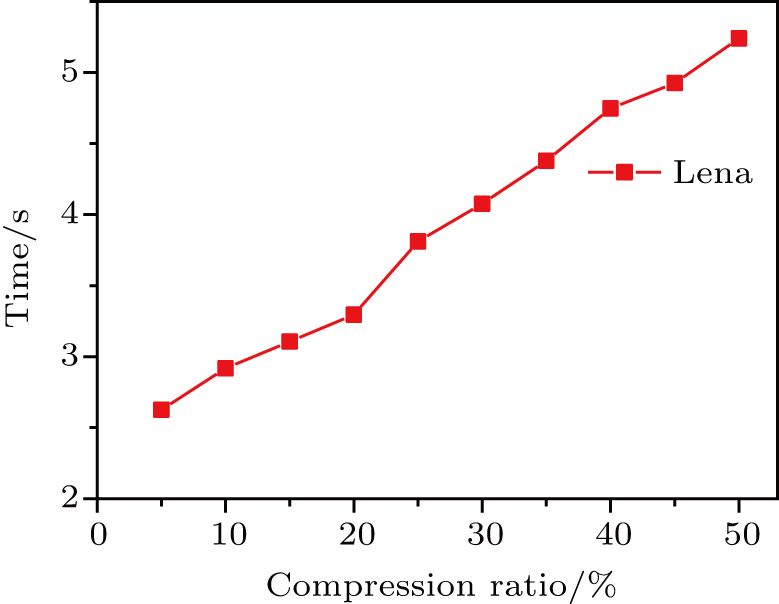 | Fig. 12. (color online) The variation curve between the time for encryption and decryption and the compression ratio. |
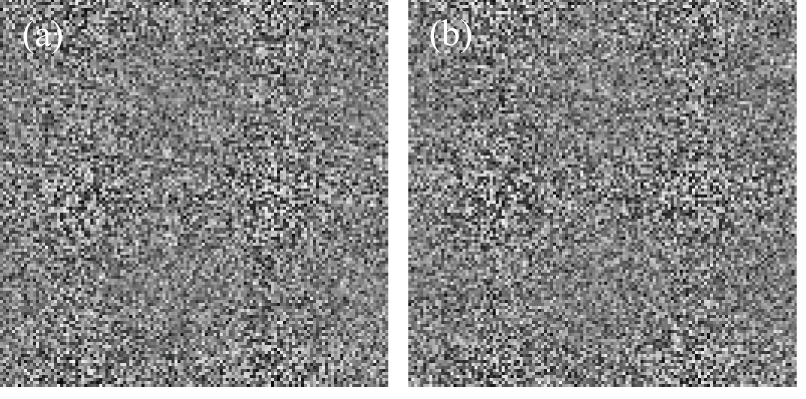
To reveal that our proposed method is resistant to statistical attack,[54–57] we encrypt two sets of plain images, each of which consists of four images. Fig.
To further illustrate the performance, the correlation of adjacent pixels is analyzed. We randomly select adjacent pixels from original images and interferograms on the horizontal (vertical, diagonal) direction, and calculate the adjacent pixels correlation.[54–57] All results are shown in Table
| Table 2.
Adjacent pixels correlation of original images and interferograms. . |
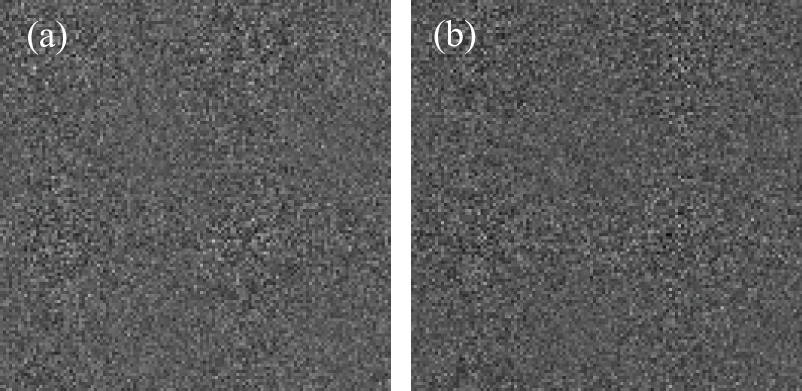
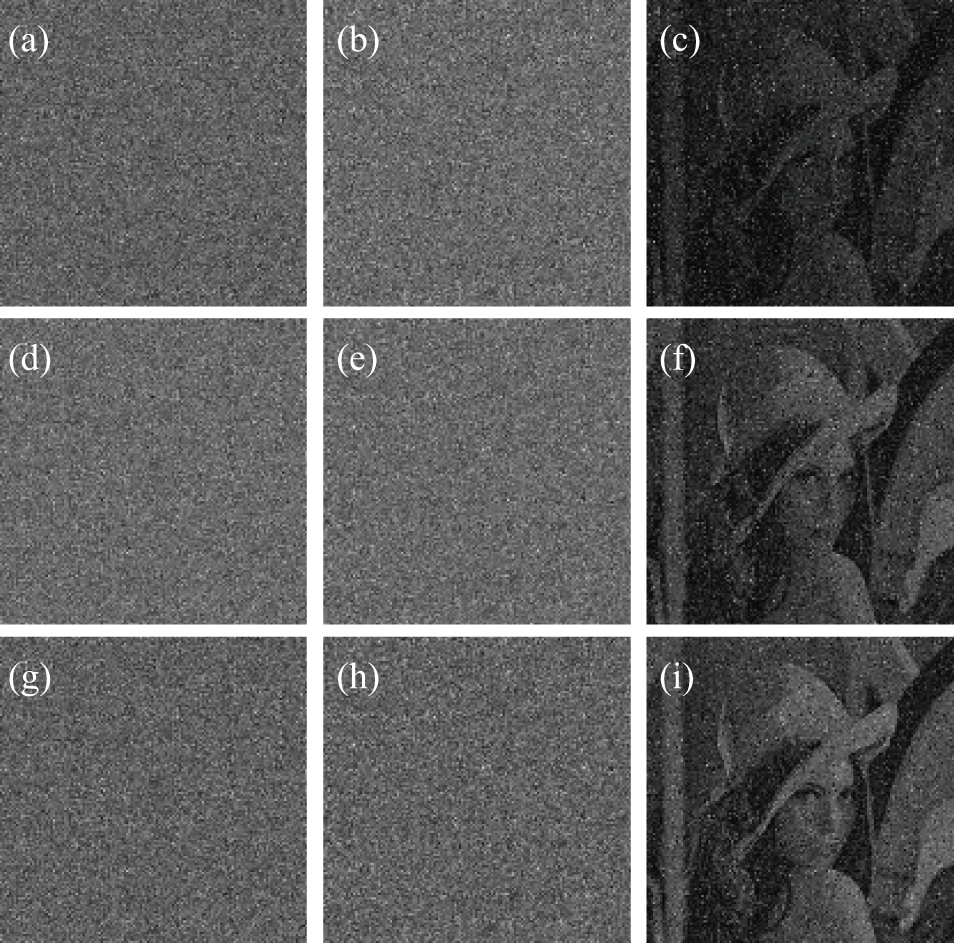
Then, a set of robustness tests against possible attacks are investigated. Two interferograms are contaminated by three different noise attacks: Gaussian white noise of mean 0 and variance 0.01 (as shown in Figs.
The cropping attack on P2 is tested here. Figure
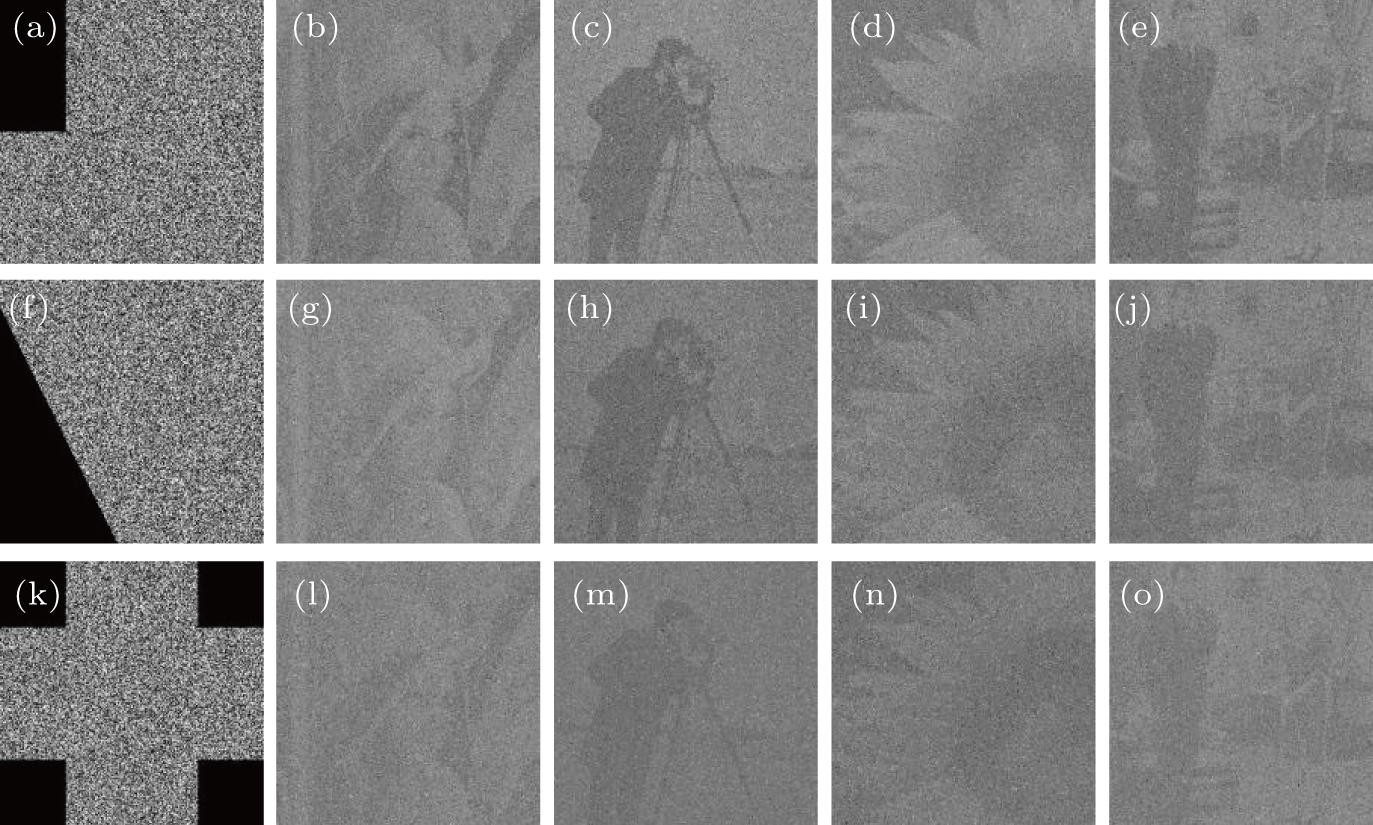 | Fig. 15. Three different types of cropping attack: (a) 12.5% occlusion; (f) 20% occlusion; (k) 25% occlusion; the corresponding decrypted images follow with them at the same rows. |
Different from our previous encryption works based on two-steps of phase-shifting interferometry,[25] in this paper, we introduce an advanced image acquisition and reconstruction technique termed compressive sensing theorem and encrypt n images with only two interferograms. The proposed method can enhance the data usage efficiency of interferograms and lessen the storage of ciphertexts. Compared with the reported optical cryptosystems based on compressive sensing and DRPE,[39] the main advantage of our proposed scheme can be summarized as follows. (i) Prior to compression, we first reorder the original images, which results in smaller non-zeros wavelet coefficients of original images and a lower compression ratio with higher decrypted quality. (ii) The two-step phase-shifting interferometry is easily capable of recording the phase information of complex amplitude which is difficult for DRPE.
In conclusion, we proposed a multiple-image encryption method based on two-step phase-shifting interferometry and spatial multiplexing of the smooth compressed signal. Followed by pixels ascending reordering, DWT, sparseness operation, Arnold transform and pixels sampling for four different secret images, one combined image can be grouped with the aid of CS and spatial multiplexing techniques. Then the combined image can be encoded into only two interferograms ciphertexts by the two-step PSI and DRPE, by which the efficiency of ciphertexts data transmission has been greatly raised. The use of the CS theory decreases the data volume of the secret images, thus, with this approach, it is possible to realize multiple image encoding and encryption. Both theoretical analysis and numerical simulations confirm the feasibility of the proposed method.
| [1] | |
| [2] | |
| [3] | |
| [4] | |
| [5] | |
| [6] | |
| [7] | |
| [8] | |
| [9] | |
| [10] | |
| [11] | |
| [12] | |
| [13] | |
| [14] | |
| [15] | |
| [16] | |
| [17] | |
| [18] | |
| [19] | |
| [20] | |
| [21] | |
| [22] | |
| [23] | |
| [24] | |
| [25] | |
| [26] | |
| [27] | |
| [28] | |
| [29] | |
| [30] | |
| [31] | |
| [32] | |
| [33] | |
| [34] | |
| [35] | |
| [36] | |
| [37] | |
| [38] | |
| [39] | |
| [40] | |
| [41] | |
| [42] | |
| [43] | |
| [44] | |
| [45] | |
| [46] | |
| [47] | |
| [48] | |
| [49] | |
| [50] | |
| [51] | |
| [52] | |
| [53] | |
| [54] | |
| [55] | |
| [56] | |
| [57] |