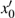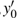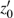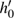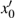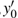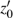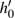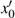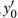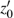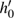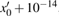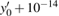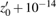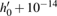† Corresponding author. E-mail:
Project supported by the National Natural Science Foundation of China (Grant Nos. 61661008 and 61603104), the Natural Science Foundation of Guangxi Zhuang Autonomous Region, China (Grant Nos. 2015GXNSFBA139256 and 2016GXNSFCA380017), the Funding of Overseas 100 Talents Program of Guangxi Provincial Higher Education, China, the Research Project of Guangxi University of China (Grant No. KY2016YB059), the Guangxi Key Laboratory of Multi-source Information Mining & Security, China (Grant No. MIMS15-07), the Doctoral Research Foundation of Guangxi Normal University, the Guangxi Provincial Experiment Center of Information Science, and the Innovation Project of Guangxi Graduate Education (Grant No. YCSZ2017055).
In this paper, a novel image encryption scheme based on Kepler’s third law and random Hadamard transform is proposed to ensure the security of a digital image. First, a set of Kepler periodic sequences is generated to permutate image data, which is characteristic of the plain-image and the Kepler’s third law. Then, a random Hadamard matrix is constructed by combining the standard Hadamard matrix with the hyper-Chen chaotic system, which is used to further scramble the image coefficients when the image is transformed through random Hadamard transform. In the end, the permuted image presents interweaving diffusion based on two special matrices, which are constructed by Kepler periodic sequence and chaos system. The experimental results and performance analysis show that the proposed encrypted scheme is highly sensitive to the plain-image and external keys, and has a high security and speed, which are very suitable for secure real-time communication of image data.
The secure and real-time communication of image data is becoming more and more important, since the digital image plays a significant role in our life with the prevalence of the internet and information technology.[1–3] Due to a bulky data redundancy and high correlation between adjacent pixels, the traditional encrypted schemes are not suitable for the image encryption through internet.[4] Then the chaos-based image encryption methods have been utilized due to its superior characteristics,[5] including sensitivity to initial condition and controlling parameters, ergodicity, pseudo-randomness, and nonlinear unpredictability. The primary image encryption algorithms are based on some simple low-dimensional chaotic systems, and their security and plasticity are not good. Therefore, the experts proposed the high-dimensional hyper-chaotic systems by analyzing the nonlinear dynamic characteristics[6,7] to be used in the design of image encryption schemes.Since then, a variety of chaos-based image encryption algorithms have been proposed.[8–20]
Inspired by the architecture of permutation-diffusion which is first presented by Shannon,[21] most of the chaos-based image encryption schemes are based on not only this architecture, but also a combination with other theory, such as, compression sensing,[13,14] DNA sequences,[15] geometric transformation,[2,16] and physical phenomenon.[17–19] Specifically, Chai et al. proposed a visually secure image encryption scheme by using the zig–zag confusion and compression sensing,[13] which can achieve the image data security and image appearance security simultaneously to reduce the possible transmission bandwidth and storage space. Zhou et al. presented an efficient image compression-encryption scheme based on the hyper-chaotic system and two-dimensional (2D) compressive sensing.[14] A novel image encryption scheme based on deoxyribonucleic acid (DNA) sequence operations and chaotic system was proposed.[15] Wu et al.[16] proposed a new lossless encryption algorithm for color images based on a six-dimensional (6D) hyper-chaotic system and the 2D discrete wavelet transform (DWT) in both the frequency domain and the spatial domain. Wang et al.[17] proposed a new image encryption scheme, which used the simulated annealing algorithm to generate the random sequence for the confusion phase. The merit of this scheme is that the random sequence is generated excellently. Ye et al.[18] adopted self-cited pixel summation to produce the keystreams to be used in both permutation and diffusion process. And in Ref. [19] a novel image encryption algorithm based on three-dimensional (3D) Brownian motion and chaotic systems was presented to overcome the limitation of movement range of bits.
In spite of having such a superiority, few schemes have been used due to some drawbacks they have. For instance, a lookup table-based image encryption scheme[22] was analyzed to beable to be broken by chosen-plain-text attack and chosen-ciphertext attack[23] due to an algebraic weakness of the scheme. And a general attack scenario was given in order to conduct security analyses of chaos-based cryptosystems and the proposed general attack scenario was applied to recently proposed chaos-based image encryption scheme in Refs. [24] and [25]. A symmetrical image encryption algorithm based on skew tent map[26] was found to be vulnerable to differential attack.[27] An image encryption scheme based on DNA coding and information entropy[28] is found to have two vulnerabilities to make the encryption fail under chosen-plain-text attack; one is that entropy fails to protect permutation indexes under chosen-plain-text attack, and the other is the substitution of elements in the last column leak patterns of the encoding rule so that it permits recovering the encoding rule and covering matrix after breaking the permutation.[29]
Inspired by the above cryptanalysis and improvement in chaos-based image encryption schemes,[22,24,26,28] a novel image encryption algorithm based on the Kepler’s third law and random Hadamard transform is proposed in the paper. First of all, two Kepler periodic sequences are generated in terms of the theory of Kepler’s third law, which is used to scramble the image. Then, a random Hadamard matrix is constructed by combining the standard Hadamard matrix with the chaos system, and it is utilized to transform image data to coefficients in Hadamard domain to be further permuted and we can obtain the permuted image by the inverse Hadamard transform. Furthermore, an interleaving diffusion based on two special matrices is adopted to increase the security of scheme. In the proposed encryption algorithm, both the permuted process and the diffusion process are closely related to the plain-text because of the rule of the Kepler’s third law. Specifically, the period of circle shifting in the permutation process and the diffusion sequences are determined by the coordination distribution of each pixel and the quality of plain-text, which greatly enhance the sensitivity of algorithm to plain-text and improve the ability to resist the differential attack and statistical security. Besides, the universal gravitational constant G of the Kepler’s third law can further increase the randomness of chaotic sequences to prevent violent attacks. In addition, the execution speed of image encryption can be improved by using the random Hadamard transform because it is very suitable for 2D data processing and can increase further the scrambling effect.
The rest of this paper is organized as follows. In Section
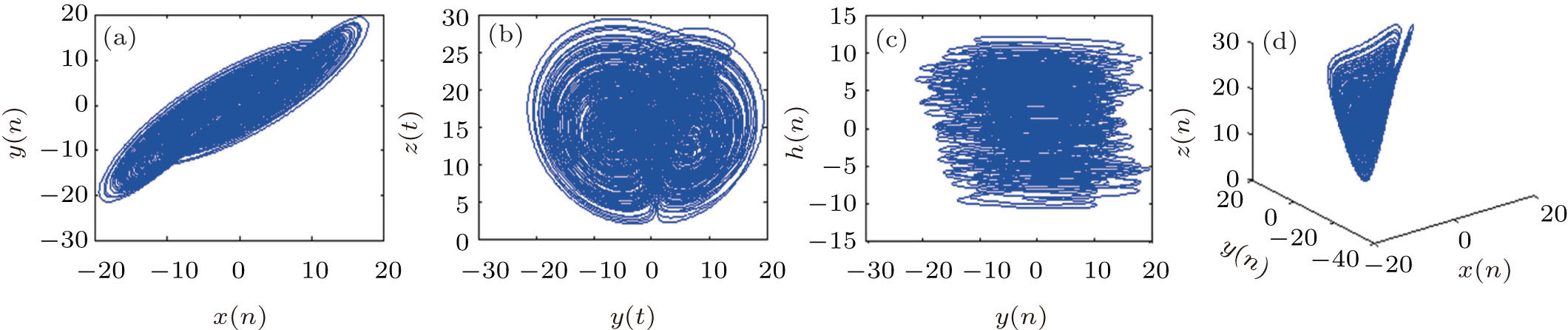
Compared with general chaos system, the hyper-chaotic system has many outstanding characteristics, e.g., many complex dynamical characteristics, good randomness and unpredictability, large key spaces, and various applications in today’s image encryption.[30–32] According to the further analysis of the Chen system,[33] a Chen-based hyper-chaotic system has been proposed and used in information security,[34,35] which is defined by
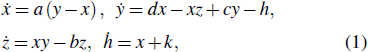
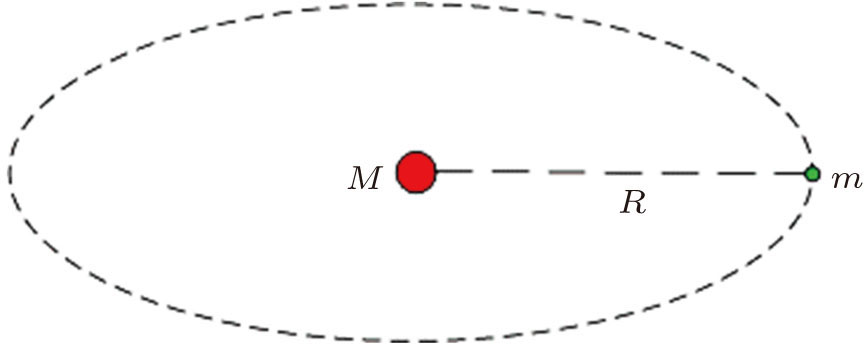
Kepler’s third law is well known in planetary motion of physics,[37] which reveals that the square of the orbital period of a planet is directly proportional to the cube of the semi-major axis of its orbit. It can be described by

Now, we come to derive planetary motion for an elliptical orbit shown in Fig.

Re-arranging Eqs. (

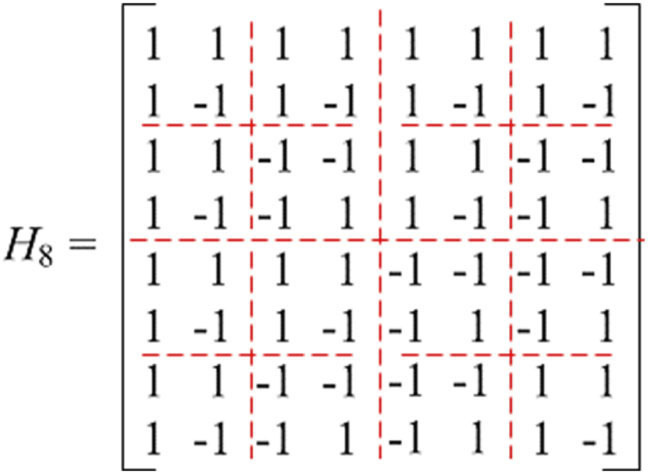
The Hadamard transform (HT) is an example of a generalized class of Fourier transforms, which can be applied to the fast discrete image transform. The Hadamard matrix is the kernel of the HT, and it is a square matrix composed of −1 and 1 as shown in Fig.

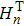

Because of the orthogonal property of Hadamard matrix, a kind of a random Hadamard matrix (RHM) can be constructed through changing the location of element in Hadamard matrix based on chaos theory, the detailed steps of which are as follows.
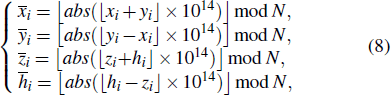
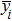
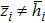
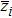
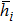
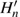
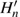
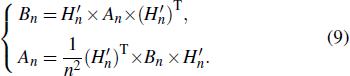
A good permutation technology can resist occlusion well, so it generally includes several features, that is: 1) the probability of changing the position of each pixel is basically the same; 2) the correlation between adjacent pixels should be seriously broken; 3) the distance between adjacent pixels of original should be become larger and larger. Considering these basic requirements, on the basis of the Kepler’s Third Law, the movement period of the barycenter of each row or column surrounding the barycenter of the whole image is first calculated, which is used as the parameter of cyclic shift cycle to scramble the plain image in the spatiotemporal domain. Specifically, the plain image is transformed by the RHT into another matrix, each row and each column of this matrix are scrambled based on the rule of cyclic shift cycle, and the scrambled image can be obtained through the Hadamard inverse transform in Eq. (
Generally, the coordinates of each pixel and barycenter of image should be determined to compute the movement period. For example, a Lena image
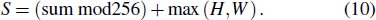
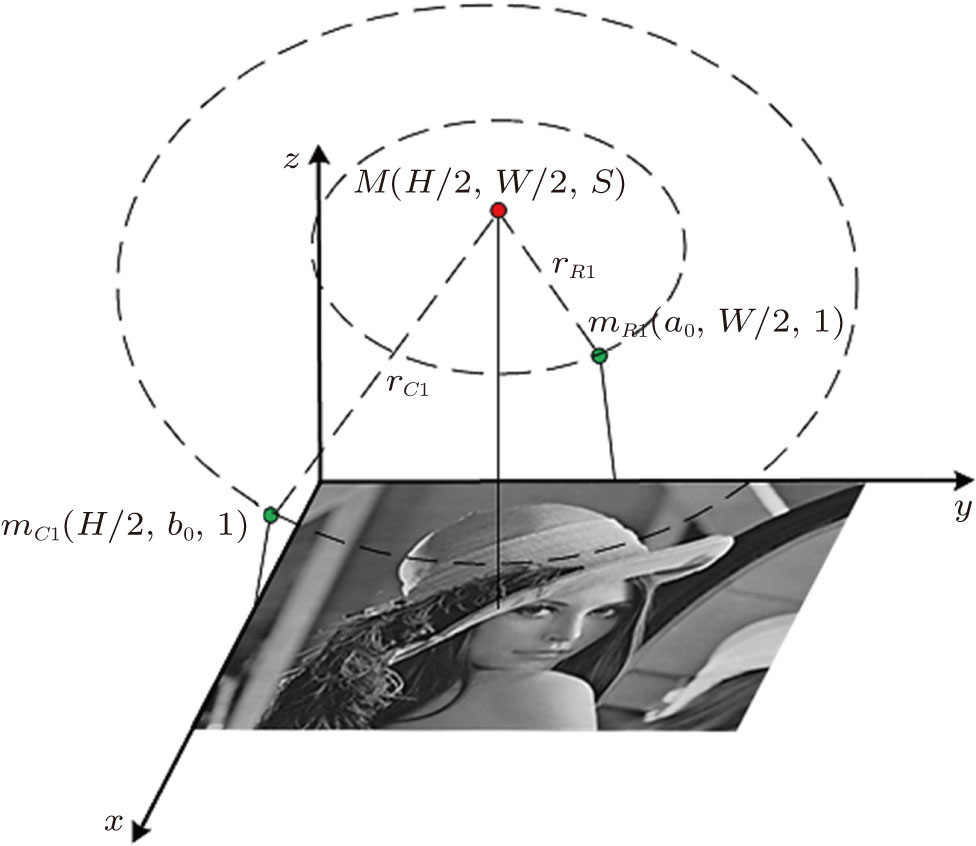 | Fig. 4. (color online) Determination of coordination of barycenter of image based on Kepler’s third law. |
As shown in Fig.
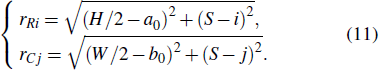
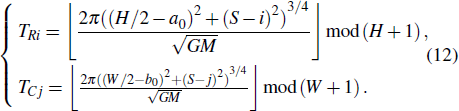
As mentioned above, the parameters TRi and TCj are used as the controlling variables to adjust the cyclic shift operation, and the specific method is given below.
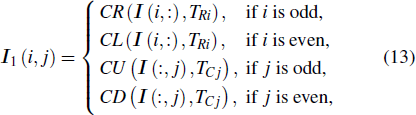
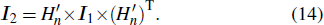
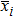
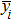
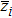
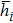
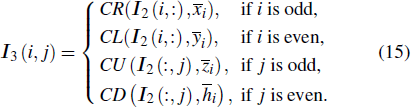
Finally, the permuted image
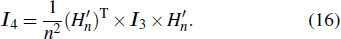
As mentioned above, the parameters TRi and TCj are tightly related to the plain image. Therefore, the encryption scheme would be better if these two parameters are applied to the process of diffusion, which is described as follows.
Firstly, re-iterate the hyper-Chen system (500 + (H × W)/2) times, and extract the back (H × W)/2 data to obtain novel four sequences, i.e., 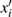
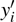
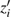
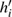
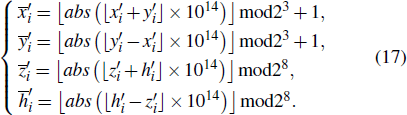
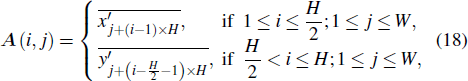
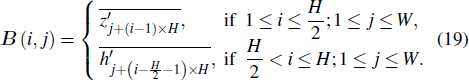
Moreover, the matrices 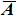
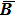
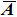
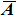
In order to improve the diffusion performance, on the basis of the operation
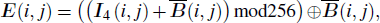
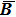
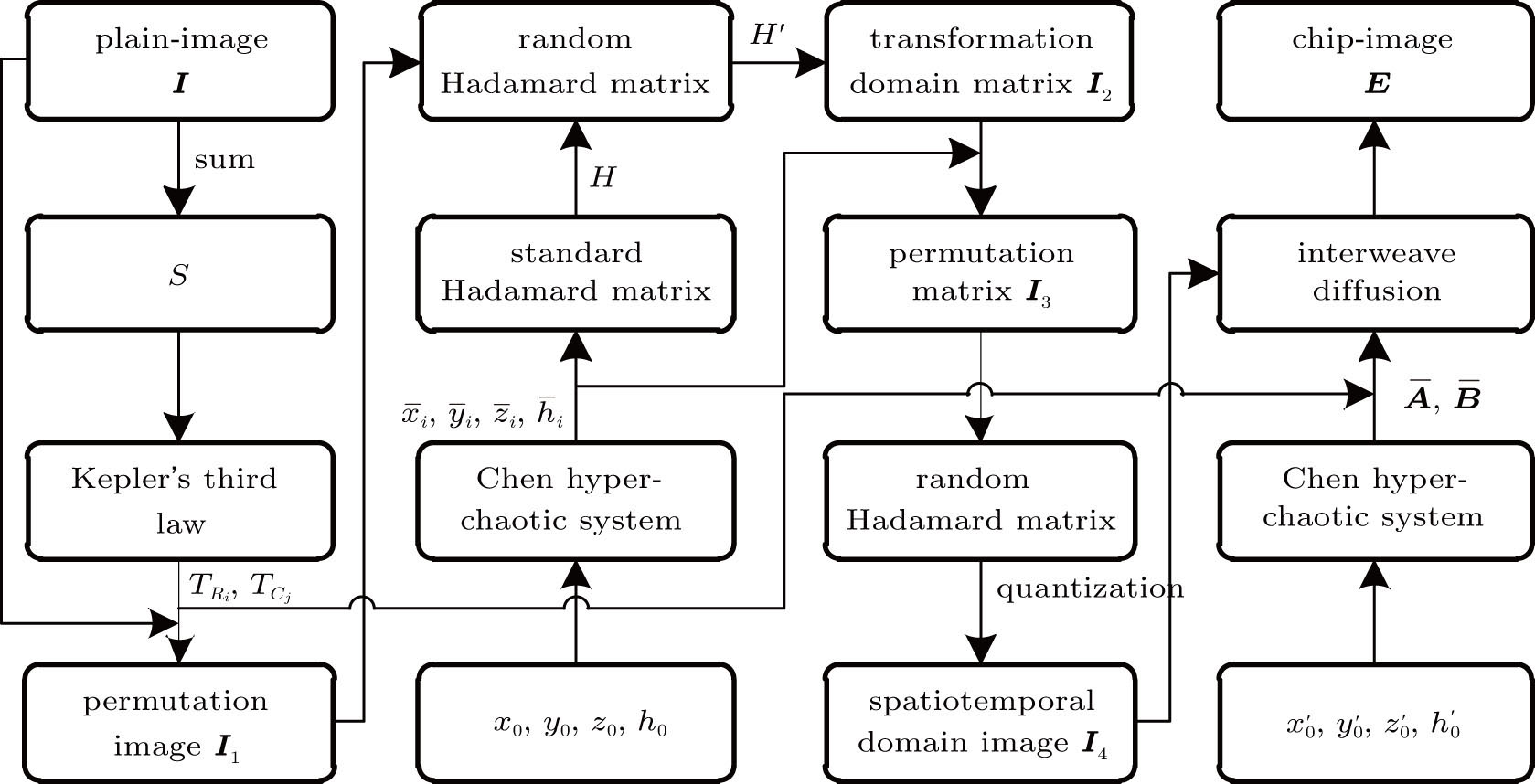
As described above, the whole encrypted scheme contains the permutation and diffusion, which cross each other as shown in Fig.
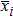
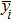
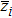
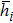
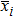
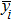
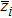
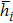
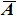
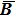
The decrypted process is the corresponding inverse process shown in Fig.
In the experiments, multiple standard grey images with a size of 512 × 512 are tested. All the simulations are done under the MATLAB R2014a platform on a Windows 7 operating system with Intel(R) Xeon(R)E3-1246 CPU 3.5 GHz (E6500) processor with 8 GB of random-access memory. Two sets of initial data for the hyper-chaotic Chen system are randomly chosen, which are {x0 = 0.1314, y0 = 0.5214, z0 = 0.3689, h0 = 0.8419 and 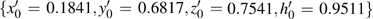
As a good image encryption system, the key space must be large enough to resist the adversaries guessing the key using a brute-force attack.[38] For the proposed encrypted scheme, the key consists of two parts: 1) two sets of initial values of the hyper-chaotic Chen system (x0, y0, z0, h0) and 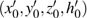
Differential attack (DA) is an important criterion to measure the merits of the encryption algorithm, which requires that a slight change in the plain-image can cause a significant difference in the cipher-image. Two metrics are used to test DA: the number of pixel’s change rate (NPCR) and the unified averaged changing intensity (UACI), which can be calculated from
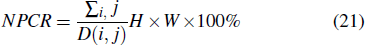
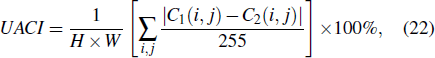
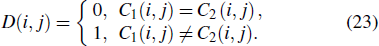
The expected values of the NPCR and UACI are 99.6094% and 33.4635%, respectively.[18] We randomly choose five different locations of the five different plain-images for experiment and test, and the corresponding results of NPCR and UACI are listed in Table
| Table 1. NPCR and UACI for different plain images. . |
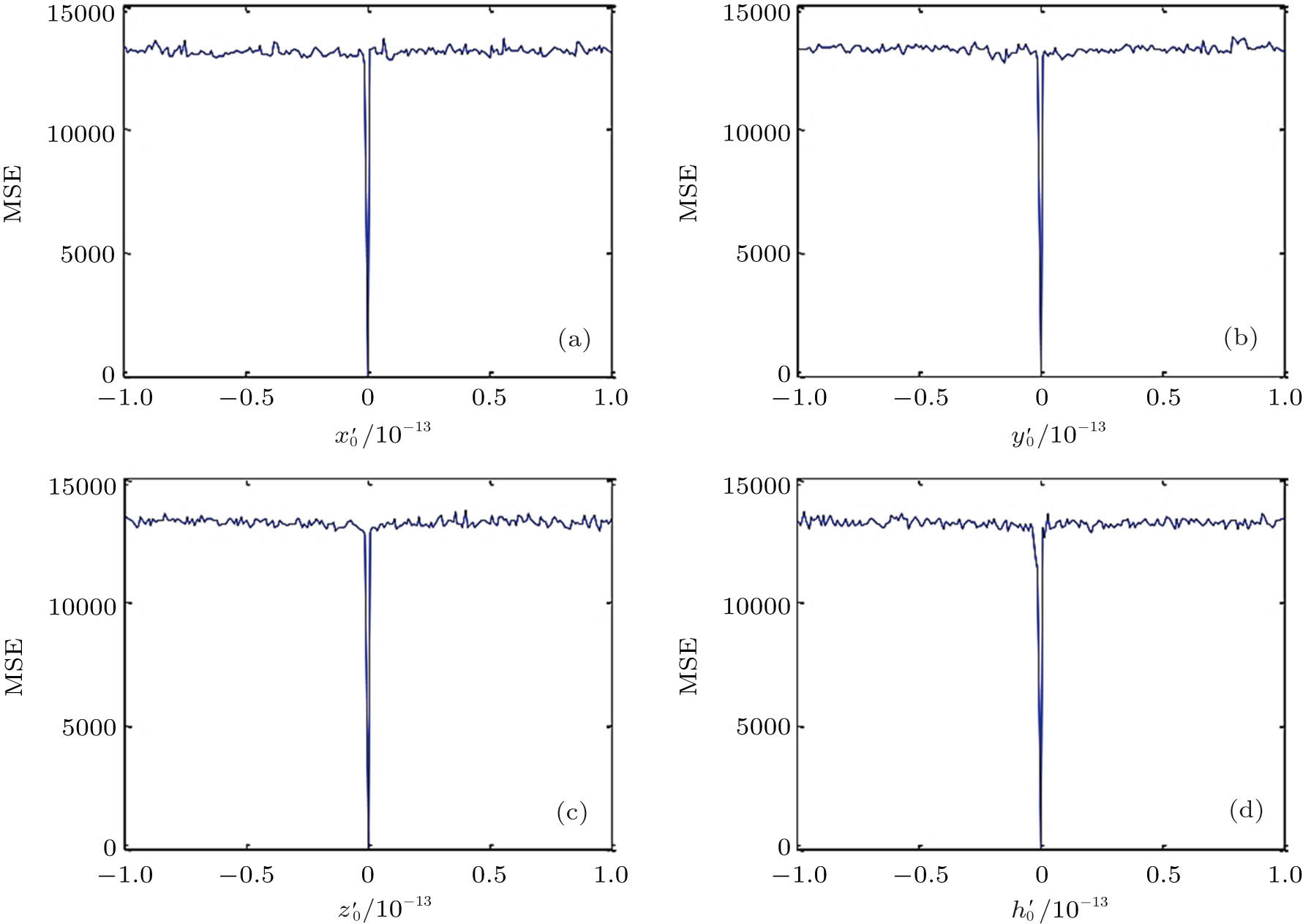
According to the Kerckhoff’s principle,[40] a high sensitivity to the key is critical for a secure encrypted scheme. Taking the Lena image shown in Fig.
Besides, the mean square error (MSE) between original image and decrypted image can be used to evaluate the key-sensitivity of encryption algorithm.[41] The MSE is calculated from
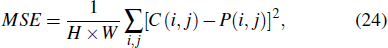
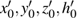
Information entropy is often used to measure the confusion degree of information sources, and prevent the attacker from utilizing its image characteristics to crack, which is given by
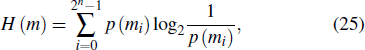
| Table 2. Results of information entropy. . |
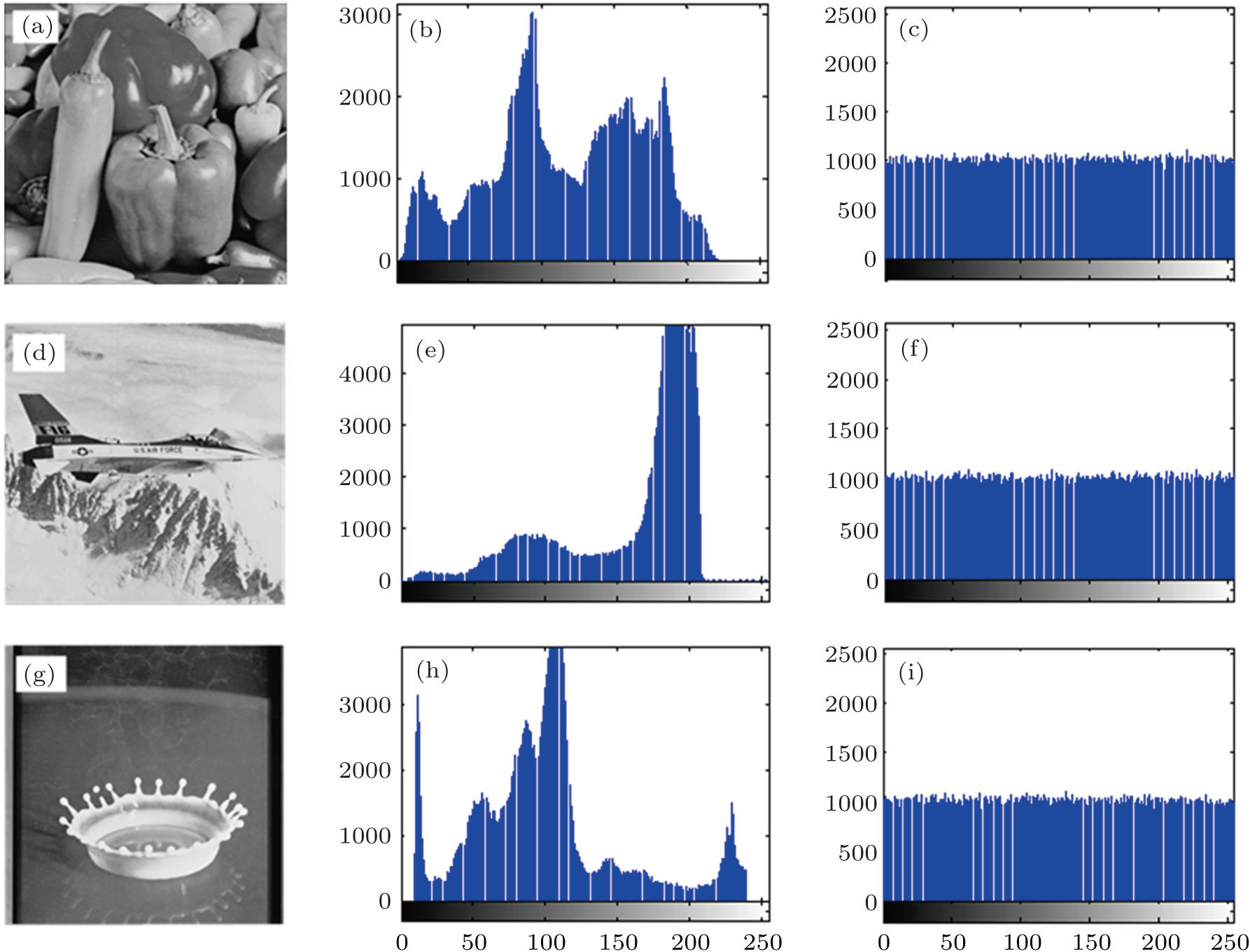
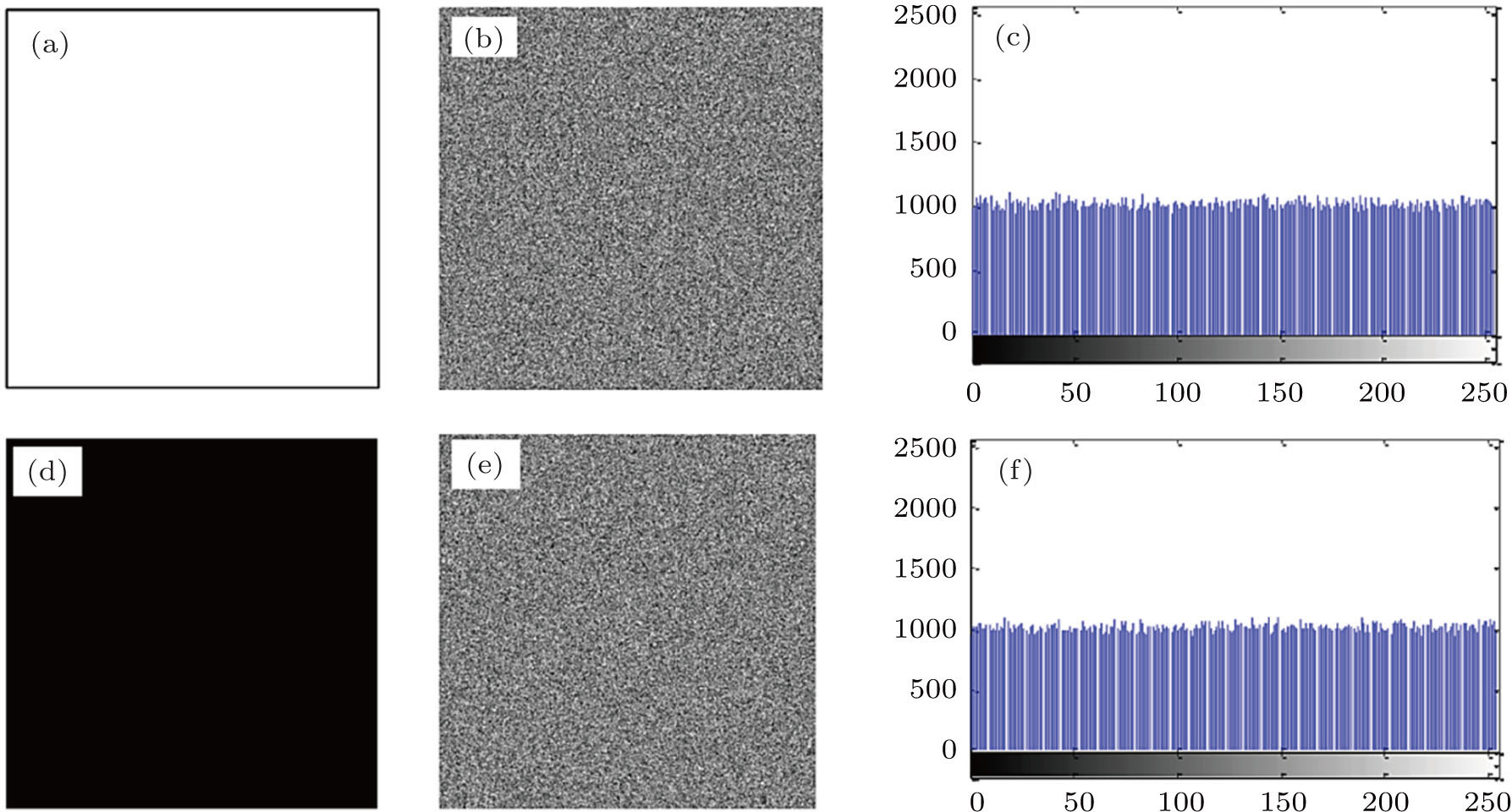
A good encryption algorithm must make the histogram of encrypted image uniform to be robust against the statistical analysis. Figure
In addition, the variance of the histogram can be used to evaluate the uniformity of the encrypted image.[43] The smaller the variance of the histogram, the better the uniformity of the encrypted image is. The variance of the histogram can be calculated from
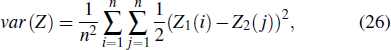
| Table 3. Comparison among variancesof histograms of all secret keys in the proposed algorithm. . |
Besides, the percentage of variance differences can be also used to measure the uniformity of each parameter of the secret keys, which is calculated from
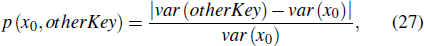
| Table 4. Comparison among percentages of variances difference of histograms of all secret keys in the proposed algorithm. . |
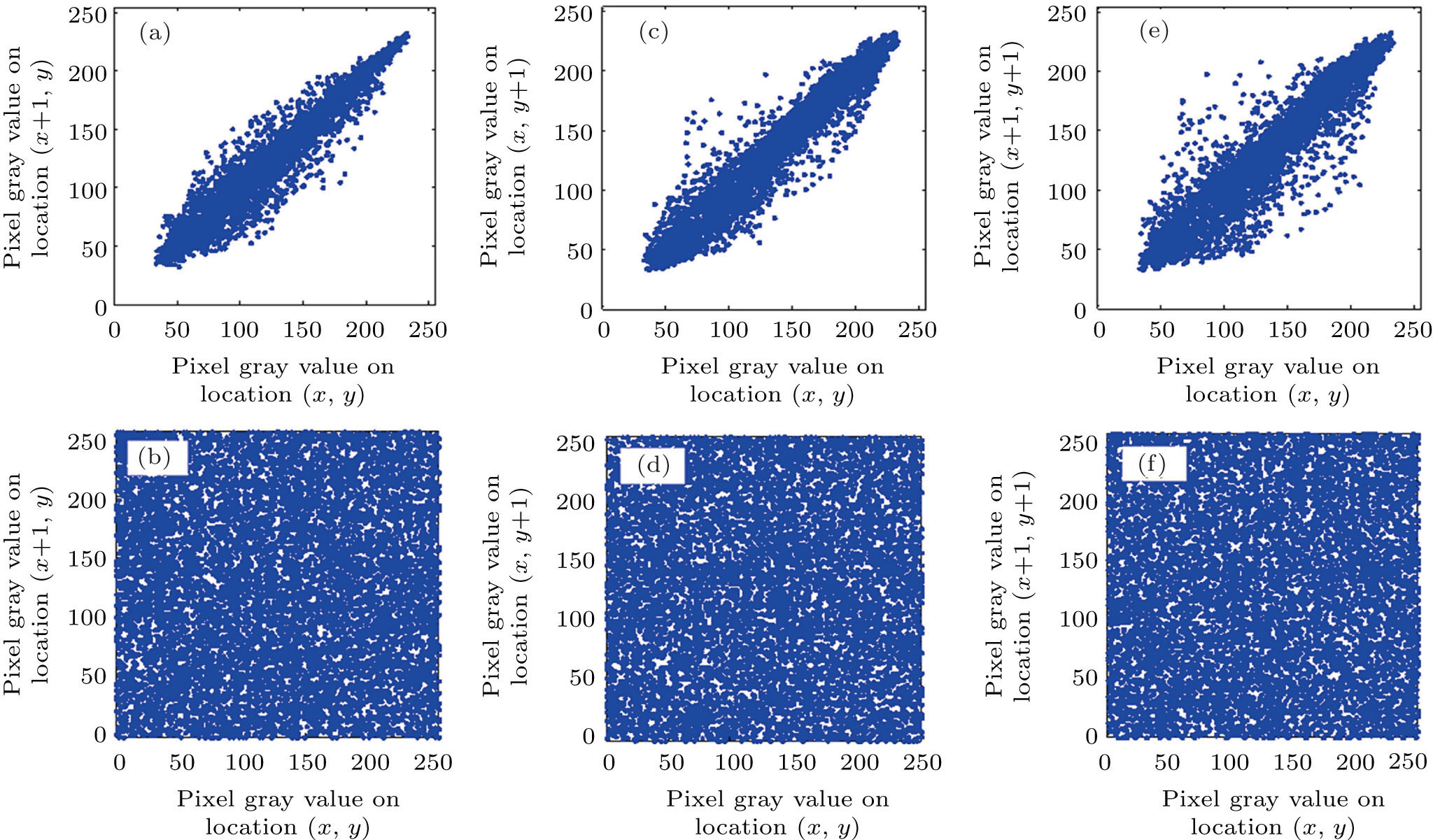
Any natural image contains a large amount of redundant information about a great correlation between two adjacent pixels, which can be considered as an important information about the crack made by attacker. Therefore, the test of correlation-coefficient is also a vital factor to measure the performance of the encrypted scheme. The as 104 adjacent pixels are randomly chosen in the horizontal, vertical and diagonal directions of the plain-image (Fig.
Moreover, the specific correlation coefficient rxy between adjacent pixels can be calculated from
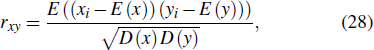
| Table 5. Correlation coefficients of plain- and cipher-images. . |
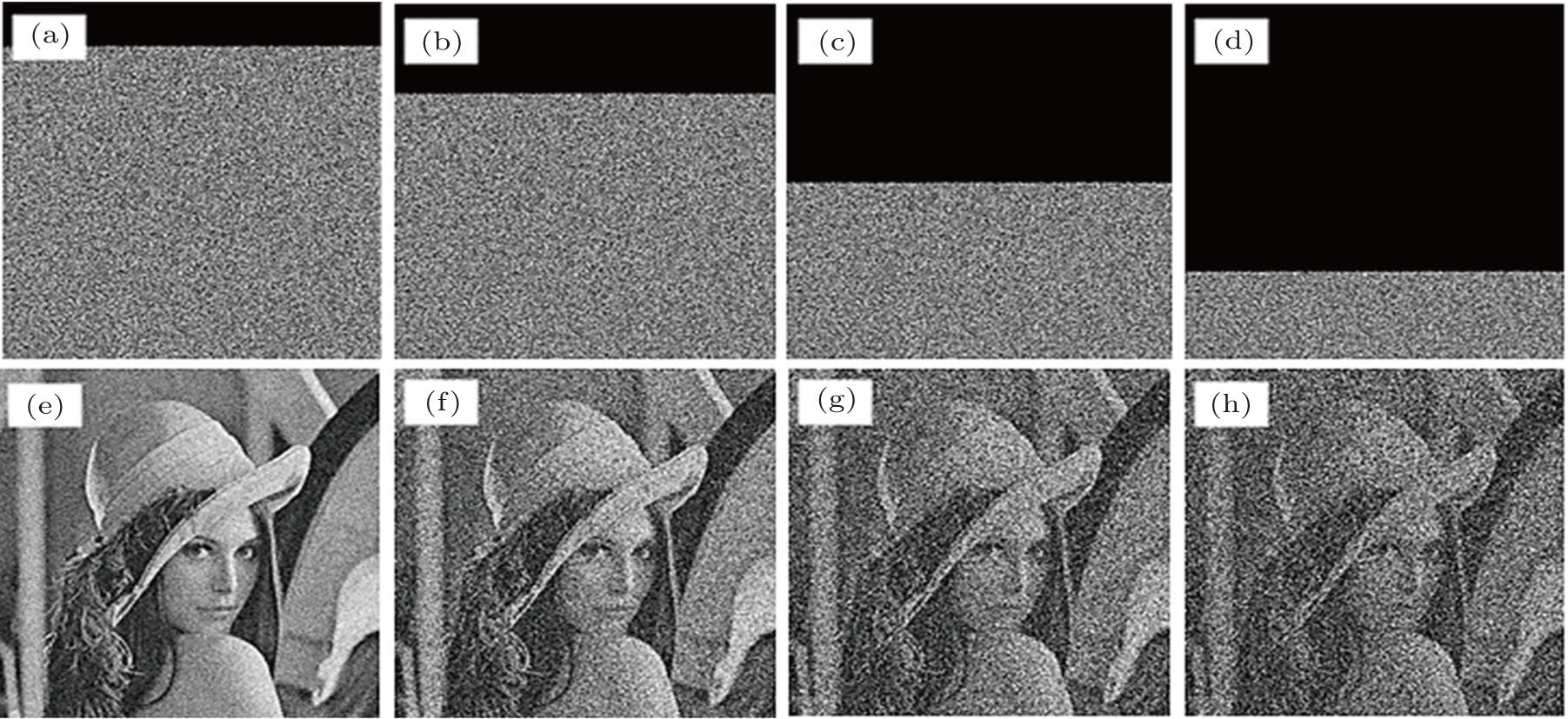
Occlusion attack and noise interference are inevitable in the information transmission due to network failure or network congestion, thus they are also two important test parameters to measure the performance of encrypted scheme, i.e., a good encryption algorithm must have a strong robustness against the occlusion attack and noise attack. Figure
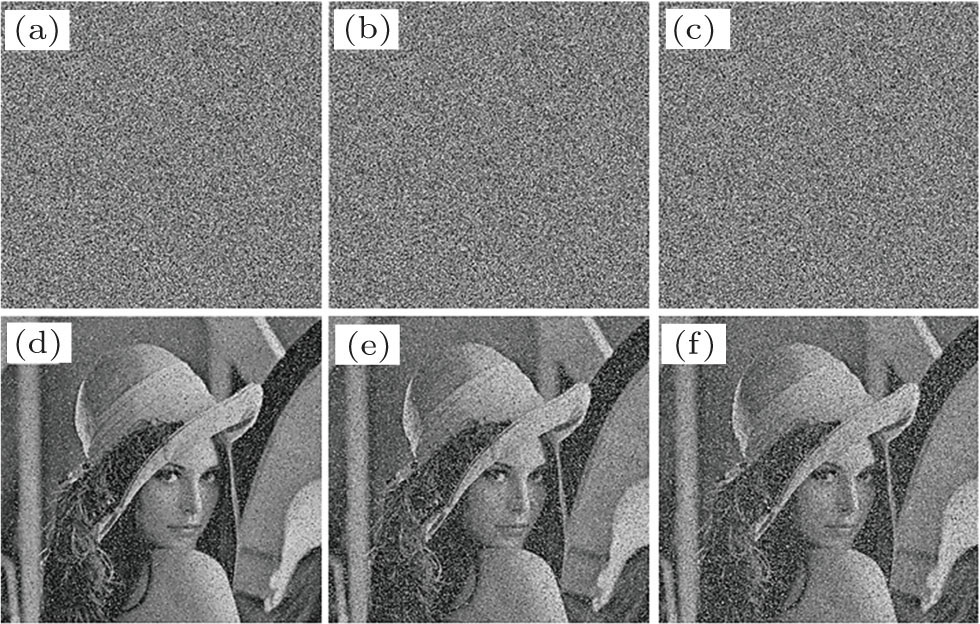
On the other hand, the Salt and pepper noise and Gaussian noise are common noises to be experimented to test the noise attack, and the results are shown in Figs.
 | Fig. 13. (color online) Salt and pepper noise attack analysis, showing ((a)–(c)) cipher-images with noise density = 5% (a), 10% (b), and 20% (c), and ((d)–(f)) the corresponding decrypted images. |
Ciphertext only, known-plain-text attack chosen-plain-text attack, and ciphertext attack are four most powerful classical attacks, and the chosen-plain-text attack is the most powerful attack.[45] Therefore, if the algorithm can resist chosen-plain-text attack, it can resist other three types of attacks to some extent. As for the proposed encryption scheme, the controlling parameters TRi and TCj are closely related to the plain-image information S, thus even if there is only one bit of change happening in the plain-image, TRi and TCj would be completely different. Moreover, the diffusion matrices 
Specifically, some special images are chosen to test the chosen plain-text attack, such as all-white image (Fig.
Besides, in order to test the ability of the proposed algorithm to resist the Ciphertext only attack, all the keys will be changed with 10−14 to decrypt the original encrypted image (see Fig.
An effective encrypted time can ensure the real-time communication of information, and thus except for a high secure scheme, there needs an efficient execution speed as well. In this paper, the encryption scheme includes four processes: pre-permutation in spatiotemporal domain, permutation in Hadamard domain, encrypted matrix construction, and interleaving diffusion. Taking a standard image Lena 512 × 512 (263 kB) for example, the specific time distribution is shown in Fig.
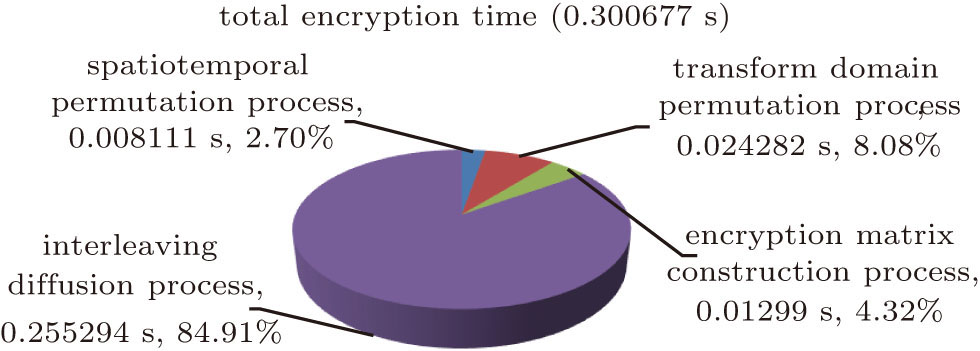 | Fig. 17. (color online) Average encrypted time and percentage of each component of the proposed algorithm for Lena with a size of 512 × 512. |
| Table 6. Relationship between encrypted time and the size of plain-image (in unit: s). . |
From Fig.
Besides, in order to compare with other relavent encrypted schemes, the proposed encryption algorithm is executed 100 times to compute the average encrypted speed and other performances. The results are given in Tables
| Table 7. Speed comparison of several cryptosystems (unit: Mb/s). . |
| Table 8. Performance comparison of several cryptosystems. . |
A novel hyper-chaos-based image encryption scheme is proposed in this study, which is based on the theory of Kepler’s third law and random Hadamard transform. And the classical permutation-diffusion encryption mechanism is adopted. In the permutation process, two Kepler periodic sequences are first generated in accordance of the image application of the Kepler’s third law, which is used to scramble the image. And the random Hadamard matrix based on chaos map is constructed to further permute the coefficients in the Hadamard domain, and then the permuted image can be obtained through the inverse Hadamard transform. In the diffusion process, two special matrices are constructed to complete the interleaving diffusion of each pixel. In order to improve the algorithm sensitivity to the plain image and the ability to resist the known-plain-text and chosen-plain-text attacks, the two Kepler periodic sequences used both in permutation process and in diffusion process and the two diffusion matrices are strong related to plain-image data. Several experimental and performance analyses, including key space analysis key sensitivity analysis differential analysis information entropy the histogram analysis correlation-coefficient analysis occlusion and noise attack analysis known-plain-text and chosen-plain-text attacks speed analysis and comparison show that the proposed algorithm is high sensitivity to original image, and has a good security and speed, which are suitable for image secure communication.In the future work, the capabilities of parallel implementation for color image encryption scheme will be considered and designed to make it optimal and universal in the application of image data field.