† Corresponding author. E-mail:
Reference-frame-independent quantum key distribution (RFI QKD) can generate secret keys without the alignment of reference frames, which is very robust in real-life implementations of QKD systems. However, the performance of decoy-state RFI QKD with both source errors and statistical fluctuations is still missing until now. In this paper, we investigate the performance of decoy-state RFI QKD in practical scenarios with two kinds of light sources, the heralded single photon source (HSPS) and the weak coherent source (WCS), and also give clear comparison results of decoy-state RFI QKD with WCS and HSPS. Simulation results show that the secret key rates of decoy-state RFI QKD with WCS are higher than those with HSPS in short distance range, but the secret key rates of RFI QKD with HSPS outperform those with WCS in long distance range.
Based on the laws of quantum physics, quantum key distribution (QKD)[1] allows two distant legitimate parties (typically called Alice and Bob) to share unconditionally secure keys, in the presence of the eavesdropper (Eve).[2] Since the first Bennett–Brassard-1984 (BB84) QKD protocol was proposed,[1] many successful QKD works have been achieved during the past decades.[3–15] In most of these experiments, a feedback setup is needed to align the reference frames between Alice and Bob, which will undoubtedly increase the complexity and time cost of QKD systems. Otherwise, the high quantum bit error rate (QBER) will prevent the generation of net secret keys.
Fortunately, reference-frame-independent QKD (RFI QKD) was proposed by Laing et al.[16] to avoid the active alignment of reference frames, which can obviously increase the whole communication efficiency between Alice and Bob. After that, a series of theoretical[17–19] and experimental[20–23] works on RFI QKD have been reported. However, none of them considered the practical scenarios including both source errors and statistical fluctuations.
In this paper, we investigate the performance of decoy-state RFI QKD in practical scenarios with two kinds of light sources, the heralded single photon source (HSPS) and the weak coherent source (WCS). The widely used vacuum + weak decoy-state method[24–28] is adopted to combat the photon-number-splitting (PNS) attack[29,30] caused by the multi-photons in the practical sources. Moreover, clear comparison results of decoy-state RFI QKD with WCS and HSPS are given, and simulation results show that the decoy-state RFI QKD even with both source errors and statistical fluctuations is very practical and robust.
RFI QKD employs three mutually unbiased bases (Z, X, and Y) to encode the information,[16] which is very similar to the six-state protocol.[31] During the quantum communication phase, Alice randomly prepares quantum states with her local bases XA, YA, and ZA, and sends them to Bob. Bob randomly measures the received states with his local bases XB, YB, and ZB. In RFI QKD, the stability of the Z basis can be well maintained, which is also the case in most other QKD systems, while the X and Y bases are allowed to vary slowly. That is, Alice and Bob’s Z, X, and Y bases satisfy ZB = ZA, XB = cosβXA + sinβYA, and YB = cosβYA − sinβXA, where β is the relative rotation between Alice and Bob’s reference frames and may drift with time slowly. After the quantum communication phase, Alice and Bob can distill secret keys from the data in ZAZB basis, and estimate Eve’s information from the data in XAXB, XAYB, YAXB, and YAYB bases. According to the decoy-state method,[26] the total gain and quantum bit error rate (QBER) that Alice sends in ξA (ξA ∈ {XA, YA, ZA}) and Bob measures them in ξB (ξB ∈ {XB, YB, ZB}) in the decoy-state RFI QKD can be calculated by
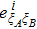
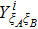

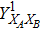
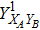

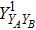


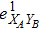

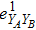


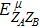
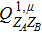
In practice, source errors and statistical fluctuations are inevitable issues in the security analysis of practical decoy-state RFI QKD systems. When considering source errors (for simplicity, we assume the vacuum source is precise which has no source errors), due to the imperfection of practical sources, the intensity of the pulses is not stable. That is to say, ε ranges from εL(δ) to εU(δ), where δ refers to the intensity fluctuations. Then, we can obtain the upper bound (

The other parameters 
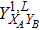
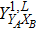

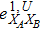
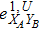

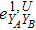
In order to explore the performance of the above decoy-state RFI-QKD scheme under practical experimental conditions, we use two kinds of light sources, e.g., WCS[3,4] and HSPS,[27,28] as examples and carry out the corresponding numerical simulations.
For the WCS, it has a Poisson distribution: 
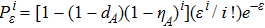
In all the simulation results presented below, we use the following parameters: ν = 0.01, ω = 0, Pμ = 1/2, Pν = Pω = 1/4, and PXA = PYA = PZA = PXB = PYB = PZB = 1/3. Moreover, we set the misalignment of the reference frames as β = π/7 (in fact, β is unknown and we just use it to simulate a practical RFI-QKD system). Other parameters used in the simulation are listed in Table
| Table 1. Simulation parameters for the three-intensity decoy-state RFI QKD with both source errors and statistical fluctuations. ηd (Y0) is the detection efficiency (the dark count rate) of Bob’s single photon detectors, ed is the probability that Bob’s single-photon detector is clicked incorrectly. α denotes the loss coefficient of the standard fiber link, γ is the number of the standard deviation when considering statistical fluctuations (here 5.3 corresponds to a failure probability of 10−7), and f is the error correction efficiency. ηA (dA) is the detection efficiency (the dark count rate) of Alice’s single photon detector with HSPS. . |
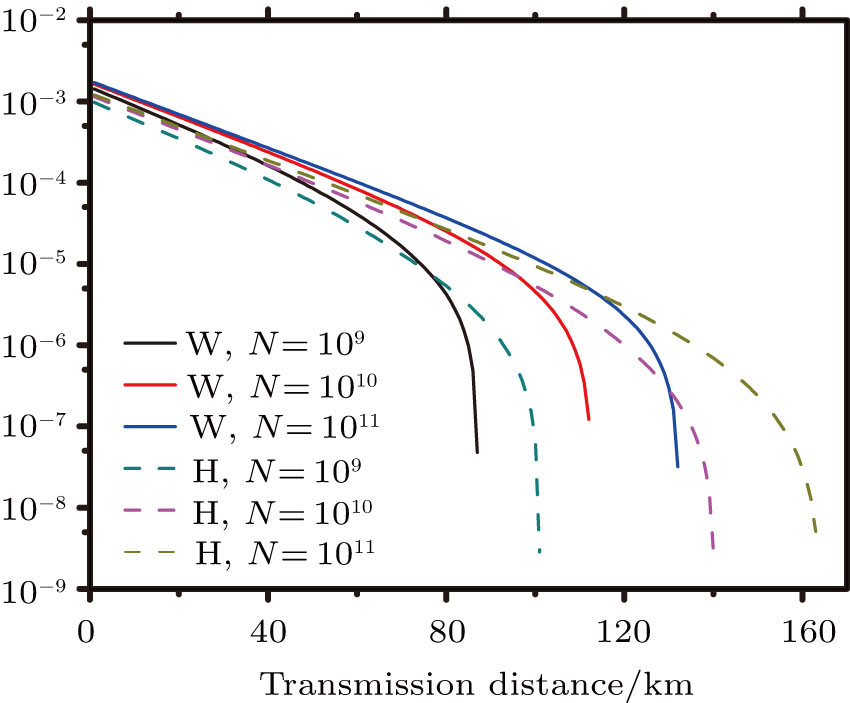
First, we study the performance of the decoy-state RFI QKD with standard statistical fluctuations, and the corresponding results are shown in Fig.
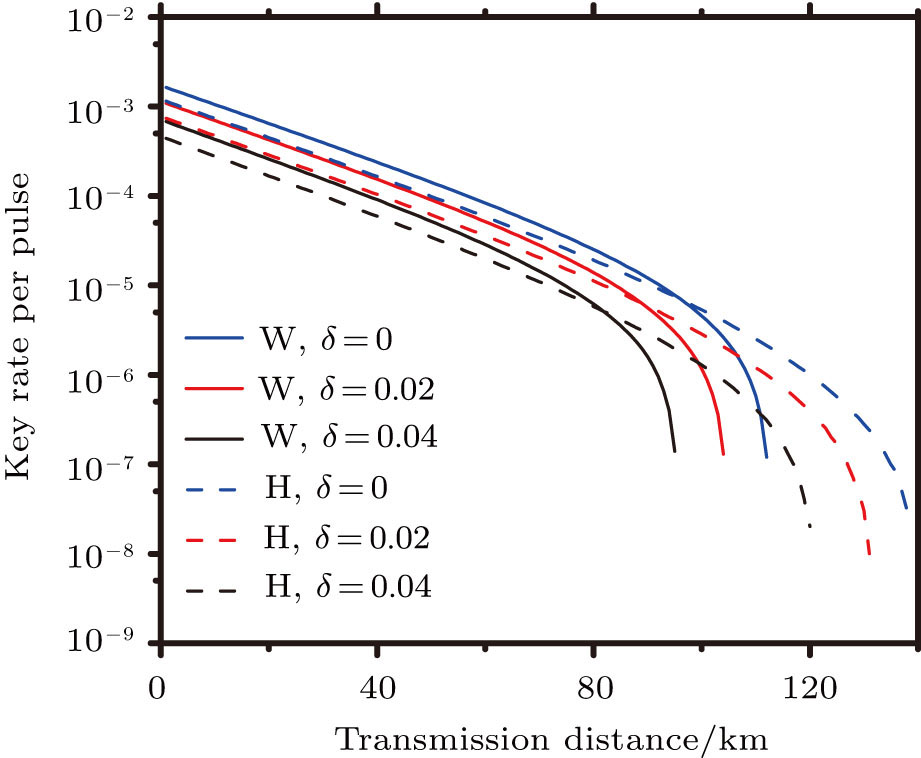
Then, we consider the effect of different source errors in the decoy-state RFI QKD with statistical fluctuations (N = 1010), and the simulation results are shown in Fig.
Finally, the optimal intensities of signal states and the corresponding key rates at 60 km with statistical fluctuations and with both statistical fluctuations and source errors are shown in Table
| Table 2. The optimal intensities of signal states and corresponding key rates at 60 km with statistical fluctuations. . |
| Table 3. The optimal intensities of signal states and corresponding key rates at 60 km with both statistical fluctuations and source errors. . |
In conclusion, RFI QKD can generate secret keys without alignment of reference frames, which exhibits obvious superiority in real-life QKD systems. Considering both source errors and statistical fluctuations, we studied the performance of the decoy-state RFI QKD with two kinds of practical sources, e.g., WCS and HSPS. Simulation results demonstrate that the secret key rates of the decoy-state RFI QKD with WCS are higher than those with HSPS in a short distance range, but the secret key rates of RFI QKD with HSPS outperform those with WCS in a long distance range. Our work will provide useful guidance in practical implementations of RFI QKD systems.
| [1] | |
| [2] | |
| [3] | |
| [4] | |
| [5] | |
| [6] | |
| [7] | |
| [8] | |
| [9] | |
| [10] | |
| [11] | |
| [12] | |
| [13] | |
| [14] | |
| [15] | |
| [16] | |
| [17] | |
| [18] | |
| [19] | |
| [20] | |
| [21] | |
| [22] | |
| [23] | |
| [24] | |
| [25] | |
| [26] | |
| [27] | |
| [28] | |
| [29] | |
| [30] | |
| [31] | |
| [32] | |
| [33] | |
| [34] | |
| [35] |