† Corresponding author. E-mail:
Shannon observed the relation between information entropy and Maxwell demon experiment to come up with information entropy formula. After that, Shannon’s entropy formula is widely used to measure information leakage in imperative programs. But in the present work, our aim is to go in a reverse direction and try to find possible Maxwell’s demon experimental setup for contemporary practical imperative programs in which variations of Shannon’s entropy formula has been applied to measure the information leakage. To establish the relation between the second principle of thermodynamics and quantitative analysis of information leakage, present work models contemporary variations of imperative programs in terms of Maxwell’s demon experimental setup. In the present work five contemporary variations of imperative program related to information quantification are identified. They are: (i) information leakage in imperative program, (ii) imperative multithreaded program, (iii) point to point leakage in the imperative program, (iv) imperative program with infinite observation, and (v) imperative program in the SOA-based environment. For these variations, minimal work required by an attacker to gain the secret is also calculated using historical Maxwell’s demon experiment. To model the experimental setup of Maxwell’s demon, non-interference security policy is used. In the present work, imperative programs with one-bit secret information have been considered to avoid the complexity. The findings of the present work from the history of physics can be utilized in many areas related to information flow of physical computing, nano-computing, quantum computing, biological computing, energy dissipation in computing, and computing power analysis.
From the early days of computers and computing processes, physics and computer fields have a long traditional straddling. The physics field considers computers as an engine. The engine which uses its energy to generate mathematical work and while doing this work it generates heat. This phenomenon can be shown in the equation below:
 |
In the present paper, the aim is to link the conventional and contemporary methods used for quantitative analysis of information leakage in imperative programs with the physics. For this purpose, the second principle of thermodynamics and Maxwell’s demon[1] has been used. Our aim is to show that even if system leaks information, the attacker has to do a certain amount of physical work to obtain leaked information. For this purpose, various experimental setups for Maxwell’s demon have been considered.
In physics, simple meaning of information has been considered, i.e., “information is any entity which you do not already know”.[2] To measure the information, Claude Shannon came up with the information entropy and information theory in 1948. He suggested that larger the information content, larger the entropy. To find the entropy of information, Shannon considered thermodynamic microstate of a computer system with a certain degree of freedom and came up with information entropy formula.
In computer science, to quantify information leakage in secure imperative programs, the non-interference property is also used along with the information theory. The non-interference policy is confidentiality policy which secure programs satisfy to protect the information. To satisfy non-interference property,[3] the computer system is divided into low-security sensitive input/output entities and high-security sensitive input/output entities. A system satisfies non-interference policy if any sequence of low input will produce the same low output regardless of the high input. Denning[4] first introduced quantitative information flow. Her work revealed that to quantify information leakage, change in uncertainty associated with information at different states needs to be considered. After that, a lot of work have been done to quantify information leakage in imperative programs using Shannon’s entropy and non-interference. In Refs. [5] and [6], quantitative analyses of information leakage in abstract computational systems have been studied using Denning’s principle. After that Clark, Hunt, and Malacaria Refs. [7] and [8] started quantifying information leakage in imperative programs with loops conditions and assignment statements. All the work related to quantification of information leakage in the imperative program was based on Shannon’s entropy formula. In some other cases like quantification of leakage in a multithreaded program, non-terminating program, mathematically derived variations of Shannon’s entropy formula was used. As a reason, the aim of the proposed work is to go back to the history and try to find the possible setup of Maxwell’s demon experiment for the mathematically derived variations of Shannon entropy formulas.
The benefit to revisit Maxwell’s experiment for various variation of Shannon entropy formula is it will relate physics and computer again. Solutions of many complex problems related to quantification of information flow can be thought of by physicist as well as computer scientists. Information flow security in quantum computing and nano-computing is also based on the Maxwell demon experiment. The proposed work may open the doors in that direction also.
In the present paper, five types of imperative programs have been derived. For these programs, mathematically and information theoretically derived variations of Shannon entropy formula have been used in literature. For these five types of contemporary imperative programs, the relation between quantitative analysis of information leakage and Maxwell’s demon principle will be derived. Not only possible Maxwell’s demon experimental setup but also the amount of minimal work required to keep secure content protected from the attacker will also be calculated. In other words, work required by the attacker to obtain the secret content from the imperative programs has been calculated. The five types of imperative programs in which variations of Shannon’s entropy formula have bees been used are as follow:
The quantification of information leakage in the simple imperative program has been described by Clark, Hunt, and Malacaria in Refs. [7] and [8].
To quantify information leakage in the imperative multithreaded program, scheduler effect also needs to be considered. In Refs. [9], [10], and [11] information leakage has been quantified in the imperative multithreaded program.
This method was first proposed by Tom Chothiya et al. in Ref. [12]. In this paper, a method has been proposed to find leakage between any two arbitrary points in the imperative probabilistic program. This method makes convenience to measure specific leaks in the program and it can be used to investigate information security of specific portion of the program.
In some programs or systems, secret contents are continuously generated as they execute repeatedly. In Ref. [13], Biondi et al. have quantified information leakage in such programs where secret content is infinite.
In this method, loosely coupled components provide services to other component and in this way information flow is generated. Thus, in SOA-based web services, interference is not only between high-security sensitive content and low-security sensitive content but also it is among secure content and low-security sensitive content and other architectural parameters.[14]
The motivation for this work has been explained in the subsection below.
Our motivation for the present work is in two-dimensional, one dimension is about computational physics and the second dimension is related to non-interference policy. In computational physics, two types of devices are described, i.e., logically reversible devices and logically irreversible devices. In the logically reversible devices, the inputs of the devices can be uniquely identified by observing their output, while in logically irreversible devices; inputs cannot be uniquely determined by observing their output. Some of the examples of logically irreversible devices are Boolean operations like AND, OR, and XOR.[15]
The physical devices relate observable outputs and inputs; similarly, non-interference policy relates observable (low-security sensitive contents) and secure content. In simple words, the attacker should not be able to know the secure content by observing output or observables of the system. Thus if we relate physical computation and non-interference, we can derive that the aim of the non-interference property is to convert the system or program into the irreversible system. But as described in Ref. [16], it is not possible to satisfy non-interference property completely in any system. At some point, low-security sensitive content and high-security sensitive content will always interfere. That means in computational physics terminology, at some point system will become logically reversible device and it can violate the second principle of thermodynamics as suggested by Rolf Landauer in 1961 in Ref. [17]. Landauer suggested that these “reversible” measurements could be used to sort the molecules and violating the Second Law. Our aim in this paper is to observe this logically reversible device when Maxwell demon experiment and Landauer’s principle is applied to them. And through this observation, study the non-interference property from a physical aspect. Thus, in short, the non-interference policy and Shannon’s entropy both are related to physics in one or the other way, that is, the hint which encourages us to study quantitative analysis of information leakage of various systems from thermodynamics and physics aspects. In the present work, the phenomenon of the reversible and irreversible systems has been in relaxed comparison to quantum computing. In quantum computing, the system is reversible only if all the prior states are physically achievable. In the present work even if the attacker is logically able to get the initial variable value or state after the execution of program then the program is considered as reversible in the present work.
Section
In this section, some of the concept relating physics and information are included. The physics and information theory is associated with each other because of the second principle of thermodynamics. The second principle of thermodynamics associates state function known as entropy S and states when the system undergoes transformation.[18] In simple words, the second principle of thermodynamics states that any system will absorb heat at temperature say T, and then if the system is irreversible then it will dissipate a certain amount of energy which can be used to do work.
Thus as per the second law of thermodynamics,
 |


 |
 |
In Eq. (
From Eq. (
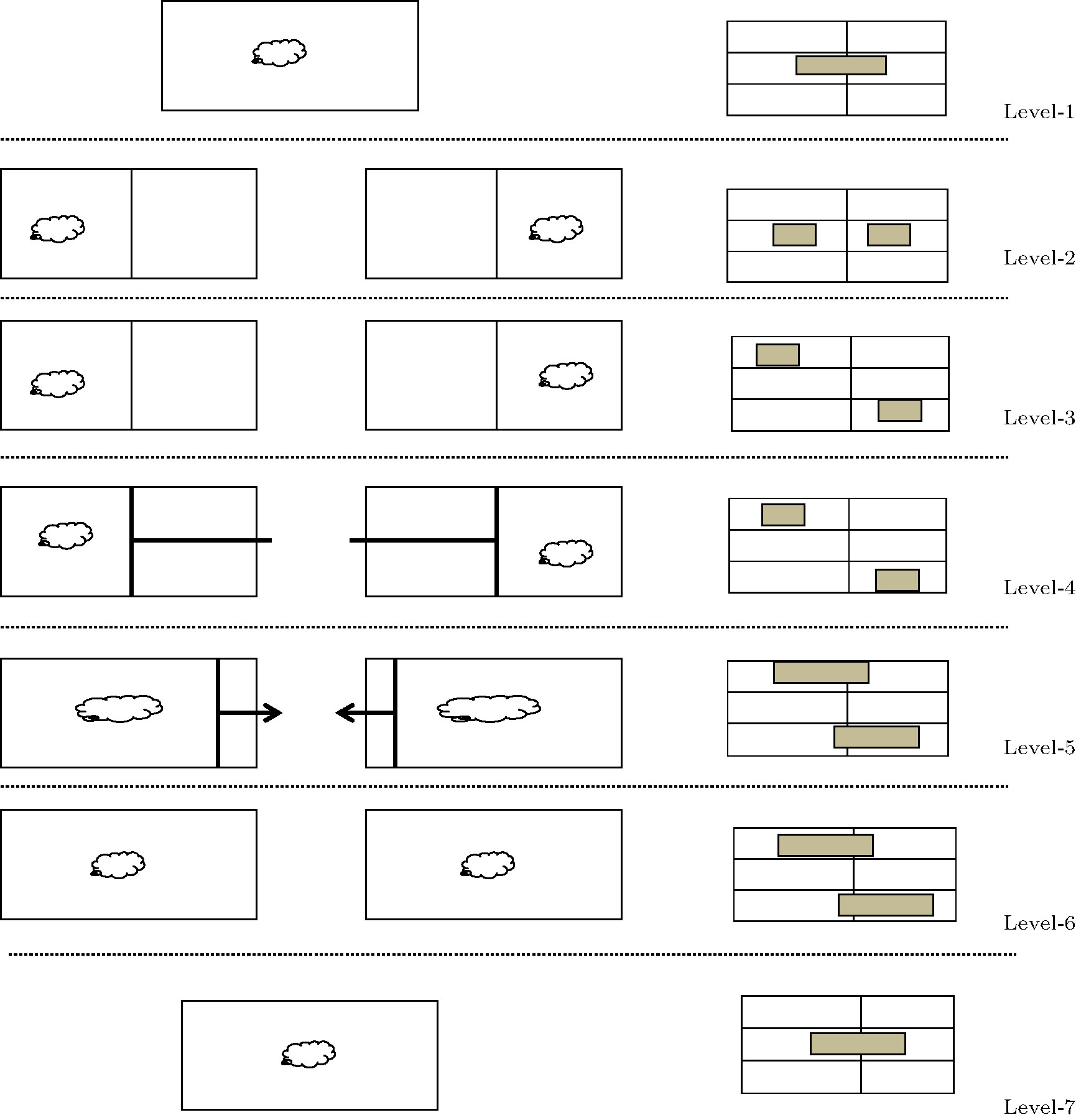
In a thought experiment, Maxwell considered a system with two neighboring chambers at the same temperature initially. The demon is an intelligent agent who can observe the molecules of gas in both the chambers. In both the chambers, some of the molecules will be moving faster than the average while some will be slower. The demon will be able to open and close the molecule size trapdoor available in the partitioning wall of two chambers and collect faster (hot) molecules in one chamber and slow (cold) particles in the other chamber. Maxwell suggested that this temperature difference can be used to create useful work. Based on Maxwell’s demon, simplified one molecule model was introduced in Refs. [19] and [20]. From a computational perspective, Bennet’s model of Maxwell’s demon has been described in Fig.
In Fig. 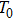

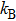
Due to the expansion, in level-6, the system will come to its original state. If the particle was on the left side then, the gas molecule will do the work and heat will flow into the reservoir. If the particle is on the right of the piston, then heat will flow from reservoir.[21] By observing heat of the reservoir, the attacker will be able to know that whether the particle was in the right chamber or the left chamber. In computer science terminology, it is similar to the situation where the attacker knows about the secret content by observing the outcome of the program after program execution due to a violation of non-interference. Because of this interference, previous state of high-security sensitive content will be known to the attacker by observing the output. That means, in the physical term, the system will be reversible.
Thus, Maxwell’s demon shows that how one-bit secret information can be leaked. Landauer suggested from Maxwell’s demon that to reset the information gained by an attacker, which means to make situation level-1 = level-7, work 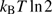

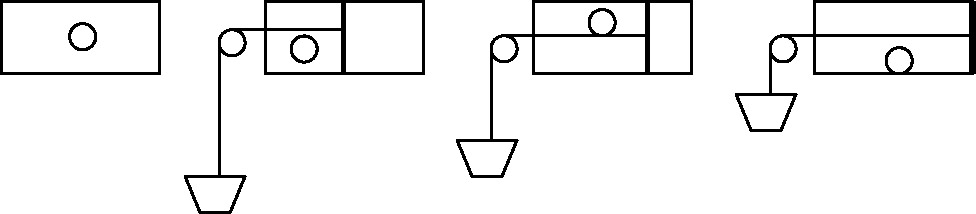
In Ref. [22], a similar experiment was done by including weight in the system to measure the work done by the system. Figure
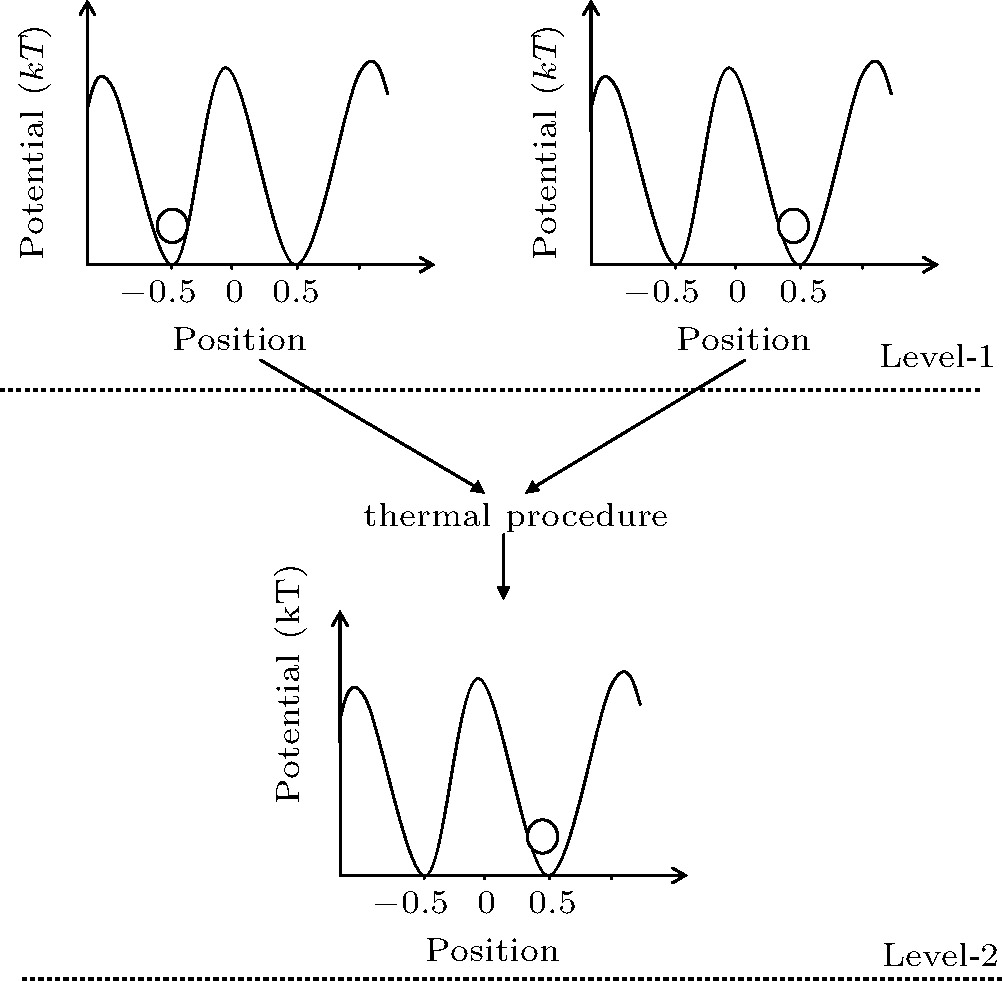
In Ref. [23], Bennett represented this concept using position versus potential graph. The graph is shown in Fig.
As shown in level-1 of Fig. 

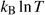
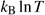

 |
From Eq. (
In the present work, we will demonstrate possible settings of Maxwell’s demon experiment for a practical imperative program like the simple imperative program, imperative multithreaded program, a probabilistic program with a point to point information leakage program, a program which generates infinite secret, and the program executes in SOA based architecture.
The quantitative analysis, based on Shannon’s entropy formula has been used widely these days to decide the threshold of the information leakage in the programs. The Shannon’s formula is derived from the second principle of thermodynamics and Maxwell’s demon experiment. So our aim in this paper is to go in the reverse direction and try to find how the experimental setup of Maxwell’s demon can be, for practical programs which have the secret of one bit. In this section, Maxwell demon’s experimental setup will be investigated for five types of program:
In the present work, the simple imperative program has been considered as a sequential program without loops. An example of simple imperative program snippet is as below:
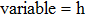

As shown in the snippet, h is high-security sensitive variable and o is observable. Assume that high-security sensitive variable h and observable o are one bit variable. In the second statement, the non-interference property is violated as high-security sensitive variable and observable interfere with each other. Thus, due to the second statement of the snippet, the program becomes reversible and violates the second law of thermodynamics as suggested in Maxwell’s demon experiment.
For these types of simple imperative programs, the setup of Maxwell’s demon experiment will be the same as shown in Fig. 

In simple terminology, multithreading is the ability of processor with a single core or multiple cores to execute more than one thread using the scheduler in such a way that it appears to the user that threads are being executed concurrently. In the present paper, it has been assumed that multithreaded programs are executed on a single core or a single processor with the help of scheduler. In Refs. [9], [10], and [11] methods to quantify information leakage are provided. The scheduler in multithreaded program assigns the probability to the thread for execution and based on probability it picks up a thread for execution. Information leakage in the multithreaded program depends on the sequence in which threads are picked up by the scheduler for the execution. An example of the imperative multithreaded program is as follows:
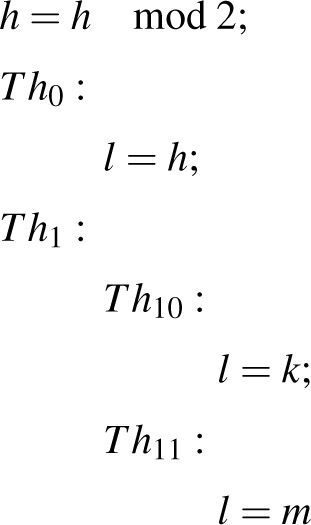
As shown in the example, h is high-security sensitive variable while l, k, and m are low-security sensitive variable. It has been assumed here that all variable, i.e., h, k, l, and m are one-bit variables. For this imperative multithreaded program, the scheduler will assign the probabilities to threads 

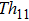
From physics perspectives, if we want to design Maxwell’s demon experiment then effects of scheduler need to be considered. To consider scheduler effect, probability needs to be included in Maxwell demon experiment. The probability was included in this experiment by Malacaria and Smeraldi in Ref. [18]. In the experiment Malacaria and Smeraldi assumed that there is more than one system in the experiment and particles are found in two chambers of the systems with probability 

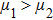

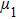

As shown in Fig. 
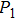
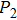
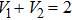

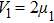
Thus, from thermodynamics perspectives, work done by this system can be calculated as
 |
Thus, the attacker needs this much work to know about the secret in the multithreaded program which executes under the effect of scheduler. Similarly, for n systems, the above case is generalized and calculated work done is provided below. Detailed calculation of work done by n-state system is provided in Ref. [18]. It is
 |
In this method of quantification, the simple imperative program has been considered but leakage has been calculated between any two arbitrary points in the imperative program. In Ref. [12], this type of information leakage model has been discussed. In the paper, leakage in practical JAVA programs has been quantified. One similar example of an imperative program is given below:
Program-1
End
As shown in the program there are five statements. Aim here is to find leakage between any two statements. The interference between high-security sensitive variable and low-security sensitive variable may be or may not be between selected arbitrary points of the program. For example, in the above code snippet, interference is in statement-3. If statement-1 and statement-2 are selected to quantify leakage then it is possible that quantified leakage is zero. In the above program, it is assumed that high-security sensitive variable is of one bit.
The setup of Maxwell’s demon experiment for this program will be hypothetical in nature. The setup is shown in Fig.
 | Fig. 5. Experimental setup of Maxwell’s demon experiment to quantify point to point information leakage in imperative program. |
As shown in the figure, volumes of chambers are 

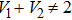
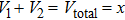
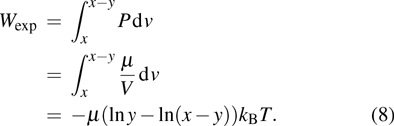 |
Thus, the attacker needs to do minimum work 
The quantitative analysis successfully measures the protection of secure content in the system but till 2014, it was assumed that secret and observations produced by the system are finite. But in 2014, Biondi et al. suggested in Ref. [13] that there can be programs or systems which can generate infinite secret and observables. In Ref. [13] method to quantify information leakage in such program was also provided. For example, consider the code snippet from Ref. [13] is provided below.

In the code snippet, variable h is high-security sensitive variable. If the value of variable h is zero then program will produce a string of infinite zeros and ones with same probability, i.e., 0.5. If the value of h is 1 then zero will be produced with probability 0.75 and 1 will be produced with probability 0.25. Thus as shown in the code snippet, it generates infinite observable. The attacker will observe the behavior of some observable and based on that he will try to guess the value of high security sensitive variable h. It is clear for the above code snippet that after some iteration, leakage will be entire variable h, i.e., 1 bit.
The setup of Maxwell’s demon experiment for programs which generate infinite observable is shown in Fig.
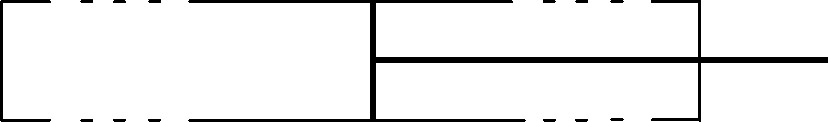 | Fig. 6. Experimental setup of Maxwell’s demon experiment to quantify information leakage in imperative program which generates infinite observables. |
As shown in the figure, hypothetical experimental setup of Maxwell demon experiment needs to be considered in this case. Both the chambers shown in Fig.
Here volume of both the chamber is infinite. Thus 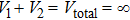
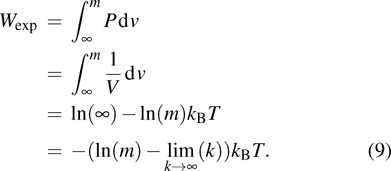 |
At volume m, an attacker may know the secret. In Ref. [13] equation 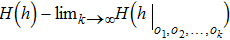
SOA is an architectural solution which provides loose coupling of services through the orchestration of service components. In the case of an SOA-based program, information leakage will not be just because of interference among the low-security sensitive and high-security sensitive variables but other architectural parameters will also play a crucial role in the quantification of information leakage. The detail about the SOA and attacks related to SOA are discussed in detail in Refs. [24] and Refs. [14] and [25] respectively. In SOA, the parameters like network link will be outside of the closed system. Thus in the SOA-based web services and programs, non-interference property needs to be considered in a global way. In this SOA-based structure, interference is not only between the high variable and low variables but all other architectural factors. In the SOA-based systems, the architectural parameters like the effect of link failure also needs to be considered which interfere with secure content.
The setup of Maxwell’s demon experiment will be very similar to the one shown in Figs.
From analysis of various experimental setups it can be concluded that at present, information security policies based on non-interference policy of various types of programming scenario were just an extension of Maxwell demon experimental setup. But for cloud computing and SOA-based system, this conventional variations of Maxwell demon experimental setup will not work due to decoherence. To eliminate decoherence, computer scientists and physicists have to do combined efforts. In Ref. [26], Anjaria and Mishra have considered non-interference policy globally and quantified the leakage. This can be considered as a way to mitigate decoherence.
From the second law of thermodynamics, in 1879, Rudolph Clausius[27] suggested that spontaneous processes have preferred direction and this direction is from hotter body to cooler body. In deriving information theory and entropy, Shannon took help of this fact represented by Rudolph. Shannon first believed that information and the second law of thermodynamics can be related but then he focused on very important questions: Just like mechanical systems, is it possible to get knowledge about the work done by the system by observing states of the system only? In the question, work done can be considered as minimal work required protecting the secret content. The answer to the above question was found from the concept of Maxwell’s demon. This famous concept of Maxwell’s demon was represented by Maxwell. The history of the experiment is available in Ref. [28].
Lio Szilard converted Maxwell’s demon experiment into single molecule based Maxwell’s demon experiment in Ref. [19]. This same single molecule-based experiment has been used in the paper to explain the relation between quantitative information and thermodynamics. Like Maxwell, Szilard also represented thought experiment only. In 1961, Landauer suggested in Ref. [17] that erasure of information in single molecule system or single bit information system is a dissipative process. In Ref. [29], Berut et al. represented actual experimental set up to verify Szilard and Landauer’s principle. In Ref. [29], Berut et al. used a system of a single colloidal particle, trapped in a modulated double-well potential to verify thought experiment represented by Szilard and Landauer.
The logical explanation for the presence of demon and why demon will not be able to break the second law of thermodynamics was presented by Bennett and Oliver Penrose in Refs. [23] and [30] respectively. Bennett and Oliver Penrose argued that presence of demon and resetting of demon’s memory to initial place will dissipate heat. Landauer suggested in Refs. [17] and [31] that resetting of memory always dissipate heat. From Landauer’s argument, Bennett and Oliver calculated and explained that due to this heat dissipation, the demon will not be able to violate the second principle of thermodynamics. Thorough and state of the art survey of thermodynamics and information is discussed in Ref. [2] by E Lutz and Sergio C State of the art survey of the relation between thermodynamics and information in provided in Ref. [32] by Juan et al.
The Maxwell’s demon, Landauer and Bennett’s principles have been widely used in mechanics, computer science, and statistics. In Ref. [33], John T and Craig L provided quantum dot cellular automata model of Maxwell’s demon. This automata model is very useful to study computation and energy dissipation in computing. In Ref. [34], Mandal and Jarzynski proposed information processing solvable model of Maxwell’s demon which can be used in computation and mechanics widely to model the work and energy dissipation. In Refs. [18] and [35], Malacaria and Smeraldi successfully attempted to relate secure computing, confidentiality, quantitative analysis of information and physical process and systems. Malacaria and Smeraldi argued using thermodynamics that any computing system whose final state is observable must dissipate 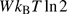
Once the fundamental relationship was established between information and thermodynamics, an attempt has been made in the present paper to relate recent trend in confidentiality and information quantification with thermodynamics. In the present work, minimal work required by an attacker to gain confidential information is also calculated for five cases, i.e., information leakage in imperative program, imperative multithreaded program, point to point leakage in imperative program, imperative program with infinite observation, and imperative program in the SOA-based environment. The possible experimental setup of Maxwell’s demon was also described for each of the five cases. Although at first possible experimental setups of Maxwell’s demon look impractical, in Ref. [29], the simple experimental setup has already been proposed. So in future, setup of other variations of this experiment may also be possible.
At present, we make no claims about practical implications of the proposed method in any specific field but in future, this work will be helpful to find many unanswered questions in the fields of computation energy dissipation, quantitative analysis, and information secrecy. The present work will also help to understand confidentiality in quantum computing. The work can be related in the future with nano-computing and technology, molecular, and biological computing fields. This work bridges the computer science and physics so that physicist and computer scientists can together solve some complex problems in information flow security and quantitative analysis of information leakage.
| [1] | |
| [2] | |
| [3] | |
| [4] | |
| [5] | |
| [6] | |
| [7] | |
| [8] | |
| [9] | |
| [10] | |
| [11] | |
| [12] | |
| [13] | |
| [14] | |
| [15] | |
| [16] | |
| [17] | |
| [18] | |
| [19] | |
| [20] | |
| [21] | |
| [22] | |
| [23] | |
| [24] | |
| [25] | |
| [26] | |
| [27] | |
| [28] | |
| [29] | |
| [30] | |
| [31] | |
| [32] | |
| [33] | |
| [34] | |
| [35] |