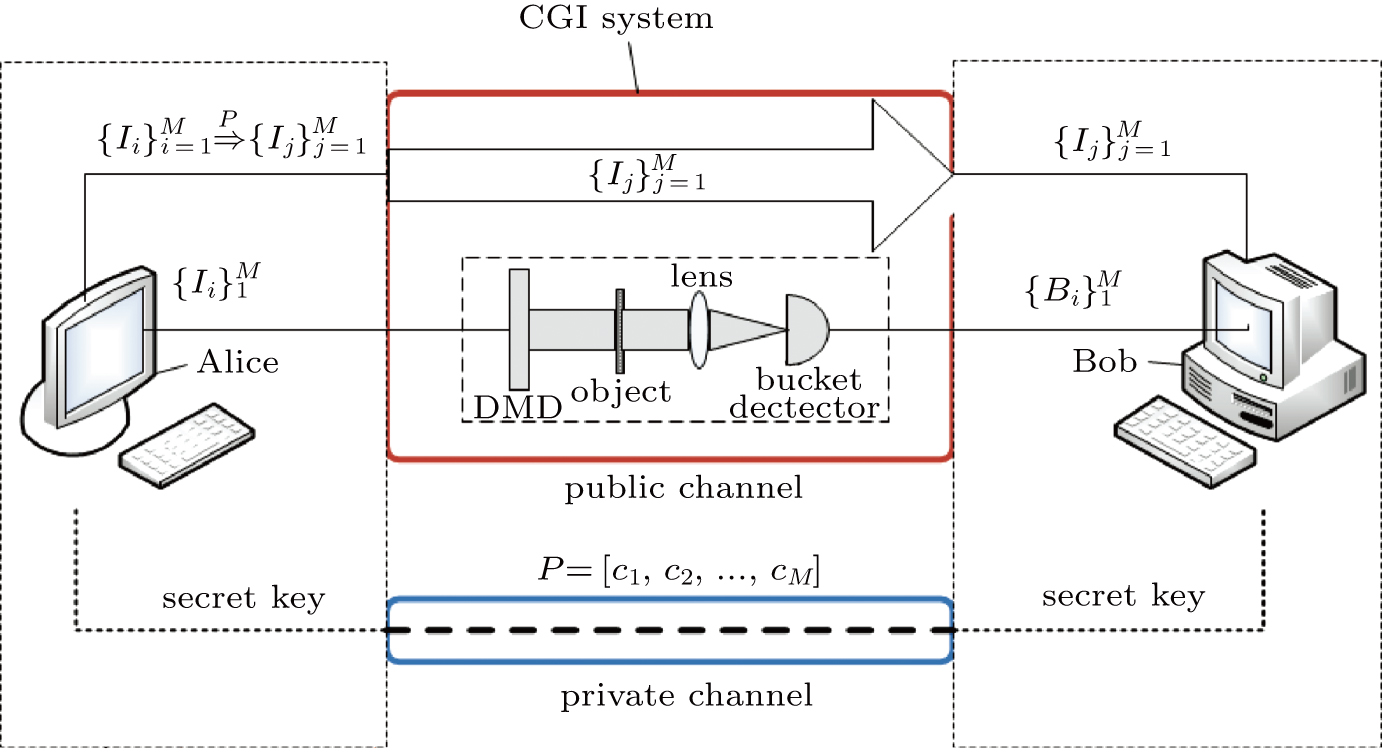
Optical encryption scheme based on ghost imaging with disordered speckles
(color online) Schematic diagram of the proposed encryption scheme with CGI system. The detection results from the object and the disorderly speckle patterns are transmitted to users by a public channel, meanwhile, the secret key, the permutation P for the disorderly speckle patterns, is transmitted to the authorized users by a private channel.