An image encryption scheme based on three-dimensional Brownian motion and chaotic system
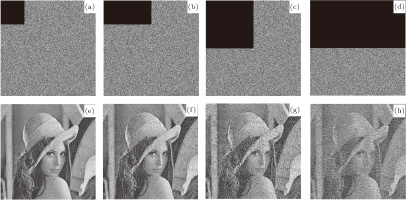
(color online) Occlusion attack analysis results of the cipher images with (a) 1/16, (b) 1/8, (c) 1/4, and (d) 1/2 occlusion, and recovered images with (e) 1/16, (f) 1/8, (g) 1/4, and (h) 1/2 occlusion.