An image encryption scheme based on three-dimensional Brownian motion and chaotic system
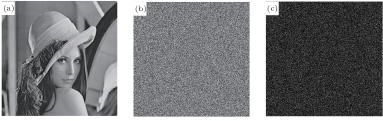
Decryption results with different keys, showing (a) recovered image with K, (b) recovered image with K
1, and (c) subtraction of Fig.
An image encryption scheme based on three-dimensional Brownian motion and chaotic system |
|
Decryption results with different keys, showing (a) recovered image with K, (b) recovered image with K
1, and (c) subtraction of Fig. |
 |