Quantum hacking of two-way continuous-variable quantum key distribution using Trojan-horse attack
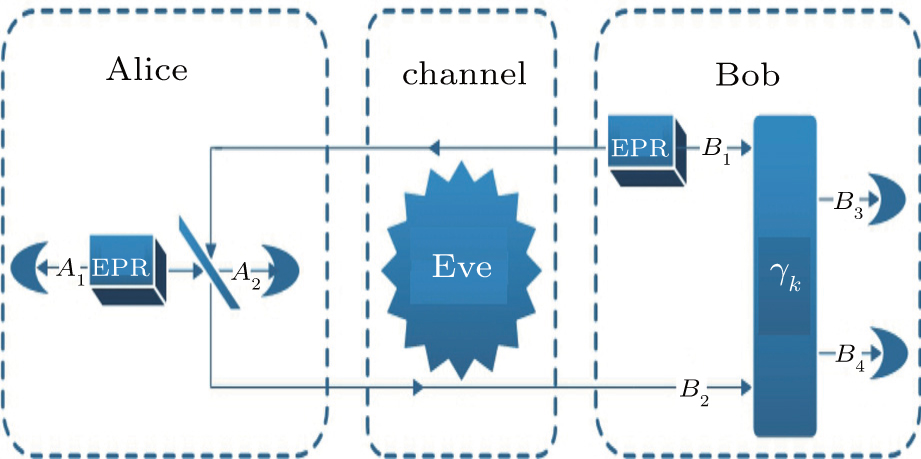
The equivalent scheme to figure 1 with post processing when Alice is switched ON.
Quantum hacking of two-way continuous-variable quantum key distribution using Trojan-horse attack |
The equivalent scheme to figure 1 with post processing when Alice is switched ON. |
 |