† Corresponding author. E-mail:
Project supported by the National Basic Research Program of China (Grant No. 2013CB338002) and the National Natural Science Foundation of China (Grant Nos. 11304397 and 61505261).
We present a Trojan-horse attack on the practical two-way continuous-variable quantum key distribution system. Our attack mainly focuses on the imperfection of the practical system that the modulator has a redundancy of modulation pulse-width, which leaves a loophole for the eavesdropper inserting a Trojan-horse pulse. Utilizing the unique characteristics of two-way continuous-variable quantum key distribution that Alice only takes modulation operation on the received mode without any measurement, this attack allows the eavesdropper to render all of the final keys shared between the legitimate parties insecure without being detected. After analyzing the feasibility of the attack, the corresponding countermeasures are put forward.
Quantum key distribution (QKD)[1] enables two authenticated users, Alice and Bob, to share secure private keys in the presence of eavesdroppers. Quantum physics allows for unconditionally secure communication through insecure communication channels. The QKD protocols are classified into two main classes: discrete-variable (DV)QKD[2–5] and continuous-variable (CV) QKD,[6–10] both of whose unconditional security have been proved in theory.[11–14] The first proposed QKD protocol[2] is based on discrete variables, such as the polarization of a single photon. In CVQKD, the information is encoded on the continuous variables, such as the position or momentum quadratures of coherent states. In recent years, CVQKD has received close attention in the research area of quantum communication. One of the most outstanding CVQKD protocols is the Gaussian-modulated coherent state protocol,[9] whose composable security has been fully proven.[15] This protocol has been experimentally demonstrated both in laboratory[16,17] and field tests.[18] In the last few years, the high-speed CVQKD has been experimentally demonstrated,[19] and the high-bit-rate CVQKD system over 50-km fiber channel has successfully passed the field tests.[20] Moreover, a recent work shows that the secure transmission of CVQKD can be extended to 150 km.[21]
In comparison to DVQKD, CVQKD has some advantages. On one hand, the modulation of continuous variables relies on Gaussian modulation of the light field quadratures, which is a mature technology in experiment. On the other hand, CVQKD can achieve higher detection efficiency, which may lead to higher bit rate of the secure key. Furthermore, most of the operation in CVQKD can be implemented efficiently by standard telecommunication networks and technologies that are currently available and in widespread use, which means CVQKD can be integrated into the current telecommunication networks by using well-established optical fiber networks and practical devices.
In spite of the above advantages, the general one-way CVQKD still has serious shortcomings. In the case of direct reconciliation, GG02 protocol has the limitation of 3 dB,[9] which means there is no secret key when channel attenuation exceeds 3 dB. Although people put forward the post-processing[22] and reverse reconciliation[16] method to overcome 3-dB limit, the problem that one-way CVQKD is susceptible to excessive noise has not yet been resolved. No matter if there is direct reconciliation or reverse reconciliation, secret key rate will be affected by excess noise obviously, which severely restricts the security transmission distance. In order to enhance the tolerable excess noise, Stefano Pirandola[23] first proposed the two-way CVQKD protocol, which overcomes 3-dB limit and tolerates more excess noise than one-way protocols. Furthermore, Alice only needs one modulator in the two-way CVQKD protocol, which makes the hardware requirements on Alice’s side in two-way CVQKD protocol lower than the one in one-way protocol. This characteristic gives the two-way CVQKD protocol a unique advantage in the situation in which Alice can only equip a small number of devices.
Recently, breakthrough progress has been made the in the security analysis of the two-way CVQKD protocol in theory. Carlo Ottavini[24] proved the security of the two-way CVQKD protocol under coherent attacks in direct reconciliation. However, the practical QKD systems have imperfections that cannot satisfy the assumptions of ideal devices in theoretical security proofs. The imperfect devices in commercial quantum key distribution systems open security loopholes that an eavesdropper may exploit. In the two-way CVQKD protocol, Alice only takes modulation operation on the received mode without any measurement. Moreover, the modulator has a redundancy of modulation pulse-width in the practical system, which leaves loopholes for Eve to take an attack strategy. Based on the above two factors, we propose a Trojan-horse attack strategy on the two-way CVQKD protocol, which allows the eavesdropper to render all of the final keys shared between the legitimate parties insecure without being detected. We discuss the feasibility of this attack and suggest countermeasures to prevent such an attack.
The paper is organized as follows. In Section 2, the general two-way CVQKD protocol is briefly introduced followed by the proposed Trojan-horse attack strategy on the two-way CVQKD protocol in Section 3. In Section 4, the feasibility of the Trojan-horse attack strategy is analyzed in detail and the corresponding countermeasures are put forward. The conclusion is drawn in Section 5.
In the one-way CVQKD protocol, the quantum states encoding information is always sent by Alice and detected by Bob after passing through the quantum channel, where the signal source is only controlled by Alice. The two-way CVQKD protocol proposed by Stefano Pirandola broke the fixed thinking that the signal source should only be controlled by Alice, where the signal sources are symmetrically distributed on both sides of Alice and Bob. In their protocol, Bob initially sends a mode to Alice and Alice encodes her information by applying a random displacement operator to the received mode and sends it back to Bob, where Bob detects both his original mode and the received mode to decode Alice’s modulations.
The procedure of implementing the general two-way CVQKD protocol with homodyne detection is illustrated in Fig.
 | Fig. 1. The entanglement-based (EB) scheme of general two-way CVQKD protocol with homodyne detection. |
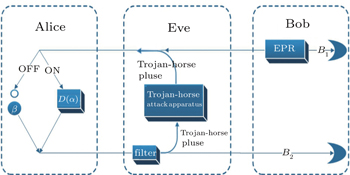
Our attack mainly focuses on the imperfection in the practical system that the modulator has a redundancy of modulation pulse-width and the unique characteristics of two-way CVQKD systems that Alice only takes modulation operation on the received mode without any measurement. By implanting a Trojan-horse pulse, our proposed attack strategy can partially or fully obtain the information transmitted between the two legal communication sides without being detected. Our attack strategy can be divided into two parts, which is illustrated in the Eve part of Fig.
Here we need to note that the security of the general two-way CVQKD protocol against coherent attacks can be achieved by switching randomly between one-way (switch OFF, where Alice detects the incoming mode and sends a new state back to Bob) and two-way schemes (switch ON),[23] as shown in Fig.
According to the attack steps and the loophole which is utilized, the feasibility of the Trojan-horse attack strategy is mainly based on the following three factors.
Firstly, in two-way CVQKD systems, Alice only takes modulation operation on the received mode without any measurement. Therefore, the Trojan-horse pulse implanted by Eve can smoothly enter the modulator of Alice’s side without being detected. Secondly, for the convenience of operation in practical experiments, the modulation pulse-width of the modulator is always larger than the pulse-width of each signal pulse. Eve can make full use of the redundancy of modulation pulse-width to make the Trojan-horse pulse receiving the same modulation process as the original signal pulse, which is the linchpin of successfully eavesdropping the key information. Finally, throughout the attack process, Eve does not take any measurement operation on the original quantum signal, which means that Eve’s behavior will not introduce any excess noise under ideal conditions.
According to the above three factors, we can conclude that Eve’s attack cannot be detected by Alice and Bob. Meanwhile, the information hacked by Eve cannot be eliminated by Alice and Bob through the reconciliation and privacy amplification. Thence, the Trojan-horse attack strategy allows the eavesdropper to render all of the final keys shared between the legitimate parties insecure without being detected.
However, in practical operations, the added Trojan-horse pulse and original signal pulse may have crosstalk, which may affect the final secret key rate. In order to judge the attack impact of our Trojan-horse attack strategy, we need to quantitative describe the effect of crosstalk between the Trojan-horse pulse and original signal pulse. For simplicity in security analysis, we replace Alice’s displacement operation with a beam splitter and EPR pairs,[26] which has been illustrated in Fig. 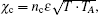
The Gaussian attack is optical in the security analysis of two-way CVQKD protocol as the corresponding covariance matrix of the state B2B1A2A1 is known to Alice and Bob.[27] In the following security analysis, we note that the Eve mentioned is the one taking Gaussian collective attack instead of the one taking Trojan-horse attack.
In Fig.

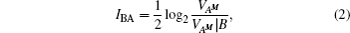
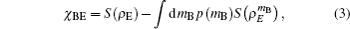

Since the state ρB2B1A2A1E is a pure state,
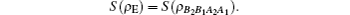
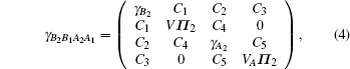
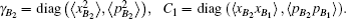
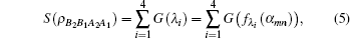
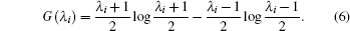
For simplicity to calculate the final key rate, we apply a symplectic transformation γk to the modes B2 and B1, obtaining the modes B4 and B3, which is illustrated in Fig.

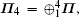
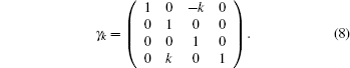
As the symplectic transformation γk does not change the von Neumann entropy of the state ρB2B1A2A1, Eve’s von Neumann entropy and conditional von Neumann entropy on Bob in Fig.

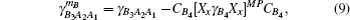
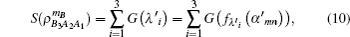
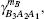
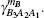
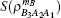
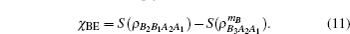
Then the final key rate is obtained
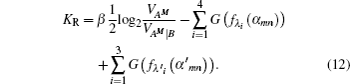
In practice, Alice and Bob calculate αmn and α′mn by measuring the variance quadratures of the mode B2, B1, A2, A1. For simplicity, we assume that the forward and backward channels are independent and linear with the same transmittances T. The noise referred to the input is χ1 = (1 − T)/T + ε, where ε is the channel excess noises referred to the input. Because we assume the crosstalk between Trojan-horse pulse and original signal pulse as the noise introduced into the backward channel, which is formulated as 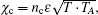
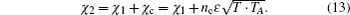
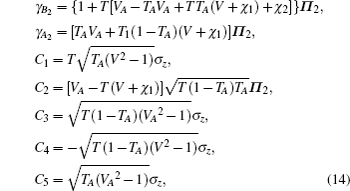
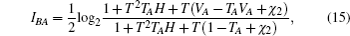
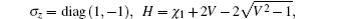
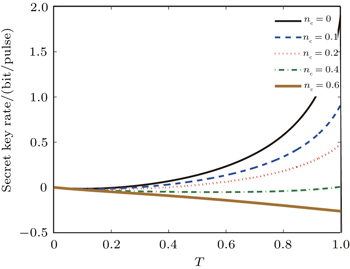
When nc = 0, there is no crosstalk between the Trojan-horse pulse and original signal pulse, which means that the operation of Trojan-horse attack does not introduce any excess noise in the communication. Figure
From Fig.
To prevent the Trojan-horse attack, the most efficient way is monitoring and removing the Trojan pulse. In one-way CVQKD system, installing isolators and wavelength filters on Bob’s side have been the most suitable countermeasures against Trojan-horse attack.[33,34] However in the two-way CVQKD system, the former one cannot be used, which will hinder the normal communication. But the latter one can certainly be useful. Therefore, the technical countermeasure specifically for the two-way CVQKD system is as follows: Bob implants a tag frame into the original signal pulse every time interval t, and a waveform detector is added before the modulator on Alice’s side, which is used to detect the tag frames. When the signal pulse passes through the waveform detector, Alice records the time interval between every two adjacent tag frames. If the time interval is t, the pulse between the two tag frames is reserved into the modulator; otherwise, the pulse is removed. This countermeasure can effectively eliminate the Trojan pulse, but it will also increase the complexity of the devices on Alice’s side, which weakens the superiority of two-way CVQKD system.
In conclusion, the Trojan-horse attack on the two-way CVQKD system is proposed by inserting a Trojan-horse pulse into the original signal pulse. If the legitimate users do not take any necessary countermeasures, the final secret key will be totally insecure under this attack, where the attacker can obtain all the information about the final key without being detected. After analyzing the feasibility of the attack, we give the limitation of successfully carrying out the attack. Finally, a technical countermeasure is provided to resist the Trojan-horse attack on the two-way CVQKD system.
| 1 | |
| 2 | |
| 3 | |
| 4 | |
| 5 | |
| 6 | |
| 7 | |
| 8 | |
| 9 | |
| 10 | |
| 11 | |
| 12 | |
| 13 | |
| 14 | |
| 15 | |
| 16 | |
| 17 | |
| 18 | |
| 19 | |
| 20 | |
| 21 | |
| 22 | |
| 23 | |
| 24 | |
| 25 | |
| 26 | |
| 27 | |
| 28 | |
| 29 | |
| 30 | |
| 31 | |
| 32 | |
| 33 | |
| 34 |