† Corresponding author. E-mail:
Project supported by the National Natural Science Foundation of China (Grant Nos. 61272495, 61379153, and 61401519), the Research Fund for the Doctoral Program of Higher Education of China (Grant No. 20130162110012), and the MEST-NRF of Korea (Grant No. 2012-002521).
We investigate the design of anonymous voting protocols, CV-based binary-valued ballot and CV-based multi-valued ballot with continuous variables (CV) in a multi-dimensional quantum cryptosystem to ensure the security of voting procedure and data privacy. The quantum entangled states are employed in the continuous variable quantum system to carry the voting information and assist information transmission, which takes the advantage of the GHZ-like states in terms of improving the utilization of quantum states by decreasing the number of required quantum states. It provides a potential approach to achieve the efficient quantum anonymous voting with high transmission security, especially in large-scale votes.
Quantum cryptography has arisen over the last decades centering on the manipulation of individual quanta of information, known as quantum bits or qubits.[1,2] Based on physical laws instead of mathematical complexities, communication with perfect secrecy can be guaranteed in an insecure channel in Vernam’s sense of one-time pad known as quantum cryptography.[3,4] Quantum entanglement (QE)[5,6] is one of its characteristics which plays a greatly vital role in quantum cryptography. It reflects the relevance of quantum bits, which has won the support of the local hidden-variable theory. Quantum cryptography is widely used in many active fields such as quantum signature, secret sharing, voting, and so on.[7–9]
Voting is a behavior that often takes place in democratic society. The traditional voting would not well meet the present voting demands because of its weakness, such as low efficiency and insecurity. With the development of network and cryptography techniques,[10] electronic voting (E-voting) arises at a historic moment. Based on cryptography, E-voting requires computers and networks to realize voting functions. E-voting also has the advantages of high efficiency, convenience and flexibility, which has been applied to several research areas.[11–13] With the continual expanding of ballot activities, scholars all over the world are actively exploring and designing secure ballot schemes. However, E-voting schemes could be easily broken by the emergence of quantum computers. Thus quantum cryptography can be applied in voting to realize the unconditional security and detectable eavesdropping,[14] which brings both challenges and opportunities to ballot protocols. In particular, the unique physical characteristic QE arouses wide concern, and how to apply it in ballots to design more secure and stable quantum ballot schemes has become an important issue in secure communications. Hillery et al. presented a fair voting protocol based on quantum resources.[15] Vaccaro et al. introduced kinds of quantum protocols for anonymous voting and their surveying.[16] Shi et al. proposed a quantum distributed ballot scheme based on Greenberger–Horne–Zeilinger (GHZ) state.[17] Those proposals are all of importance in the situations that the identity of the person who sends the message should be secret.[18–20] Unfortunately, there are still challenges for the security if talking of collaborating parties cannot be prohibited, the voting message of each individual voter may be learnt by the tallyman or the other voters.
The quantum cryptography with continuous variable (CV)[21,22] has the strength of security and high efficiency.[23,24] The CV-based quantum voting protocols were proposed,[25] which employed Einstein–Podolsky–Rosen (EPR) pairs to serve as information carrier and introduced a new idea of utilizing CV quantum states during the voting procedure. It demonstrates that CV-based quantum cryptography can improve the practicality of quantum voting. The protocols of Ref. [25] can not only bring the conception of CV quantum voting but also offer us more opportunities to study more efficient voting schemes. Considering the voting efficiency, we suggest anonymous communications[26] and two quantum anonymous voting protocols (QAVP) based on a quantum cryptosystem with multidimensional CV, in which CV-based GHZ-like states[27–30] are applied as information carriers. The GHZ-like states employed as voting states in this paper consist of momentum-squeezed and position-squeezed modes. All the modes are taken advantage of in the voting process, which indicates that the proposed protocols can not only guarantee the security of communications but also improve the voting efficiency by decreasing the required consumption of GHZ-like states. The remainder of this paper is organized as follows. Section 2 introduces QAVP with continuous variable entangled states (CVES). The security and efficiency are analyzed in Section 3 respectively. Finally, the conclusions are drawn in Section 4.
First, the QAVP should obey the following principles:
Then a CVES-based quantum voting scheme and two improved protocols with modified operators are introduced respectively.
To satisfy the above-mentioned principles, we start with a fundamental QAVP, which can be divided into two parts, i.e., the preparation and voting phase, and measurement of the final states.
During the voting procedure, the tallyman cannot gain any information about the individual votes from voters, which can be achieved by utilizing an entangled state to carry the voting information. With a map S, the CV-based GHZ-like state[31] with three modes (1, 2, and 3) serving as the information carrier can be expressed in Heisenberg operators, i.e.,
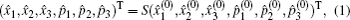


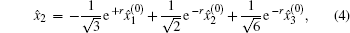

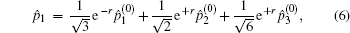
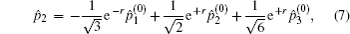
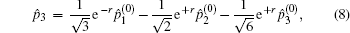
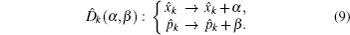
Suppose two candidates Alice and Bob are involved, and n voters participate in the voting process. Then the voting phase depicted in Fig.

The tallyman’s duty is to measure the final state to obtain the voting result, that is, the number of each kind of votes should be published. The tallyman can implement measurements on different final states where the voting with position operations differs from that with momentum operations. Next, two kinds of measurements, position measurement and momentum measurement are discussed.
However, there is a situation where some participants may cheat or give up voting, which cannot be ignored. Thus two improved protocols are presented as follows.
A modified displacement operation on mode 2 and mode 3 is applied to propose two improved voting protocols, i.e., a simple binary-valued ballot protocol with two candidates and multi-valued ballots with m candidates. Thus a refined displacement operator can be expressed as
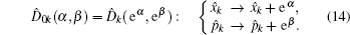
The binary-valued ballot is a special case of anonymous voting, in which the vote is required to be a binary natural number. This binary-valued ballot is considered beneficial for the vote procedure involving two candidates (Alice and Bob), and each voter can vote for just one of them. Quantum anonymous voting is involved in the binary-valued ballot as well. Either the position-squeezed mode or momentum-squeezed mode could serve as an ideal voting mode. Since the above-mentioned measurements are relatively similar, only the position-squeezed mode is taken into consideration in this part. This voting process presented in Fig.
 | Fig. 2. The improved binary-valued ballot with the CV-based GHZ-like state. j ∈ {1,2,3…,n} and k ∈ {2,3}. |

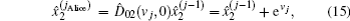




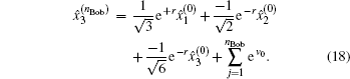
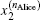
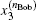
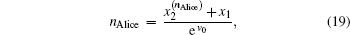


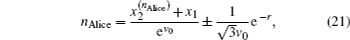



Another ballot, multi-valued ballot is introduced, in which voters have m (m > 2) choices corresponding to m candidates (denoted as Cm). It is discussed in this part that one group of CV-based GHZ-like states could offer four choices (position-squeezed modes and momentum-squeezed modes are all utilized) for voting. Four situations where m may refer to 4t, 4t − 1, 4t − 2, 4t − 3 (t = 1,2,3,…) should be considered. The first situation: m = 4t is discussed only, since the differences for the four situations exist in the employing of the position or momentum of the two modes, and the analysis of these four situations are almost the same. Also, n voters and the ballot agency are involved in the ballot. The voting process presented in Fig.
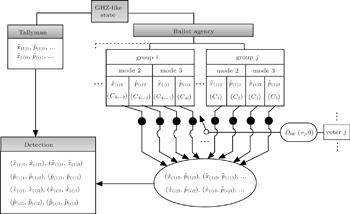 | Fig. 3. Multi-valued ballot with the CV-based GHZ-like state, where j ∈ {1,2,3…,n}, i ∈ {1,2,3…,t}, α and β are arbitrary real numbers. |
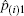
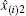
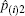
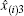
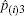

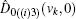
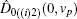
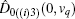

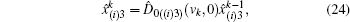
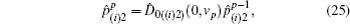




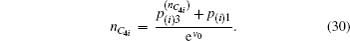
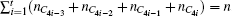
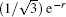
Besides, another case that a voter may give up voting should be considered. If a voter gives up voting while another voter votes twice, the cheating behavior cannot be detected with the previous method in Subsection 2.1. However, the problem could be solved by setting the option of giving up voting as the (m+1)-th choice. The exact number for the voters who give up voting can be obtained definitely.
Next, the security and efficiency of the improved protocols are discussed.
During the voting process, cheating behavior is unpopular. The two most possible cheating behaviors occurring in the voting phase can be discussed as follows.


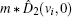

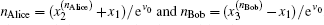
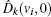
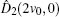

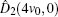



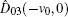
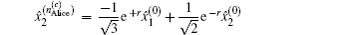
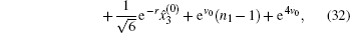
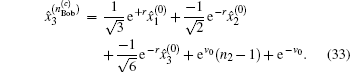

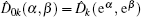
The security of the proposed protocols is proved by analyzing the performance for detecting the two most possible cheating behaviors above. With the modified operator and CV-based GHZ-like states, cheating behaviors can be prohibited effectively.
For the purpose of ensuring the security and confidentiality, the CV-based GHZ-like states are utilized as quantum resources in our proposed protocols, which contributes to deriving an effective voting scheme with high utilization of quantum states as well.
In the CV-based multi-valued ballot protocol, t (t ≥ 1) groups of CV-based GHZ-like states are employed, and each group can provide four modes (the position-squeezed and momentum-squeezed mode of mode 2 and those of mode 3) to serve as voting modes. It is merely required to prepare two groups of CV-based GHZ-like states if there are eight candidates. Generally, it is defined that 4t candidates could require t groups of CV-based GHZ-like states in our protocols. The comparison of the quantities that CV-based GHZ-like states consumed in our protocols and EPR states consumed in Jiang’s protocol is shown in Table
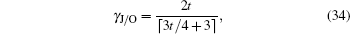
| Table 1. Comparison of the quantities that CV-based GHZ-like states and EPR states consumed in our protocols and Jiang’s protocol[25] respectively during the voting process. “CN”, “QCG”, “QCE”, and “QCM” are abbreviated for “candidates’ number”, “quantities of consumed GHZ-like states”, “quantities of consumed EPR states”, and “quantities of consumed quantum modes”, respectively. . |
Two branches of anonymous voting, CV-based binary-valued ballot and CV-based multi-valued ballot, are proposed in this paper, in which CV-based GHZ-like states are utilized to complete the voting process with less waste of consumed states. Each voter’s anonymity and privacy can be guaranteed by the entanglement of CV-based GHZ-like states. The improved displacement operation 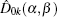
| 1 | |
| 2 | |
| 3 | |
| 4 | |
| 5 | |
| 6 | |
| 7 | |
| 8 | |
| 9 | |
| 10 | |
| 11 | |
| 12 | |
| 13 | |
| 14 | |
| 15 | |
| 16 | |
| 17 | |
| 18 | |
| 19 | |
| 20 | |
| 21 | |
| 22 | |
| 23 | |
| 24 | |
| 25 | |
| 26 | |
| 27 | |
| 28 | |
| 29 | |
| 30 | |
| 31 |



