† Corresponding author. E-mail:
Project supported by the National Natural Science Foundation of China (Grant No. 11304397).
Passive decoy-state quantum key distribution systems, proven to be more desirable than active ones in some scenarios, also have the problem of device imperfections like finite-length keys. In this paper, based on the WCP source which can be used for the passive decoy-state method, we obtain the expressions of single-photon error rates, single-photon counts, and phase error rates. According to the information of smooth min-entropy, we calculate the key generation rate under the condition of finite-length key. Key generation rates with different numbers of pulses are compared by numerical simulations. From the results, it can be seen that the passive decoy-state method can have good results if the total number of pulses reaches 10 10 . We also simulate the passive decoy-state method with different probabilities of choosing a pulse for parameter estimation when the number of pulses is fixed.
Quantum key distribution (QKD) [ 1 , 2 ] allows two legitimate parties, Alice and Bob, to establish a common and secret key when the channel is accessible to an eavesdropper, Eve. Since the best-known Bennett–Brassard 1984 (BB84) protocol [ 1 ] was put forward, QKD has attracted more and more attention all over the world, due to its unconditional security based on the fundamental laws of physics: no-cloning theorem and the uncertainty principle. [ 3 ]
QKD has been developed well both theoretically and experimentally [ 4 – 11 ] in recent years. However, people have come across all sorts of difficulties in a real situation. [ 12 ] Though an ideal QKD system is unconditional security, in fact the necessary assumptions that ideal QKD system need are not easy to be satisfied. These practical factors such as finite resources and imperfections of setups, will undoubtedly threaten the security of the real QKD system, and Eve can take advantage of the leaks to attack the system. To prevent the attacks, many countermeasures have been applied. One of them is to employ the decoy-state method [ 13 – 17 ] which introduces two or more decoy states to confuse Eve so that she cannot distinguish the signal state from the decoy states. Another important approach is the notion of device-independent QKD (DI-QKD). [ 18 – 28 ] What is more, people make works to characterize the effects of the real imperfect factors on the security of QKD system in a mathematical way to give a security proof. [ 12 ]
The finite-length key is an important practical factor which needs to be solved in a real QKD system. Under ideal conditions, the data transformed between Alice and Bob are infinite, and QKD can generate the final secure key from the infinite data. However, in practice, the data above cannot be infinite. It may cause statistical fluctuations on relating parameters. When we regard the finite-length keys, we should reconsider the security bound in the asymptotic regime.
In recent years, many significant advances have been achieved. [ 29 – 32 ] In 2008, Scarani and Renner [ 33 ] creatively presented the smooth min-entropy theory to obtain the security bound for practical BB84 with finite-length keys. Then Tan and Cai [ 34 , 35 ] studied the passive decoy-state with finite-length keys and demonstrated its unconditional security. Their works show that the practical decoy state can reach the asymptotic limit, where the resource is large enough but not infinite. In 2014, Zhou et al. [ 36 ] presented a concise and stringent formula to calculate the key generation rate for QKD using SPDCSs with finite-length keys.
In this paper, we first briefly introduce the decoy state protocol. We focus on the passive decoy-state protocol and the differences from the active decoy-state protocol. Then we introduce the phase-randomized WCP source used for the passive decoy-state method. With this source, we describe the passive decoy-state protocol without considering the finite-length key.
The rest of this paper is organized as follows. In Sections 2 and 3, we briefly introduce decoy state protocol and the WCP source which has been transformed for the passive decoy-state method, respectively. Next, in Section 4, we consider the passive decoy-state method with the infinite-length key. The affect of the finite-length key on the passive decoy-state method is analyzed in detail in Section 5. The numerical simulations of this section are shown in Section 6. Finally, Section 7 concludes the paper with a summary.
In Section 1, we presented the fact that the necessary assumptions an ideal QKD system needs are not easy to satisfy. In the original proposal of the BB84 protocol, a single-photon source is necessary, but the single-photon source is still unavailable with current technology. Usually, a weak coherent pulse (WCP) source is used instead and many WCP-based experiments have been done since the first QKD experiment was carried out. [ 37 ] However, due to the multiphoton pulse sent from the WCP source, the QKD system will suffer from photon-number splitting (PNS) attack. [ 38 , 39 ] To protect the QKD system from PNS attack, one can use the decoy-state method which could closely reach the performance of single-photon sources. Actually, the method that Alice prepares the decoy state actively can be called the active decoy-state method. Similarly, the active decoy-state method also suffers from some practical factors. Because of imperfect experiments and channels, it may bring in some side channel information that Eve can take advantage of having an attack. For the real active (regular) decoy-state experiments, it is more difficult to verify the assumption that Eve cannot distinguish decoy and signal states. [ 40 ]
However, the passive decoy-state method [ 41 , 42 ] can reduce the side channel information in the decoy-state preparation procedure. Different from the active decoy-state method which actively changes the intensity of the laser pulses randomly, the passive decoy-state method only has one intensity pulse. The key point to distinguish in the passive decoy-state method is clicking or no clicking for Alice’s detector.
The common point between the passive decoy state and the active decoy state is that the yields and the error rates of the same photon-number states of the signal states and the decoy states shall be equal to each other, which means [ 14 ]
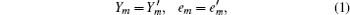
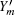
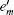
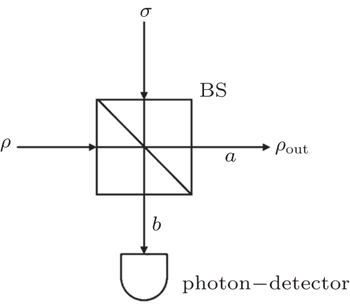
Due to the characters of the WCP source itself, it cannot be used for the passive decoy-state method directly. Curty et al. [ 43 , 44 ] have adjusted the WCP source to make it output two Fock diagonal states, so that it can be used for the passive decoy-state method. The fundamental setups are shown in Fig.
In Fig.
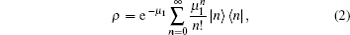

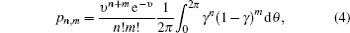
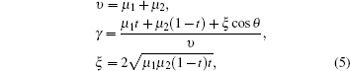
Whenever the sender, Alice, does not care about the result of the measurement in mode b , the probability of having n photons in mode a can be written as
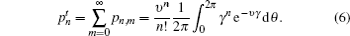
For Alice’s detector, the joint probability of having n photons in mode a and no click in the threshold detector now has the form
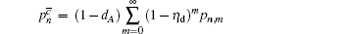
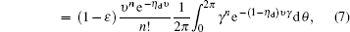
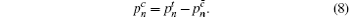
In this paper, we define that c denotes “click” of the detector while c̄ denotes “no click”. We also denote the signals that cause a click of Alice’s detector as signal states. The ones that cause no click of Alice’s detector are decoy states.
In this section, we discuss the ideal passive decoy-state method. In the passive decoy-state method, two-mode states are a prerequisite as shown in Fig.
In Section 3, we have mentioned the parameter 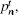
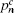
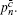
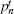
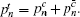
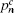
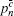
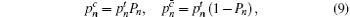
According to the passive decoy-state method, the counting rates and the error rates of the n -photon states of the signal states and the decoy states are
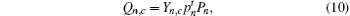
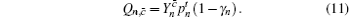
From Eqs. ( 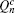
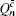
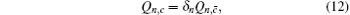
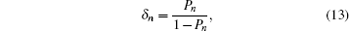
The overall gain of Alice’s detector producing a click is Q c and no click is Q c̄ . They can be expressed by
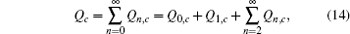
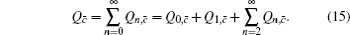
In order to calculate the lower bound of Q 1, c̄ , we eliminate 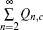
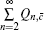
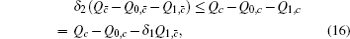
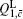
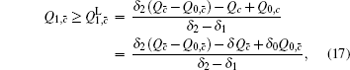
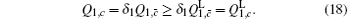
Next, we will calculate the upper bound of error rates of the signal state and the decoy state. According to the quantum bit error rate (QBER),
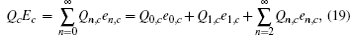
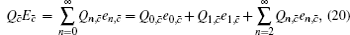
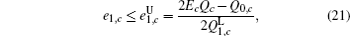
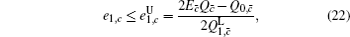
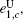
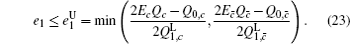
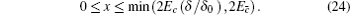
Finally, taking the parameters above into the GLLP formula, one can obtain the following final key rate: [ 42 ]
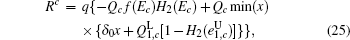
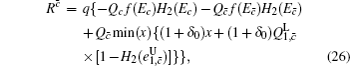
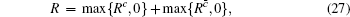
Because of the finite-size data sets in real-life condition, parameters have various fluctuations. In this paper, we mainly consider the influence of the finite-size data on the single-photon yield and single-photon error rate. Here, we will use smooth min-entropy to study the passive decoy-state method with the finite-length key.
Firstly, we introduce some related definitions.
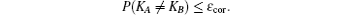
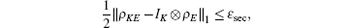
For QKD protocol, correctness can be regarded as the maximal probability of error-correction failure. Secrecy implies the probability that the final key is equal to the key without Eve is no less than 1 – ε sec .
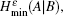
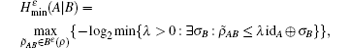
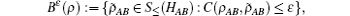
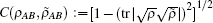
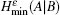
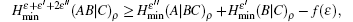

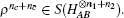
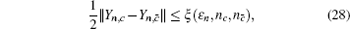
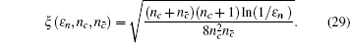
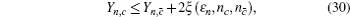
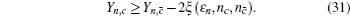
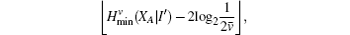
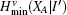
Due to the influence of the finite-length key, the yields of the signal state and decoy state are no longer equal to each other, that is
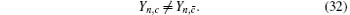
Next, we can calculate the lower bound of the single-photon counting rates for the decoy state and signal state.
Similar to that in Section 4, we need to eliminate the elements of n ≥ 2 in Eq. (
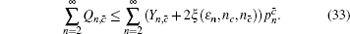
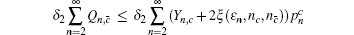
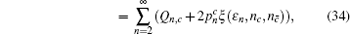
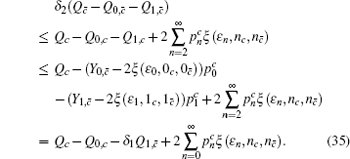
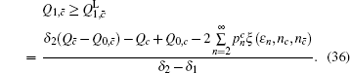
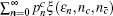
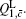
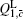
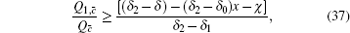
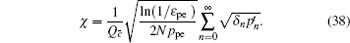
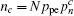
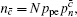
Similarly, we can obtain the lower bound of Q 1, c according to inequalities (
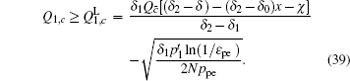
Next, we will recalculate the upper bounds of e 1, c and e 1, c̄ .
Due to e 1, c ≠ e 1, c̄ , we can obtain two sample upper bounds of e 1, c and e 1, c̄ from Eqs. (
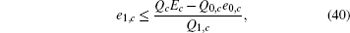
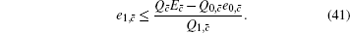
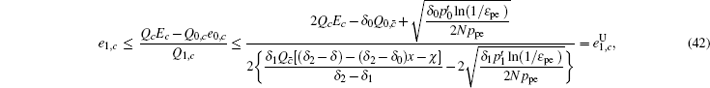
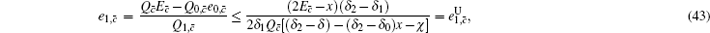
To calculate the final key generation rate, Lemma 2 is usually used to obtain the length of the secret key firstly. In this paper, we set
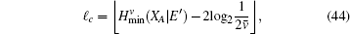
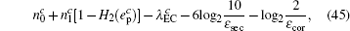
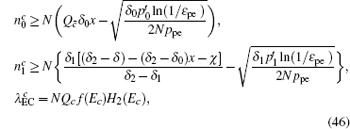
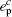
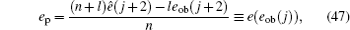
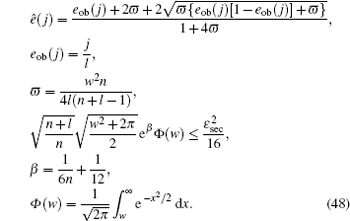
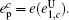
Combined with the lower bounds of Q 1, c , Q 1, c̄ and the upper bounds of e 1, c , e 1, c̄ , equation (45) can be expressed by
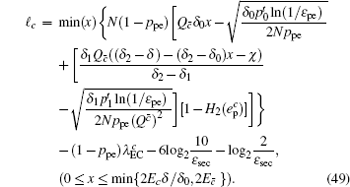
According to the definition of the key generation rate, it is the fraction of the length of secret key and the number of total pulses, i.e., R = ℓ / N . One can obtain the final key generation rate as
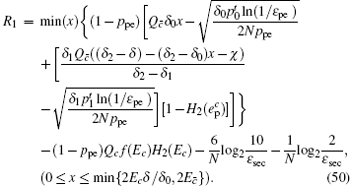
However, it has been noted that the decoy state also has contributions to the key generation rate in the passive decoy-state method, so equation (44) is not suitable here. Recently, reference [ 36 ] considered the key generation rate of the decoy state of the passive decoy-state method and gave the length of the secret key in this situation as
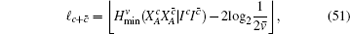
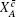
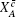
The final secret key can be said to be ε sec -secret if its length ℓ c + c̄ is chosen by
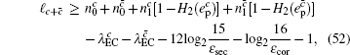
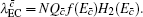
Now, combined with the lower bounds of the single-photon counting rate and the upper bounds of the error rate that have been calculated above, one can obtain the length of the final secret key as
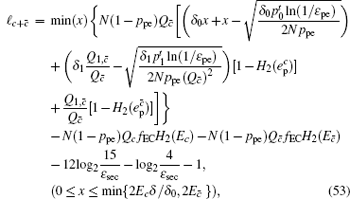
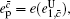
According to the definition of the key generation rate, the final key generation rate under this condition is
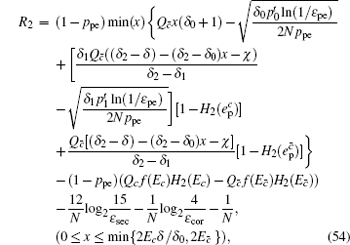
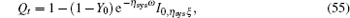
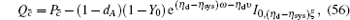




Finally, the length of the final secret key is
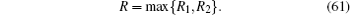
In this section, we will take some numerical simulations to show how the finite-length key influences the final key generation rate of the passive decoy-state method. In the scenario we considered, the yields Y n can be expressed by
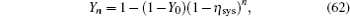
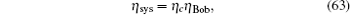
The parameters 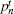
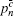
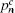
| Table 1. Experimental QKD parameters. . |
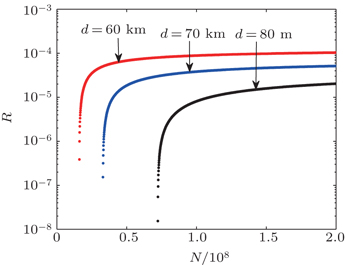
Figure
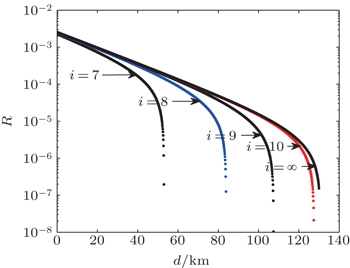 | Fig. 2. Key generation rate R versus transmission distance d with different N ( N = 10 i , i = 7, 8, 9, 10, ∞). |
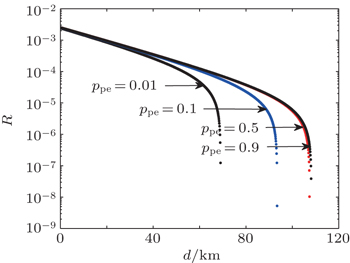
Figure
Finally, we analyse the relationship between R and d with different p pe which means the probability of choosing a pulse as the sample bits used for parameter estimation when N is fixed. Figure
In summary, we introduce the decoy state method and analyze the phase-randomized WCP source that can be used in passive decoy-state protocol. Then, we study the passive decoy-state method using the WCP source with an infinite-length key. After recalculating the phase error rate, counting rate, and error rate of the single photon state, we obtain the length of the secret key considering both the signal state and the decoy state in the passive decoy-state method. According to the results of numerical simulations, we find that the finite-length key influences the real QKD system. It can affect the key generation rate and the transmission distance. The key generation rate and the extreme transmission distance become larger with the increase of the number of total pulses. When the number is larger than 10 10 , the passive decoy-state QKD with the WCP source will perform well. Meanwhile, we study the relationship between the key generation rate and the probability of choosing a pulse as the sample bits used for parameter estimation. It can help us to select the optimal value to make sure that the passive decoy-state method in this paper will be implemented best. Our work can help QKD experimentalists to improve the performance and provide references about how to choose the data-size.
| 1 | |
| 2 | |
| 3 | |
| 4 | |
| 5 | |
| 6 | |
| 7 | |
| 8 | |
| 9 | |
| 10 | |
| 11 | |
| 12 | |
| 13 | |
| 14 | |
| 15 | |
| 16 | |
| 17 | |
| 18 | |
| 19 | |
| 20 | |
| 21 | |
| 22 | |
| 23 | |
| 24 | |
| 25 | |
| 26 | |
| 27 | |
| 28 | |
| 29 | |
| 30 | |
| 31 | |
| 32 | |
| 33 | |
| 34 | |
| 35 | |
| 36 | |
| 37 | |
| 38 | |
| 39 | |
| 40 | |
| 41 | |
| 42 | |
| 43 | |
| 44 | |
| 45 | |
| 46 | |
| 47 | |
| 48 | |
| 49 | |
| 50 |