Controlled mutual quantum entity authentication using entanglement swapping
Controlled mutual quantum entity authentication using entanglement swapping |
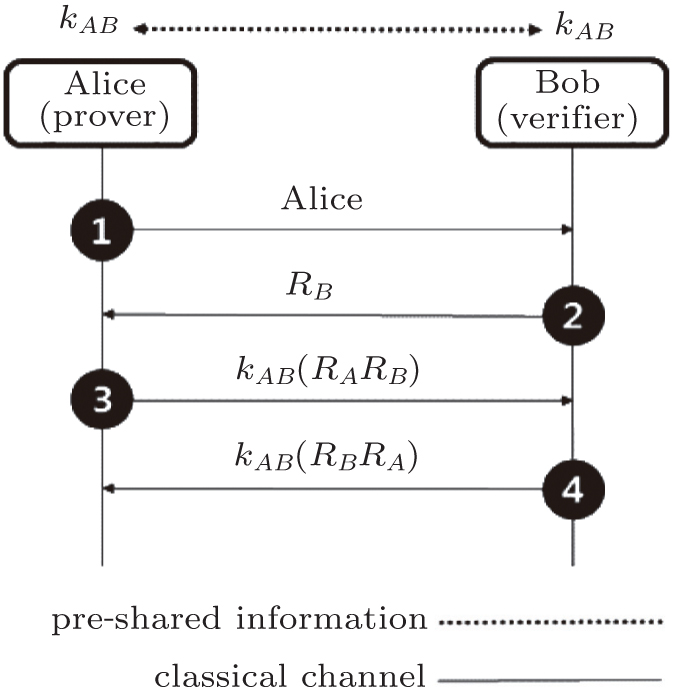
| Bidirectional challenge-response authentication using a symmetric-key cipher.[ 1 – 4 ] As in Fig. 1(a) , Alice and Bob, respectively, check the nonce (random number) R A and R B , and mutually verify the unidirectional authentication using the nonce. In phase 3, Alice generates encrypted random numbers k AB ( R A R B ) and responds to Bob’s challenge, while simultaneously challenging Bob to identification. In phase 4, Bob generates k AB ( R B R A ) and responds to Alice’s challenge, thereby completing the certification process. |
 |