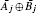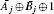†Corresponding author. E-mail: huangwei096505@aliyun.com
*Project supported by the National Natural Science Foundation of China (Grant Nos. 61272057, 61170270, and 61309029), Beijing Higher Education Young Elite Teacher Project, China (Grant Nos. YETP0475 and YETP0477), and BUPT Excellent Ph.D. Students Foundation, China (Grant No. CX201441).
A multi-user quantum key distribution protocol is proposed with single particles and the collective eavesdropping detection strategy on a star network. By utilizing this protocol, any two users of the network can accomplish quantum key distribution with the help of a serving center. Due to the utilization of the collective eavesdropping detection strategy, the users of the protocol just need to have the ability of performing certain unitary operations. Furthermore, we present three fault-tolerant versions of the proposed protocol, which can combat with the errors over different collective-noise channels. The security of all the proposed protocols is guaranteed by the theorems on quantum operation discrimination.
Over the last two decades, the principles of quantum mechanics have been widely applied in the field of information, which has promoted rapid developments of quantum cryptography and quantum computation. Since the pioneering work of Bennett and Brassard in 1984, [1] quantum cryptography has attracted a great deal of attention and become one of the most promising applications of quantum information processing. There are several remarkable branches of quantum cryptography, including quantum key distribution (QKD), [1– 14] quantum secure direct communication (QSDC), [15– 22] quantum secret sharing (QSS), [23– 28] and secure multi-party computation (SMC).[29– 33] The multi-party quantum cryptographic protocols (MQCPs) which involve at least three participants, such as quantum private comparison (QPC) protocols and QSS protocols, are more complicated than the two-party ones. Therefore, more attention is needed in the research of MQCPs.
In most MQCPs, the quantum information carriers need to be transmitted more than once, and usually eavesdropping detection should be taken in every step of the transmission. However, this detection strategy, which is called step-by-step detection, always makes the protocols inefficient and complicated. First, it is known that the security analysis of the quantum cryptographic protocols is based on the error rate analysis with theories in statistics. Hence, the proportion of the detection states (i.e., states chosen for eavesdropping detection) in the transmitted states should not be too small. If the detection is taken in every step of the transmission of the quantum information carriers, a lot of states will be used for checking eavesdropping and the qubit efficiency of the corresponding protocol will decrease with the increase of the number of detections. Second, detecting in every step of the transmission usually requires all the participants in such a protocol to be equipped with many quantum devices, e.g., the quantum state measurement machine, the quantum state generation machine, and the quantum storage machine. However, based on the current technology, these quantum devices are still expensive because of their construction difficulties. As a consequence, it is uneconomical to require that every participant is equipped with most of these quantum devices. Apparently, an MQCP would be more efficient and easier to realize if the detection is taken only once in the whole procedure of the protocol. Fortunately, if an MQCP makes use of the collective eavesdropping detection strategy, it could meet such a requirement. Collective detection is an efficient and useful eavesdropping detection strategy for MQCPs. On one hand, in an MQCP which employs the collective detection strategy, the detection needs to be taken only once after the whole transmission procedure of the quantum information carriers. On the other hand, this strategy can also reduce the hardware requirement for the implementation of the protocol, since all the users (except for the center who is responsible for preparing and measuring states) only need to perform certain unitary operations in the whole executing procedure of the protocol. To date, much attention has been focused on the collective detection strategy and a lot of MQCPs have been proposed by utilizing it (for simplicity, we will call the MQCP which uses collective detection MQCP-CD), [34– 41] including QKD, [34– 36] QPC, [37] QSS, [38– 40] and QSQC.[41]
In an MQCP-CD, all the users (except for the center) just need to be capable of performing certain unitary operations. Therefore, the operations performed by them are very important to the security of the protocol. In this paper, a method for constructing the operations needed in the MQCP-CD is presented. It is a method that can be used to construct the unitary operations which meet the security requirements of the MQCP-CD with different kinds of quantum states, such as single photons, EPR pairs, and GHZ states. Based on this method, we present a multi-user quantum key distribution (MQKD) protocol with collective detection and single particles. Our protocol is presented on a star network where any two of the involved users can execute quantum key distribution with the help of a serving center. There are several merits of this protocol. First, to establish a random key by employing this protocol, two users only need to be capable of performing certain unitary operations. Second, none of the participants (all the users and the center) in our protocol needs to be equipped with a quantum storage machine. As storing quantum qubits is still a very difficult task in reality, our protocol is more feasible than the ones[34– 36] in which the quantum storage machine is required. In addition, our protocol can resist various kinds of attacks from both outside eavesdroppers and a dishonest center.
Actually, quantum states transmitted in a channel interact with the environment uncontrollably, which will introduce noise into the communication and influence both the correctness and efficiency of the communication. If the variation of the noise is slower than the time delay between the quantum states transmitted inside a time window, the states will be affected by the same noise. This kind of noise is called collective noise.[42, 43] To combat the errors caused by the collective noise, we further introduce three fault-tolerant versions of our protocol with the idea of decoherence-free subspace (DFS), [44– 54] which can resist the collective-dephasing noise, the collective-rotation noise, and all kinds of unitary collective noise, respectively.
The remainder of this paper is organized as follows. The next section presents our method for constructing the required unitary operations in the MQCP-CD. In Section 3, our MQKD protocol and its three fault-tolerant versions, which utilize the collective detection and block transmission, are proposed in detail. The block transmission, which was proposed firstly by Long et al. in Ref. [15], is one of the most important techniques for transmitting quantum states in quantum information processing. In block transmission, the quantum states are ordered and transmitted in blocks, and the eavesdropping detection is also executed on the blocks. In Section 4, the security of our proposed protocols is analyzed by using the theorems on quantum operation discrimination. Finally, a discussion as well as a short conclusion is given in Section 5.
Thus far, many MQCP-CDs[34, 35, 55– 57] have been attacked since the unitary operations used in those protocols can be discriminated unambiguously (by a single use) if an eavesdropper utilizes some special attack strategies, such as dense-coding attack[35] and fake-signal attack.[55] It is just because there is still no effective method for constructing the required unitary operations that some improper ones were used in those protocols. In this section, we introduce a method for constructing the required unitary operations which can be used in designing a secure MQCP-CD. This method can be used to construct the required unitary operations with different kinds of quantum states. Afterwards, we prove the correctness of this method based on the conclusions on quantum operation discrimination.
Before presenting the method for constructing the required operations, we first briefly introduce the basic principle of the MQCP-CD.[34– 41] In this kind of protocol, two mutually unbiased bases, which are denoted as {| a⟩ , | b⟩ } and {| c⟩ , | d⟩ }, are required for secure communication. Here, ⟨ a| b⟩ = ⟨ c| d⟩ = 0, and | ⟨ a| c⟩ | 2 = | ⟨ a| d⟩ | 2 = | ⟨ b| c⟩ | 2 = | ⟨ b| d⟩ | 2 = 1/2. Besides, there should be a center who is responsible for generating and measuring the quantum states. The center first generates a sequence of states in the two bases and sends them to the first user. Then the first user processes the received states by performing four unitary operations according to his secret binary string and controlling binary string. After the operations, the first user sends the processed sequence to the next user. The following users execute procedures just like the first user one by one. When the last user finishes his operations, he sends the sequence back to the center. After the center receives the sequence, the users randomly choose some states to check eavesdropping with the information of the unitary operations performed on the chosen states and the corresponding measurement outcomes provided by the center. If the whole transmitting procedure is secure, the remaining states (or measurement outcomes) can be used to realize the main function of the protocol.
Concretely, when a user receives a sequence of quantum states, he first encodes his secret string by performing the operation I (identity operator)/U (encoding operation) on each of the received states if the corresponding bit of the secret string is 0/1. The effect of the unitary operation U is flipping a state in the same MB, i.e., U| a⟩ = α | b⟩ , U| b⟩ = β | a⟩ , U| c⟩ = γ | d⟩ , and U| d⟩ = δ | c⟩ . Here α , β , γ , and δ are global phase factors which can be ignored. After that, he disturbs the encoded states by performing the operation I/C (controlling operator) on each of these states if the corresponding bit in his controlling string is 0/1. The effect of the unitary operation C is flipping each one of the four states in {| a⟩ , | b⟩ , | c⟩ , | d⟩ } from one basis to the other basis. When a user encodes his secret string on the received states, each of the bits in the secret string and the controlling string will be used only once. If an eavesdropper wants to obtain some information of a bit in the secret string without leaving a trace in the eavesdropping detection, he should have the ability of discriminating between the four unitary operations I, U, C, and UC unambiguously with only one opportunity (i.e., under the condition that the device can be accessed only once). Therefore, one of the key steps in designing a secure MQCP-CD is to find appropriate unitary operations U and C which make I, U, C, and UC impossible to be discriminated unambiguously with a single use.
Now we give the method for constructing the required unitary operations. Suppose V is a d-dimensional Hilbert space. By employing the Gram– Schmidt procedure, it is easy to construct an orthonormal basis of V, {| 0′ ⟩ , … , | (d− 1)′ ⟩ }. It can be easily proved that {| 0′ ⟩ , | 1′ ⟩ } and {| + ′ ⟩ , | − ′ ⟩ } are two mutually unbiased bases of a 2-dimensional subspace, where
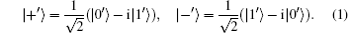
Then the encoding operation is chosen in the form of

where part M should meet the following two conditions. First, M should be in a proper form to make U be a unitary operation, i.e., U† U = UU† = I. Second, M should be orthogonal to both | 0′ ⟩ and | 1′ ⟩ . It can be easily verified that the operation U could flip each one of the states in {| 0′ ⟩ , | 1′ ⟩ , | + ′ ⟩ , | − ′ ⟩ } in its own basis when M is in the required form. There are many feasible choices for the form of M, such as M = | 2′ ⟩ ⟨ 2′ | + · · · + | (d − 1)′ ⟩ ⟨ (d − 1)′ | and M = | 2′ ⟩ ⟨ 3′ | + | 3′ ⟩ ⟨ 4′ | + · · · + | (d − 1)′ ⟩ ⟨ 2′ | . After getting the encoding operation U, we choose one of the square roots of U as the controlling operation, which could flip each one of the states in {| 0′ ⟩ , | 1′ ⟩ , | + ′ ⟩ , | − ′ ⟩ } from one basis to the other basis, i.e., 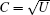
Herein we demonstrate that the four unitary operations I, U, C, and UC cannot be discriminated unambiguously with a single use if U and C are constructed by our method. Before giving the proof, we first introduce an important theorem on quantum operation discrimination.
Theorem 1[58] Under the condition that the device can be accessed only once, the minimum error probability to discriminate two unitary operations U1 and U2 is
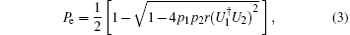
where 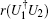
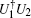
Corollary 1 Under the condition that the device can be accessed only once, two unitary operations U1 and U2 can be discriminated unambiguously if and only if 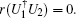
As defined in the presented method, 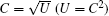
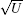
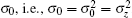
As shown above, all the eigenvalues of the operator 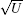
Till now, we have proved that the four unitary operations I, U, C, and UC constructed by our method cannot be discriminated unambiguously under the condition that the device can be accessed only once. Utilizing this method, we can construct the required unitary operations for designing a secure MQCP-CD with different kinds of quantum states.
If someone wants to design an MQCP-CD using a certain kind of quantum state in his favor, one of the most important things he should do first is to find the corresponding encoding operation U and controlling operation C which satisfy the security requirement of the MQCP-CD. Obviously, the method we just proposed can be used to construct such unitary operations. For example, if he wants to design an MQCP-CD with single photons, a natural choice for one of the two bases could be {| 0⟩ , | 1⟩ }. By employing our method, the other basis could be chosen as {| + ⟩ , | − ⟩ }, where 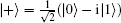
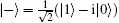
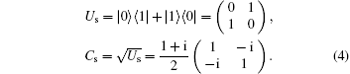
It can be easily verified that {| 0⟩ , | 1⟩ } and {| + ⟩ , | − ⟩ } form two mutually unbiased bases. The effect of the operations Us and Cs on the four states can be illustrated as
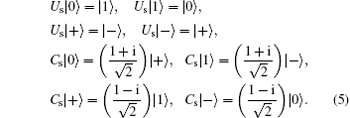
Utilizing the two bases and two operations (Us and Cs) given above, one can design different kinds of MQCP-CDs (QSS, QPC, etc.) with single photons. Evidently, there are still some other choices for the two operations if other single particles are chosen to be the quantum information carriers. To date, in order to improve the qubit efficiency or reduce the hardware requirement, some MQCP-CDs [34– 41] have been proposed with single photons. Unfortunately, all of those protocols need to store the quantum qubits, which is still a difficult task in reality. To make use of the collective detection under the current techniques, we present a more feasible MQKD protocol without employing a quantum storage machine in the next section. More importantly, we also enhance the proposed protocol to be immune to the errors over different collective-noise channels based on the above method.
In this section, we present an MQKD protocol by employing single particles and the collective detection on a star network (see Fig. 2). In this protocol, there is a center who is responsible for generating and measuring quantum states. With the help of the center, any two users involved in the network can securely establish a random key just by performing unitary operations on the states transmitted to them. If user i wants to share a random key with user j, they can encode their random binary strings into the states produced by the center, and then they are able to deduce a random key with the measurement outcomes published by the center, where 1 ≤ i, j ≤ n. In this circumstance, users i and j only need to hide their secrets in the transmitted states with proper unitary operations. In the network, we assume that any two of the participants (the center and all the users) can transmit quantum states between them. Similar to most of the previous quantum cryptographic protocols, the classical channels involved in this protocol are supposed to be authenticated. Compared with the existing MQKD
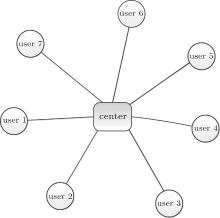 | Fig. 2. A simple illustration of the MQKD with seven users on a star network. In this network, any two of the seven users can establish a shared secret key only with unitary operations. |
protocols which also utilize the collective detection, [34– 36] our protocol has the following two advantages. First, it is secure against attacks from both outside eavesdroppers and a dishonest center. Second, it does not need a quantum storage machine, which indicates that our protocol is more feasible in practice under current techniques. By utilizing the method presented in Section 2, two fault-tolerant versions of the proposed protocol are proposed by using two-qubit states: one is immune to the collective-dephasing noise, and the other is immune to the collective-rotation noise. Then we also present a more robust version of the protocol, which can resist all kinds of unitary collective noise by using four-qubit states.
If two users in the network, say Alice and Bob, want to share a random key, they can execute the MQKD protocol as described below (see also Fig. 3).
1) Alice generates two random binary strings of length 4n, which are denoted as A and A′ , respectively. Similarly, Bob generates two random binary strings of length 4n, which are denoted as B and B′ , respectively. After that, Alice informs the center that she wants to establish a random key with Bob.
2) The center receives Alice’ s request, prepares a sequence of 4n single particles which are all in the state | 0⟩ (denoted as sequence S), and sends it to Alice.
3) Once receiving S, Alice performs the unitary operations UAi and 
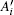
4) Upon receiving the sequence S1, Bob performs operations UBi and 
5) Once receiving S2, the center makes a measurement on each of the particles randomly in σ z-basis or σ y-basis, and then publishes the measurement outcome of each of the particles in S2, where σ z-basis = {| 0⟩ , | 1⟩ } and σ y-basis = {| + ⟩ , | − ⟩ }. According to the i-th measurement outcome announced by the center, Alice and Bob could learn which of the two bases was used to measure the i-th particle in S2. Concretely, if the measurement outcome is | 0⟩ or | 1⟩ (| + ⟩ or | − ⟩ ), the σ z-basis (σ y-basis) was used.
6) After the center announced the measurement outcomes of all the particles in S2, Alice and Bob publish A′ and B′ , respectively, where 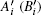
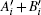



7) To check eavesdropping, Bob randomly chooses n positions in string C and requires Alice to tell him the corresponding bits in Ā . According to the information announced by Alice and Table 1, Bob checks whether the corresponding bits in C are in accordance with the theoretical values. If the error rate is higher than acceptable, they abort the results; otherwise, Bob can trust the transmission and deduce the rest n bits of Ā with the corresponding bits of C and 
Table 1. The relationship among the values of Ā j,   |
In this protocol, with the help of the center, any two of the involved users can establish a random key with only unitary operations. Although the qubit efficiency of our protocol is half of that of the protocols in Refs. [34]– [36], our protocol does not need to store quantum qubits. Hence, our protocol is more feasible with the current techniques. Besides, users should set up a filter and a beam splitter to prevent a Trojan horse attack and an invisible-photon attack.[61, 62]
Herein we introduce three fault-tolerant versions of the proposed MQKD protocol based on the method in Section 2 and the idea of DFS, which can be immune to the collective-dephasing noise, the collective-rotation noise, and all kinds of unitary collective noise, respectively.
The collective-dephasing noise[42, 45, 63] can be described as

where ϕ is the noise parameter and fluctuates with time. A logical qubit, which is composed of two physical qubits with antiparallel parity as
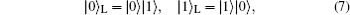
is immune to the collective-dephasing noise, as both qubits obtain the same phase factor eiϕ through this kind of channel. To communicate securely, at least two non-orthogonal measuring bases are required. According to the presented method, one basis could be {| 0⟩ L, | 0⟩ L}, and the other one is {| + ⟩ L, | − ⟩ L}, where

It is straightforward to verify that | ⟨ + | 0⟩ L| 2 = | ⟨ + | 1⟩ L| 2 = | ⟨ − | 0⟩ L| 2 = | ⟨ − | 1⟩ L| 2 = 1/2, which indicates that {| 0⟩ L, | 1⟩ L} and {| + ⟩ L, | − ⟩ L} form two mutually unbiased bases. Based on the method given in Section 2, we construct the following encoding operation Udp and controlling operation Cdp for our MQKD protocol which can resist the collective-dephasing noise:

The effect of the operations Udp and Cdp on the four states can be illustrated as
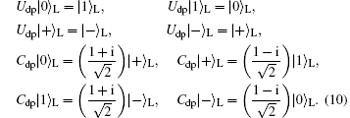
In this case, with the help of the center, any two of the involved users can establish a shared secret key over the collective-dephasing channel with the same steps of the protocol given in Subsection 3.1. Certainly, there are some differences between these two cases. First, the four states | 0⟩ , | 1⟩ , | + ⟩ , and | − ⟩ should be respectively replaced by | 0⟩ L, | 1⟩ L, | + ⟩ L, and | − ⟩ L. Second, the unitary operations Is, Us, and Cs should be substituted with 
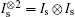
The collective-rotation noise[42, 45, 63] can be described as
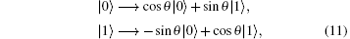
where θ is the parameter of noise which fluctuates with time. Two Bell states, 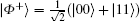
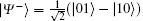
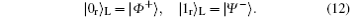
For secure communication, at least two non-orthogonal measuring bases are required. According to the presented method, one basis could be {| 0r⟩ L, | 0r⟩ L}, and the other one is {| + r⟩ L, | − r⟩ L}, where

It is easy to verify that | ⟨ r+ | 0r⟩ L| 2 = | ⟨ r+ | 1r⟩ L| 2 = | ⟨ r− | 0r⟩ L| 2 = | ⟨ r− | 1r⟩ L| 2 = 1/2, which indicates that {| 0r⟩ L, | 1r⟩ L} and {| + r⟩ L, | − r⟩ L} form two mutually unbiased bases. Using the method given in Section 2, we construct the encoding operation Ur and controlling operation Cr for the MQKD protocol over the collective-rotation channel as follows:
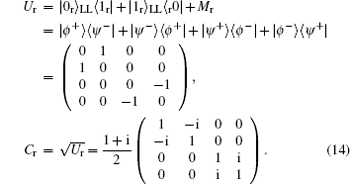
The effect of the operations Ur and Cr on the four states can be illustrated as
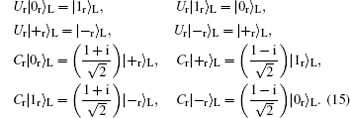
In this case, with the help of the center, any two of the involved users can establish a shared secret key over the collective-rotation channel with the same steps of the protocol presented in Subsection 3.1. Of course, there are some differences between these two cases. One difference is that the four states | 0⟩ , | 1⟩ , | + ⟩ , and | − ⟩ should be respectively replaced by | 0r⟩ L, | 1r⟩ L, | + r⟩ L, and | − r⟩ L. Another difference is that the unitary operations Is, Us, and Cs should be substituted with 
Decoherence-free (DF) states[43, 54] are a type of state which is changeless under any n-lateral unitary transformation (i.e., U⊗ n| ψ − ⟩ = | ψ − ⟩ , where U⊗ n = U⊗ · · · ⊗ U denotes the tensor product of n unitary transformations U). The amount of quantum information that a given N-qubit DFS is able to protect depends on the number of its qubits. If N is even, the DFS spanned by the eigenstates of the whole Hamiltonian of the qubit– bath system has dimension[43, 50]
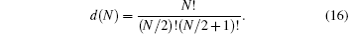
For N = 2, there exists only one DF state, the singlet state | ψ − ⟩ . For N = 4, the dimension of the DFS is 2. Hence, 4 qubits are sufficient to fully protect one arbitrary logical qubit from all kinds of unitary collective noise.[50] A natural choice for the orthogonal basis of the 4-qubit DFS is

To communicate securely, at least two non-orthogonal measuring bases are required. According to the presented method, One basis could be {
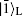

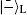
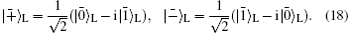
It can be easily verified that 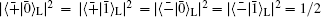

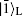

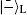

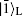
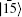
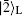
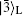
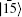
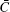
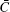

Here, we have many feasible choices for O, such as 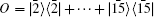
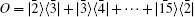
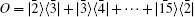
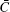
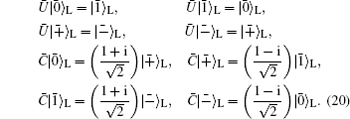
In this case, with the help of the center, any two of the involved users can establish a shared secret key over the channel with all kinds of collective-noise with the same steps described in the protocol proposed in Subsection 3.1. Certainly, there are some differences between these two cases. That is, the four states | 0⟩ , | 1⟩ , | + ⟩ , and | − ⟩ should be respectively substituted with 
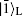

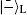
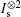
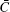

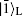

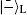
In this section, we analyze the security of the MQKD protocol with single particles. For the security of the ones over collective-noise channels, it can be analyzed in the same way. For clarity, we first consider the attacks from outside eavesdroppers. After that, we take into account the situation in which the center tries to eavesdrop the key.
Let us assume that Eve is an attacker who wants to eavesdrop the users’ secret key without being noticed in the eavesdropping detection. Eve could intercept the traveling particles sent to the receiver and replace them with the ones prepared by herself, [55] or she can entangle the travelling particles with additional states and try to extract information from these states.[64] Since the secret strings of the users are encoded on the travelling particles via the operations performed, the action to eavesdrop on the users’ secret strings is equivalent to discriminating between the operations that they have performed. For instance, if Eve wants to obtain the value of Ai (1 ≤ i ≤ 4n), she should know which one of the operations Is, Us, Cs, and UsCs Alice has performed on the corresponding particle. In other words, Eve should be capable of discriminating between the four unitary operations. Actually, the quantum operation discrimination has been well studied. In addition to Theorem 1 and Corollary 2, here we introduce another theorem.
Theorem 3[65] The quantum operations γ 1, … , γ n can be unambiguously discriminated by a single operation if and only if for any i = 1, 2, … , n, supp(γ i) ⊈ supp(Si), where supp(γ ) denotes the support of quantum operation γ and Si = {γ j : j ≠ i}.
In the proposed protocol with single particles, the unitary operations performed by both users (Alice and Bob) can be viewed as a whole with four unitary operations, i.e. Is, Us, Cs, and UsCs. Here, Is is the identity density operator on the two-dimensional Hilbert space and the operations Us and Cs are respectively the encoding operation and controlling operation defined in Eq. (4). It can be easily found that these operations satisfy 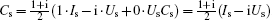
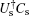
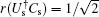
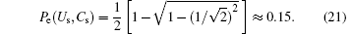
In the same way, we obtain the minimum error probability Pe(Is, Cs) = Pe(Is, UsCs) = Pe(Us, UsCs) ≈ 0.15, which means that these operations cannot be discriminated unambiguously under the condition that the device can be accessed only once.
In the proposed protocol, the users’ secret strings are encoded in the operations they performed on the states. If Eve wants to obtain a bit of a user’ s secret string without leaving a trace in the eavesdropping detection, she should have the ability of unambiguously finding out which of Is, Us, Cs, and UsCs has been performed on the corresponding particle with only one opportunity. However, as we analyzed above, the four operations cannot be unambiguously discriminated under this condition. Consequently, well-known attacks, such as the intercept-resend attack, the measurement-resend attack, the entanglement-measure attack, and the dense-coding attack, from an outside eavesdropper will inevitably be found in the eavesdropping detection.
Furthermore, as for the two special attacks of two-way communication, i.e., the Trojan horse attack and the invisible-photon attack, the users and the center can make use of the methods in Refs. [61] and [62] to protect the proposed protocols. Hence, we omit a redundant description here.
It is known that an attack from a dishonest participant is more powerful than those from the outside eavesdroppers. On one hand, he knows parts of the legal information. On the other hand, he could tell lies in the executing procedure of the protocol to avoid being detected. Therefore, attacks from dishonest participants should be paid more attention. Such situations should also be considered in our protocol. First, in the case that the center has been corrupted by others, he may try to eavesdrop the random key shared between the users. Second, in some special situations, the center may be out of service and a person who has the ability of generating and measuring the quantum states may want to eavesdrop the key. That is, the one who is able to substitute the center may be dishonest. Now, we show that, if the users use the proposed protocol, a dishonest center cannot obtain the random key without leaving a trace in the eavesdropping detection,
Compared with the outside eavesdroppers, a dishonest center has the following two superiorities. First, he could replace the particles in S with whatever kind of states he wants. Second, he could modify the measurement outcomes which are announced in step 5. Nevertheless, he is still unable to obtain the key shared between the users without being noticed in the eavesdropping detection of our protocol. According to the analysis given above, no matter what kind of states the dishonest center has prepared in step 2, he is unable to unambiguously discriminate between the four unitary operations performed by the users under the condition that the device can be accessed only once. In other words, these four unitary operations cannot be precisely discriminated when they are performed on a single qubit or one qubit of any entangled state. That is to say, if the center utilizes a strategy to discriminate between these four operations, he will obtain an incorrect outcome with a non-negligible probability. In our protocol, the users will announce the controlling string A′ and B′ only after the center publishes the measurement outcomes of all the particles in S2. Also the bits utilized to check eavesdropping are randomly chosen by the users after the measurement outcomes are published. Since the dishonest center cannot precisely discriminate between the four unitary operations utilized in our protocol with only one opportunity, no matter what attack strategy he employs, once he obtains part of the useful information about the secret string, he will inevitably introduce errors into the eavesdropping detection and hence be noticed by the users.
Till now, we have analyzed the security of the MQKD protocol in Subsection 3.1 to show that it is secure against attacks from both the outside eavesdroppers and the dishonest center. For the fault-tolerant MQKD protocols against collective-dephasing noise, collective-rotation noise, and all kinds of unitary collective noise, we can show that they can be immune to all the present attacks in just the same way, since the operations in {I⊗ 2, Udp, Cdp, UdpCdp}/{I⊗ 2, Ur, Cr, UrCr}/{I⊗ 4, Ū , 
To combat the errors introduced by the collective-noise channel, Zhang has proposed a well-known fault-tolerant multiparty quantum secret sharing (MQSS) protocol.[28] It is easy to find that this MQSS protocol can also be used for MQKD. However, there are clear differences between this protocol and our protocol. First, by utilizing our protocol, two arbitrary users could establish a secret key with the help of the center, and then they could utilize this key for secure communication between each other. In this circumstance, the center is unable to obtain any useful information of the shared key. While by employing Zhang’ s protocol, a boss could establish a joint key with his agents. Only when all the agents collaborate can they deduce the joint key and then utilize this key for secure communication with the boss. Second, as there exists a serving center in our protocol, if two of the involved users want to establish a secret key, they only need to be capable of performing certain unitary operations. Nevertheless, in Zhang’ s protocol, if the boss wants to establish a joint key with his agents, the boss should be able to generate quantum states, and the agents should be capable of performing a certain unitary operation and measuring the quantum states. In addition, to establish a secret key, the quantum state sequence should be transmitted three times in our protocol, while the sequence in Zhang’ s protocol only needs to be transmitted twice.
In fact, with some minor modifications, the protocol proposed in Section 3 can also be used for secret sharing of a random key. Concretely, if we want this protocol to be used for QSS, the following modifications are needed. Firstly, in step 5, after the center finishes measuring all the received particles, he notifies the fact to Alice and Bob. Different to the original protocol, he no longer publishes the measurement outcomes. Secondly, in step 6, once receiving the center’ s notification, Alice and Bob publish Ā ′ and 

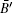



So far, we have shown that the protocol proposed in Section 3 can be used for three-party QSS with some minor modifications. Nevertheless, QSS has different security requirements from QKD. On one hand, the boss (i.e., the message sender) of a QSS protocol is honest. On the other hand, the agents (i.e., sharers) of a QSS protocol may be dishonest. That is to say, some dishonest agents may cooperate to attack the protocol and try to obtain the key without the help of other agents. According to the security analysis given in Section 4, it is not hard to find that the three-party QSS we just mentioned is secure. However, when the number of agents is more than two, many more threatening attacking strategies for QSS, such as the entanglement swapping attack, [39] should be considered. That is to say, to extend the above three-party protocol to an n-party one, some extra strategies should be employed for resisting these attacks. As the related strategies have been discussed somewhere else, [40] we do not focus on this issue here.
We introduce a method for constructing encoding operations and controlling operations, which are required in the MQCP-CD. Then by employing single particles and collective detection, we present an MQKD protocol on a star network without storing qubits, which can resist attacks from both outside eavesdroppers and a dishonest center. Based on the proposed method and the idea of DFS, we also introduce three fault-tolerant versions of the proposed protocol against collective-dephasing noise, collective-rotation noise, and all kinds of unitary collective noise.
Obviously, the presented method is useful as it can be used to construct the unitary operations required in the MQCP-CD with different kinds of quantum states. Compared with the existing MQCP-CDs, [34– 41] the protocols proposed in this paper have the following advantages. First, the proposed protocols are more feasible since they do not need to employ a quantum storage machine. Second, the proposed protocols can not only utilize the collective detection, but also be immune to the collective noise.
| 1 |
|
| 2 |
|
| 3 |
|
| 4 |
|
| 5 |
|
| 6 |
|
| 7 |
|
| 8 |
|
| 9 |
|
| 10 |
|
| 11 |
|
| 12 |
|
| 13 |
|
| 14 |
|
| 15 |
|
| 16 |
|
| 17 |
|
| 18 |
|
| 19 |
|
| 20 |
|
| 21 |
|
| 22 |
|
| 23 |
|
| 24 |
|
| 25 |
|
| 26 |
|
| 27 |
|
| 28 |
|
| 29 |
|
| 30 |
|
| 31 |
|
| 32 |
|
| 33 |
|
| 34 |
|
| 35 |
|
| 36 |
|
| 37 |
|
| 38 |
|
| 39 |
|
| 40 |
|
| 41 |
|
| 42 |
|
| 43 |
|
| 44 |
|
| 45 |
|
| 46 |
|
| 47 |
|
| 48 |
|
| 49 |
|
| 50 |
|
| 51 |
|
| 52 |
|
| 53 |
|
| 54 |
|
| 55 |
|
| 56 |
|
| 57 |
|
| 58 |
|
| 59 |
|
| 60 |
|
| 61 |
|
| 62 |
|
| 63 |
|
| 64 |
|
| 65 |
|